Secure shell and file access for embedded systems
Unlike embedded Linux, or rich CPU-based systems, embedded systems running on a microcontroller rarely have support for file systems. Most often these devices run a firmware stored on a flash memory. However, more advanced microcontroller-based systems designed for edge computing offer the possibility to connect non-volatile storage devices, such as SD or MMC cards, non-volatile random-access memories and solid-state drives. In these cases, a bare-metal or RTOS-based system may benefit from a lightweight filesystem implementation, for standard read/write file access and directory management.
wolfSSH offers all the functionality of a SSH server and client in a compact and microcontroller friendly library. It implements SSH protocol v.2 with both password and public key based authentication. The SSH protocol is mostly famous for the secure shell feature on UNIX-like systems, used by administrators to control and automate process execution on remote systems. SSH however provides file transfer support via SCP, and more advanced file system access via SFTP.
wolfSSH implements SCP and SFTP for any embedded system, giving the possibility to customize the actions associated with remote filesystem access operations. A system with no filesystem support can still implement rudimentary operations on hardcoded file paths very easily, by defining use-case specific callbacks. Even without any actual filesystem, it is still possible to respond in a custom way to specific SFTP or SCP commands. A common usage, like the one shown in this FreeRTOS based example, is using SSH for remote secure firmware updates, uploading a new version of the firmware binary image as a file, e.g. via SCP. The embedded target does not actually have a file system but it receives the content of the remote file and stores it in a flash memory partition. Afterwards the application can delegate the secure bootloader, e.g. wolfBoot, to consider and process the update package for installation.
Customizing file I/O operations on non-POSIX systems can be done by defining WOLFSSH_USER_FILESYSTEM at compile time, and then assigning callbacks to I/O operations. A minimal set of calls for file management may include WFOPEN, WFCLOSE, WFWRITE, WFREAD, WFSEEK; although the full set of POSIX operations for subdirectory handling, file statistics, permission management and more are supported when running wolfSSH with SFTP on POSIX machines.
FatFS support
Using a lightweight FatFS implementation to store data in embedded systems has several advantages. Removable memory supports such as SD or MMC cards can be accessed offline by any PC host if required. On those microcontrollers supporting USB-OTG, internal block devices can appear as USB drives when the device is connected to a USB host.
ChaN’s FatFS (http://elm-chan.org/fsw/ff/00index_e.html) is a popular lightweight Open Source FAT implementation suitable for microcontrollers and distributed along with many BSP provided by hardware manufacturers, often as optional middleware package. FatFS exposes two interfaces: the API to be used by the application to access the filesystem, and the MAI (media access interface) to attach the I/O to any block-based storage system. Many embedded developers use this library even if there is no specific need for FAT format, simply because it is a complete filesystem implementation with a small footprint, provides a friendly, POSIX-inspired, well documented API, and it is easy to integrate with any physical storage medium.
Since version 1.4.7, wolfSSH offers a fully featured, pre-packaged integration with ChaN’s FatFS. By adding the compile-time option WOLFSSH_FATFS, wolfSSH will automatically map the file and directory callbacks to the corresponding function in the filesystem implementation. This means that there is no additional ‘glue code’ needed to integrate wolfSSH to provide remote secure file access and directory management.
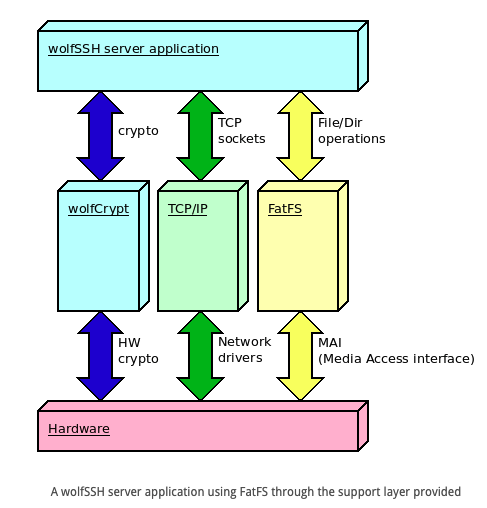
wolfSSH is the easiest way to implement SFTP and SCP on embedded targets. Adding wolfSSH to an existing connected system simply consists in providing send and recv callback functions to communicate over a TCP socket. For SFTP and SCP support a filesystem implementation, real or emulated, is required as well to respond to remote file and directory access requests, and wolfSSH offers a flexible interface to integrate with any filesystem implementation.
On those platforms where FatFS support is already included with the board support package or the real time operating system in use (e.g. ST CubeMX, NXP MCUXpresso), the integration of wolfSSH with the existing filesystem has now been made even easier. Setting up a thread in a RTOS with a SSH daemon providing SFTP access is a matter of a few lines of code, needed to set up SSH certificate, passwords and public keys. The target system will start accepting SSH connections and exchanging files from any compatible SFTP client.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.


