On April 18th, 2024, the NSA released updates and clarifications to their CNSA 2.0 (Commercial National Security Algorithm Suite 2.0) advisory. They did it in the form of an FAQ document (list of Frequently Asked Questions with Answers). The FAQ document was sent to the PQC Forum. This will be a multi-part series of postings about the questions and answers that we feel are most interesting and our reactions to them.
Q: Is there a quantum-resistant public-key algorithm that commercial vendors should adopt today?
A: NSA encourages vendors to use CNSA 2.0 approved hash-based signatures for software- and firmware-signing. NSA does not approve using pre-standardized or non-FIPS-validated CNSA 2.0 algorithms (even in hybrid modes) for NSS missions. However, NSA does recommend limited use of pre-standardized or non-FIPS-validated CNSA 2.0 algorithms and modules in research settings to prepare for the transition. NSA requests vendors begin preparing to implement CNSA 2.0 algorithms so they are primed to provide products soon after NIST completes standardization.
The NSA has spoken and they expect the industries from which they purchase to provide products that support the CNSA 2.0 Algorithm Suite upon standardization. That means DO NOT start when standardization is complete; start now.
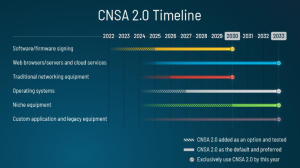
Note that for software/firmware signing it says you should already have it added and tested in your system! By next year, it should be the default and preferred. This means if you are not using LMS or XMSS in your boot loader then you are out of compliance with the CNSA 2.0 guidance. Checkout wolfBoot where we have already added support for the stateful hash-based signature schemes.
The NSA is also saying you need to be prepared with these algorithms already integrated into your products. Here at wolfSSL we have been saying the same message for years. You need to prepare for and understand the impacts that the larger keys, cipher text and signatures are going to have on your systems. Will these larger cryptographic artifacts require more memory resources? Will they slow down your transmissions? Will the answer to those questions cascade into new requirements and trade-offs? Now is the time to find the answers to those questions. Contact us at support@wolfSSL.com for benchmarking details.
If you haven’t already, go ahead and get started today. See Appendix G of our wolfSSL manual. Have further questions about getting started with CNSA 2.0 using wolfSSL, contact us at support@wolfSSL.com.
If you have questions about any of the above, please contact us at facts@wolfSSL.com or +1 425 245 8247.
Download wolfSSL Now


