RECENT BLOG NEWS
wolfCrypt v4.0 FIPS with AES-NI
wolfSSL will be releasing wolfCrypt v4.0 FIPS with an expanded security boundary. We have added many algorithms to the boundary. We have also tested the code using AES-NI with Linux and Windows 10.
Intel added a set of instructions for accelerating AES processing including performing AES-GCM’s GHASH. Also available are accelerations to SHA-1, SHA-2, and SHA-3 hashing using the AVX instruction sets. Our implementations use algorithmically generated accelerated assembly code to get the job done fast.
For more information about wolfCrypt v4.0 FIPS, please send a message to fips@wolfssl.com. For more information about wolfSSL in general, including TLSv1.3 support, send a message to facts@wolfssl.com.
wolfCrypt v4.0 FIPS with Key Generation and RDSEED
wolfSSL will be releasing wolfCrypt v4.0 FIPS with an expanded security boundary. We have added many algorithms to the boundary, including Key Generation.
wolfCrypt v4.0 FIPS can generate keys for use with RSA and ECDSA signing. It can also do the perform the ECDHE and DHE key agreement schemes. We have also self-affirmed wolfCrypt for HKDF as a key-derivation function.
To use wolfCrypt key generation in a FIPS approved manner, you must build wolfCrypt with the Intel RDSEED feature enabled. If you do not have RDSEED available, you may use your own seeding method but it must meet the NIST SP 800-90B requirements.
For more information about wolfCrypt v4.0 FIPS, please send a message to fips@wolfssl.com. For more information about wolfSSL in general, including TLSv1.3 support, send a message to facts@wolfssl.com.
SCP with wolfSSH
We have been hard at work adding server support for SCP to wolfSSH and it will be available in the next release of wolfSSH, version 1.3.0.
If you have an embedded device and want to securely upload a new firmware image to it or download a log file with the convenience of a copy command, wolfSSH has you covered. Our server API keeps it simple to receive or send files when a client connects using ciphers found in our lightweight crypto library, wolfCrypt.
If you are interested in FIPS, wolfSSH compiles against wolfCrypt and can use the wolfCrypt FIPS library. For more information about FIPS, contact fips@wolfssl.com and we can discuss your requirements and FIPS testing.
For more information about wolfSSH please contact facts@wolfssl.com.
wolfSSL Release 3.15.0
wolfSSL is proud to announce release v3.15.0 of our wolfSSL embedded TLS library. Among the many additions are:
- Support for wolfCrypt FIPS on SGX
- Support for TLS 1.3 Draft versions
- Single Precision assembly code added for ARM and 64-bit ARM to enhance performance
- Improved performance for Single Precision maths on 32-bit
- Expanded OpenSSL compatibility layer
We have added Intel SGX as an operating environment for our wolfCrypt FIPS library. You can take advantage of running the wolfCrypt code in a secure enclave. For more information, contact fips@wolfssl.com.
With the finalization of TLS 1.3 on the horizon, we add incremental support for the drafts of the protocol. wolfSSL is current through draft 28 of the specification.
We are committed to supporting TLS 1.3 on embedded platforms, and we want to squeeze the most performance out of the chips for public key algorithms. After great success with the Intel assembly performance increases, we have added ARM assembly single-precision math support for RSA, ECC, and DHE.
To make porting existing projects over to wolfSSL, we have our OpenSSL compatibility layer. We are always expanding it. This release includes a large set of APIs to our support.
For more information, please contact facts@wolfssl.com. You can see the full change log in the source archive from our website at www.wolfssl.com or at our GitHub repository.
wolfSSL Intel SGX (#SGX) + FIPS 140-2 (#FIPS140)!
wolfSSL is pleased to announce the following addition to the wolfSSL FIPS certificate!
| Debian 8.7.0 | Intel ® Xeon® E3 Family with SGX support | Intel®x64 Server System R1304SP |
| Windows 10 Pro | Intel ® Core TM i5 with SGX support | Dell LatitudeTM 7480 |
The wolfCrypt FIPS validated cryptographic module has been validated while running inside an Intel SGX enclave and examples have been setup for both Linux and Windows environments.
Intel ® SGX (Software Guard Extensions) can be thought of as a black-box where no other application running on the same device can see inside regardless of privilege. From a security standpoint this means that even if a malicious actor were to gain complete control of a system including root privileges, that actor, no matter what they tried, would not be able to access data inside of this “black-box”.
An Intel enclave is a form of user-level Trusted Execution Environment (TEE) which can provide both storage and execution. Meaning one can store sensitive information inside and also move sensitive portions of a program or an entire application inside.
While testing, wolfSSL has placed both individual functions and entire applications inside the enclave. One of the wolfSSL examples shows a client inside the enclave with the only entry/exit points being “start_client”, “read”, and “write”. The client is pre-programmed with a peer to connect with and specific functionality. When “start_client” is invoked it connects to the peer using SSL/TLS and executes the pre-programmed tasks where the only data entering and leaving the enclave is the info being sent to and received from the peer. Other examples show placing a single cryptographic operation inside the enclave, passing in plain-text data and receiving back encrypted data masking execution of the cryptographic operations.
If you are working with SGX and need FIPS validated crypto running in an enclave contact us at fips@wolfssl.com or support@wolfssl.com with any questions. We would love the opportunity to field your questions and hear about your project!
Performance Comparison: TLS 1.3 in wolfSSL and OpenSSL
The performance of TLS 1.3 using wolfSSL has recently been discussed here in the blogs. While checking our performance a comparison was made with OpenSSL. An OpenSSL server using the latest TLS 1.3 implementation at the time was used with the wolfSSL client. The numbers showed that the recent Intel x86 64-bit assembly optimizations have been worth it.
Firstly, the performance of PSK without key exchange is mostly dependent on the speed of the hash algorithm. The results showed that the small block performance of SHA-256 in wolfSSL was the difference. On the platform tested, wolfSSL is about 22% faster than OpenSSL at hashing 256 bytes. The performance of wolfSSL in PSK non-KE handshakes was about 19% better than that of OpenSSL. The improved hashing performance partially helped other results.
The performance of other TLS 1.3 handshakes is dominated by the public key operations. Note that OpenSSL did not negotiate DH with TLS 1.3 in the version tested. When using PSK with a key exchange the public key operations the server performs are: ECDH key generation and secret calculation. While these operations in wolfSSL are only around 7% faster than OpenSSL on the platform the overall handshake performance was about 36% better. The overheads around performing the cryptographic operations in OpenSSL and slower hashing during the handshake made up the difference.
When using RSA certificates for server authentication, the cost of signing outweighs any other operation. On the platform RSA signing is about the same speed in wolfSSL as OpenSSL. The overall handshake speed was 10-15% better than OpenSSL due to overheads and hashing.
P-256 operations are faster in wolfSSL than OpenSSL and the overheads and hashing difference once again impacted the results. The server is performing key generation, secret generation, and signing operations. wolfSSL is 7-13% faster at performing these operations with P-256 on the platform and about 3% faster performing X25519 operations. wolfSSL was seen to be 35-40% faster than OpenSSL when using P-256 and 20-30% faster when Curve25519 is used for key exchange. When client authentication was also performed, similar improvements were seen.
Performance increases like 35-40% are real reasons to use wolfSSL rather than OpenSSL for TLS 1.3 and especially on Intel x86 64-bit.
If you would like more information about using wolfSSL in your project, email us at facts@wolfssl.com.
wolfSSL FAQ page
The wolfSSL FAQ page can be useful for information or general questions that need need answers immediately. It covers some of the most common questions that the support team receives, along with the support team's responses. It's a great resource for questions about wolfSSL, embedded TLS, and for solutions to problems getting started with wolfSSL.
To view this page for yourself, please follow this link here.
Here is a sample list of 5 questions that the FAQ page covers:
- How do I build wolfSSL on ... (*NIX, Windows, Embedded device) ?
- How do I manage the build configuration of wolfSSL?
- How much Flash/RAM does wolfSSL use?
- How do I extract a public key from a X.509 certificate?
- Is it possible to use no dynamic memory with wolfSSL and/or wolfCrypt?
Have a question that isn't on the FAQ? Feel free to email us at support@wolfssl.com.
TLS 1.3 Performance Part 6 – Throughput
Some interesting results were found when comparing the throughput of TLS 1.2 and TLS 1.3 using an assembly optimized wolfSSL – some good, some bad. This is the last of the blogs discussing the performance differences observed between TLS 1.2 and TLS 1.3 in wolfSSL and how to make the most of them in your applications. There are differences in the way the data is encrypted in TLS 1.2 and 1.3. For some algorithms this makes a noticeable difference.
TLS 1.2 encrypts the plaintext of the message and generates an authentication code on the encrypted data plus additional_data which includes: a 64-bit sequence number, 1 byte content type, 2 byte version and 2 byte length. This is a total of 13 extra bytes in additional_data.
TLS 1.3 encrypts the plaintext of the message plus one byte for the real record type and generates an authentication code on the encrypted data plus the record header of 5 bytes.
For AES-GCM cipher suites the throughput was observed to be slightly increased with the Intel x86 64-bit optimized assembly code. This is due to the number of bytes passed in as additional authentication data (AAD). The AAD bytes are processed separately before encryption and decryption and it turned out processing 5 bytes was faster than 13. The extra byte on the end of the encrypted data did not have a significant impact.
For Chacha20-Poly1305 the different size of data passed in as AAD has no significant impact as the data is placed into a 16 byte block and padded before being processed. But, the extra byte at the end of the plaintext did impact the Chacha20 and Poly1305 performance. For Poly1305, the extra byte resulted in an extra 16 byte block being processed. In total this had about a 3-5% impact on throughput with the Intel x86 64-bit optimized assembly code.
TLS 1.3 has better throughput when using AES-GCM and is another reason to change. For maximum throughput consider sending one less than the maximum plaintext size, by default 16384 bytes, in an application data message. This will have a positive impact for both AES-GCM and Chacha20-Poly1305 cipher suites.
Part 1 (TLS 1.3 Performance – Resumption)
Part 2 (TLS 1.3 Performance – Full Handshake)
Part 3 (TLS 1.3 Performance – Pre-Shared Key (PSK))
Part 4 (TLS 1.3 Performance – Server Pre-Generation)
Part 5 (TLS 1.3 Performance – Client-Server Authentication)
TLS 1.3 Performance Part 5 – Client-Server Authentication
TLS 1.3 has some significant changes from TLS 1.2 in the ordering of handshake messages and this impacts performance. This is the fifth part of six blogs discussing the performance differences observed between TLS 1.2 and TLS 1.3 in wolfSSL and how to make the most of them in your applications. This blog discusses how the changes to certificate based client-server authentication in TLS 1.3 adversely affects performance.
Let’s start with a look at the TLS 1.2 full handshake performing client-server authentication with certificates below.
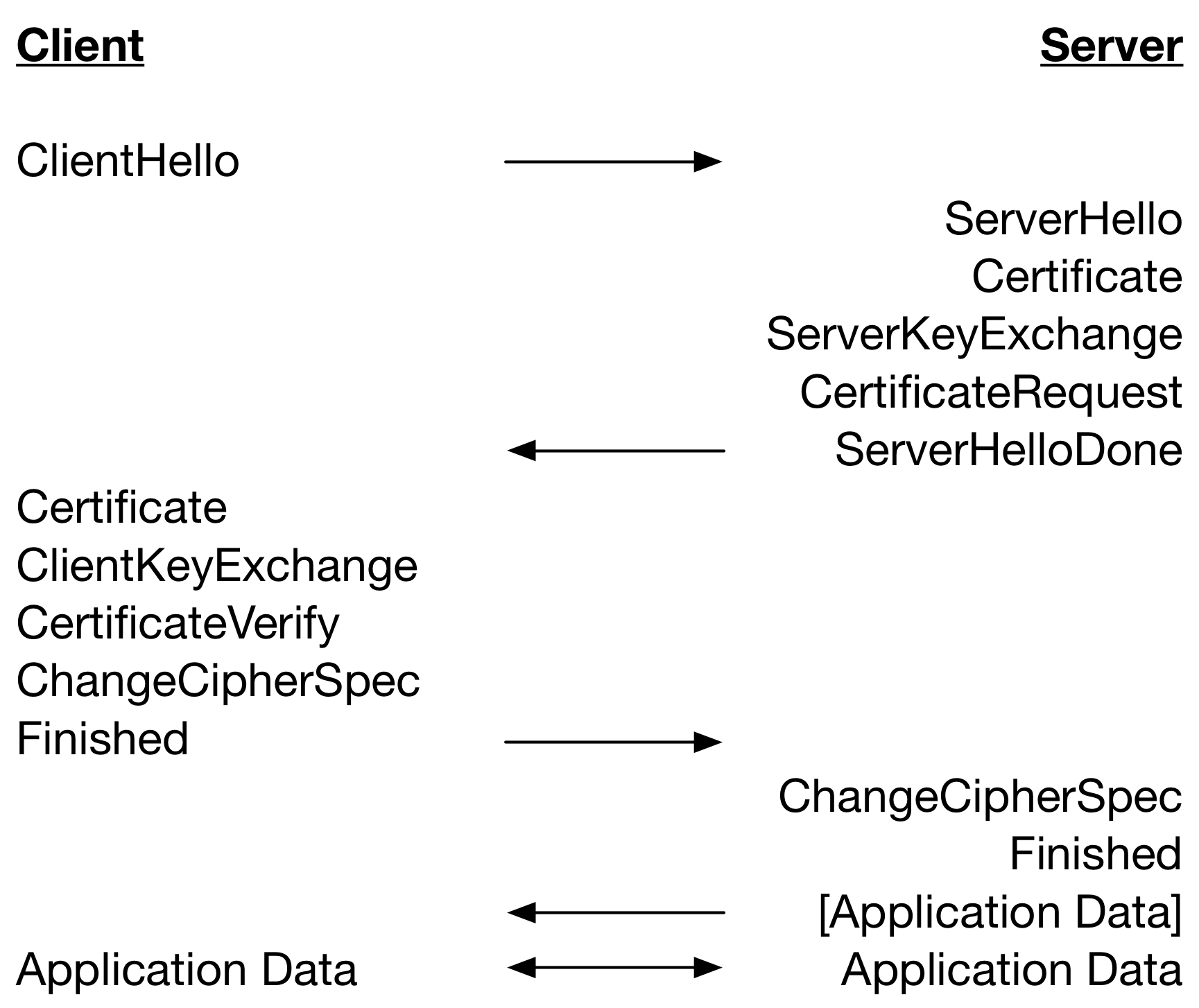
A TLS 1.3 full handshake (without HelloRetryRequest) performing client and server authentication with certificates is given below.
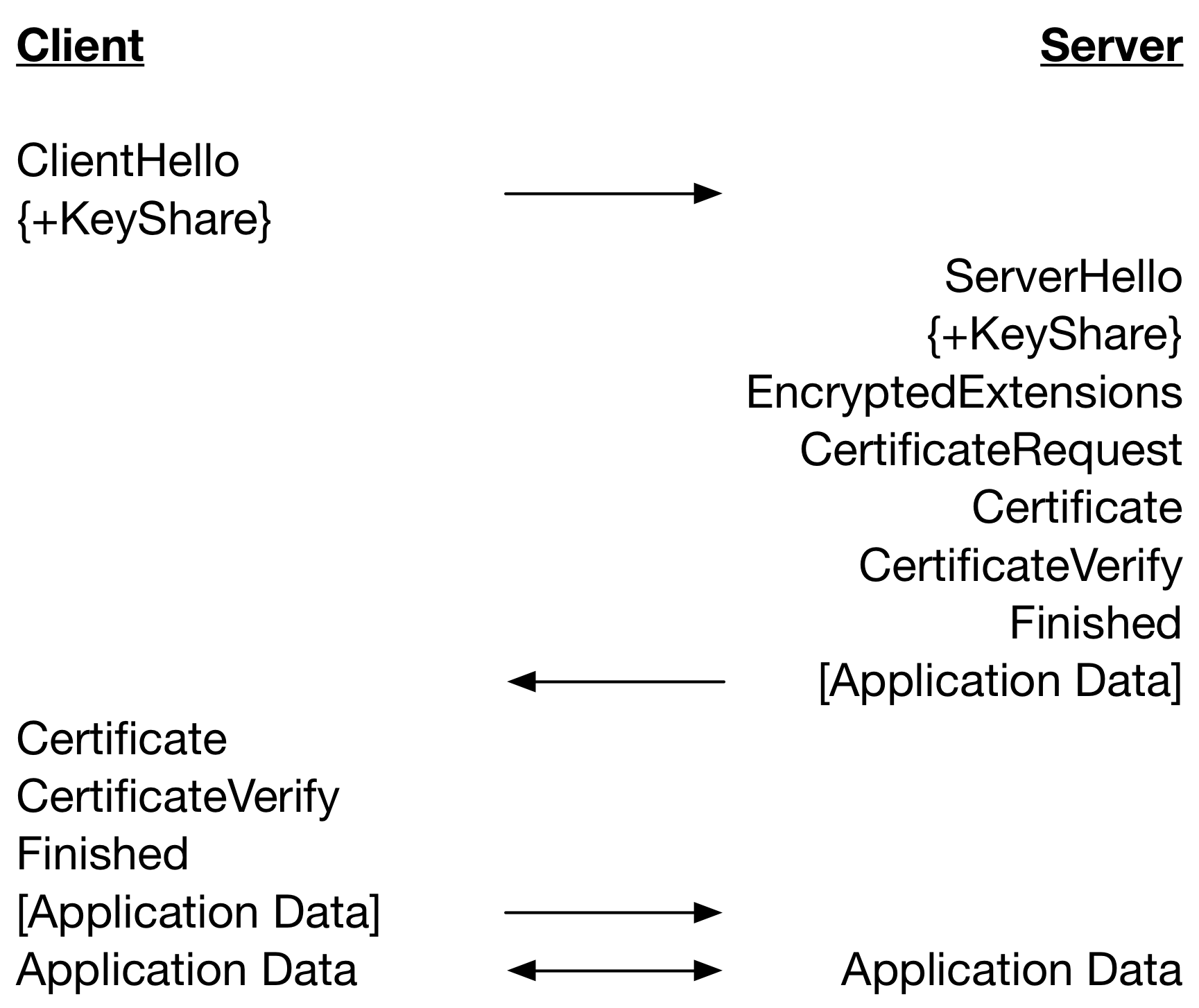
Notice that there is one less round trip until Application Data can be sent in TLS 1.3 as compared to TLS 1.2. This improves performance on high latency networks but there is a downside. What is clear in the diagram is when messages are sent but not how and when handshake messages are processed.
The table below restates the TLS 1.2 handshake, but includes the processing of messages and the major cryptographic operations that are performed. Operations are on the same line if the operations are performed at the same time relative to network latency.
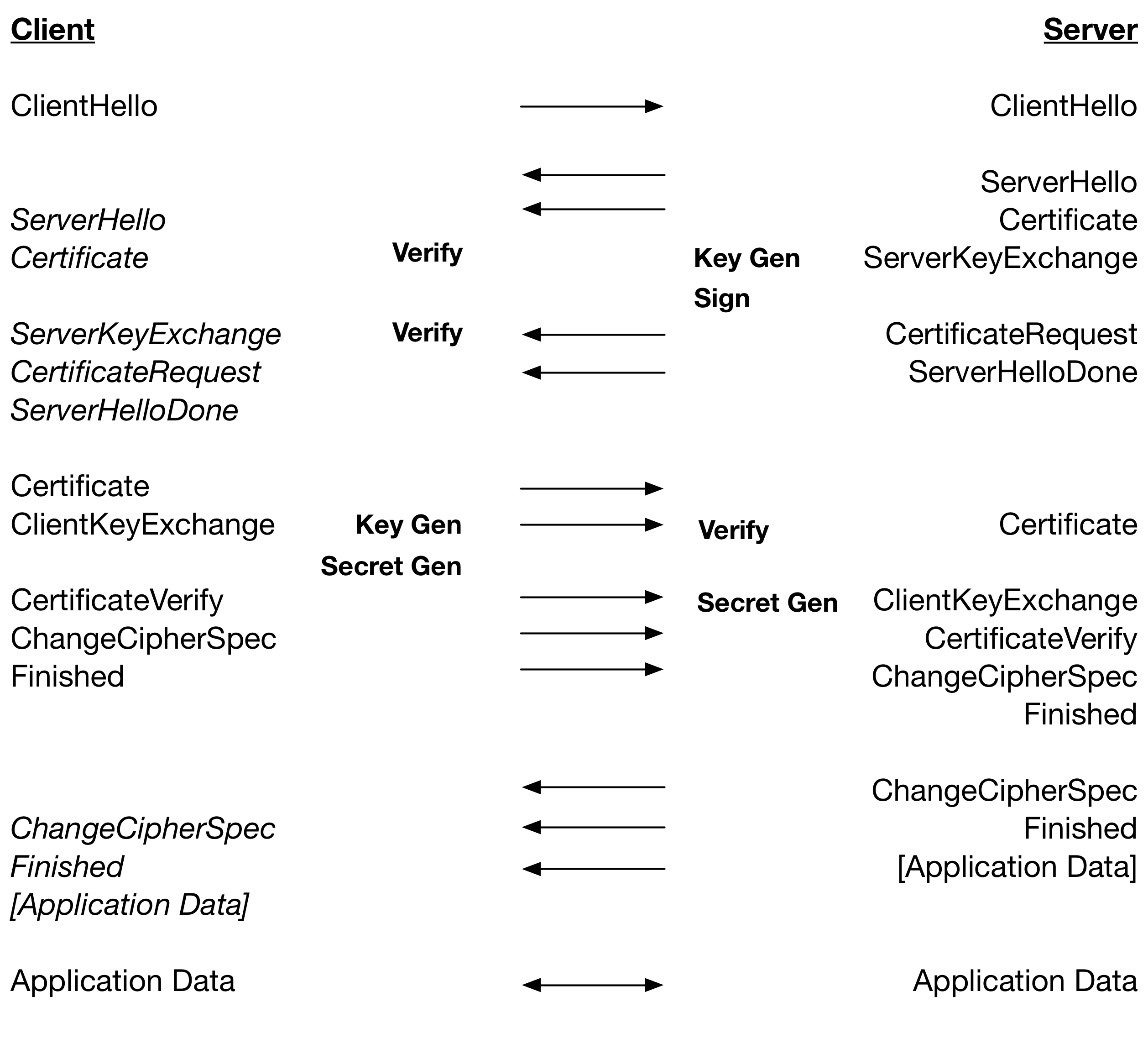
The server produces a KeyShare, sends the ServerHello, and then quickly sends the EncryptedExtensions, CertificateRequest and Certificate messages. The CertificateVerify takes a while to produce and the Finished message is quick. The client takes a while to process the KeyShare, quickly process the EncryptedExtensions and CertificateRequest messages, and spends a long time performing certificate chain verification. The CertificateVerify will typically arrive during the chain verification and then the client processes the rest of the messages synchronously. As a result, there is little overlap.
From this we can see that for RSA where Verify is very fast relative to Sign, a TLS 1.2 handshake is dependent on: 2 x Key Gen, 2 x Secret Gen, 1 x Sign and 2 x Verify. For ECDSA, where Verify is slower than Key Gen plus Sign: 1 x Secret Gen and 3 x Verify.
The table below restates the TLS 1.3 handshake, including processing of message and the major cryptographic operations.
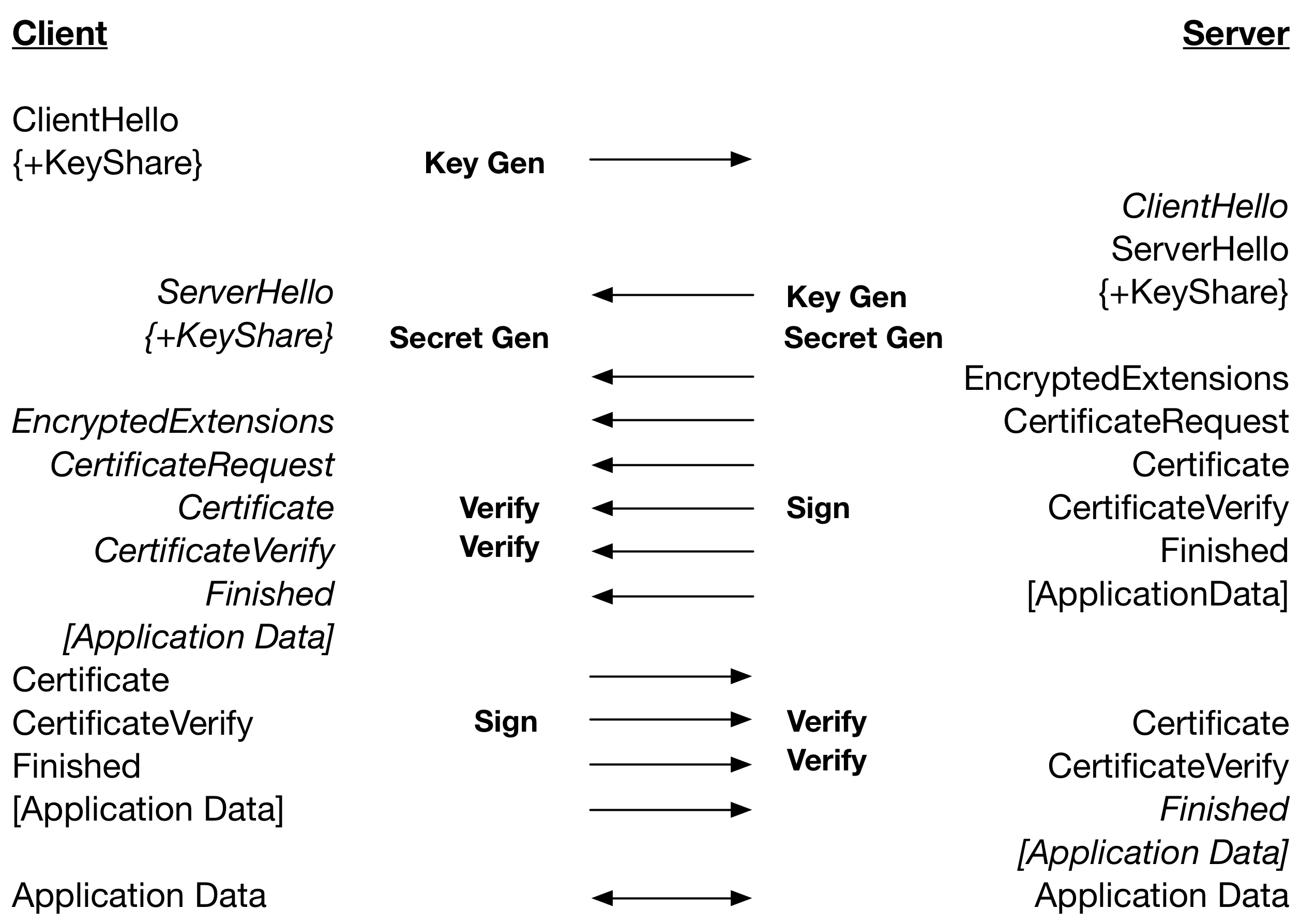
From this we can see that a TLS 1.3 handshake using RSA certificates is dependent on: 2 x Key Gen, 1 x Sercret Gen, 2 x Sign. Therefore a Secret Gen and 2 x Verify in TLS 1.2 are replaced with a Sign. Using ECDSA a handshake is dependent on: 2 x Key Gen, 1 x Sercret Gen and 4 x Verify. Therefore, a Secret Gen and Sign in TLS 1.2 is replaced by 2 x Verify.
This means that for low latency networks TLS 1.3 can be slightly slower or about as fast as TLS 1.2. The only practical mitigation for ECC certificates is to minimize the amount of work performed in chain verification. Having the server certificate stored on the client and/or the client certificate stored on the server will improve TLS 1.3 performance but at the risk of lower security.
The next blog will be the final one in this series and will discuss difference in throughput between TLS 1.2 and 1.3.
Part 1 (TLS 1.3 Performance – Resumption)
Part 2 (TLS 1.3 Performance – Full Handshake)
Part 3 (TLS 1.3 Performance – Pre-Shared Key (PSK))
Part 4 (TLS 1.3 Performance – Server Pre-Generation)
wolfSSL Competitive Upgrade Program
One of the services that wolfSSL provides is the wolfSSL Competitive Upgrade Program. With this program, wolfSSL offer competitive upgrade pricing for those who wish move from an outdated or expensive SSL/TLS library to wolfSSL with low cost and minimal disturbance to their code base.
Here’s an outline of the Competitive Upgrade Program:
- You need to currently be using a commercial competitor to wolfSSL.
- You will receive up to two weeks of on-site consulting to switch out your old SSL/TLS library with wolfSSL. Travel expenses are not included.
- Normally, two weeks is the right amount of time for us to make the replacement in your code and do initial testing. Additional consulting on a replacement is available as needed.
- You will receive the standard wolfSSL royalty free license to ship with your product.
- The price is $10,000.
The purpose of this program is to enable users who are currently spending too much on their embedded SSL/TLS implementation to move to wolfSSL with ease. If you are interested in learning more, or interested in how wolfSSL compares to what you are currently using, then please contact us at facts@wolfssl.com.
Weekly updates
Archives
- April 2025 (19)
- March 2025 (22)
- February 2025 (21)
- January 2025 (23)
- December 2024 (22)
- November 2024 (29)
- October 2024 (18)
- September 2024 (21)
- August 2024 (24)
- July 2024 (27)
- June 2024 (22)
- May 2024 (28)
- April 2024 (29)
- March 2024 (21)
- February 2024 (18)
- January 2024 (21)
- December 2023 (20)
- November 2023 (20)
- October 2023 (23)
- September 2023 (17)
- August 2023 (25)
- July 2023 (39)
- June 2023 (13)
- May 2023 (11)
- April 2023 (6)
- March 2023 (23)
- February 2023 (7)
- January 2023 (7)
- December 2022 (15)
- November 2022 (11)
- October 2022 (8)
- September 2022 (7)
- August 2022 (12)
- July 2022 (7)
- June 2022 (14)
- May 2022 (10)
- April 2022 (11)
- March 2022 (12)
- February 2022 (22)
- January 2022 (12)
- December 2021 (13)
- November 2021 (27)
- October 2021 (11)
- September 2021 (14)
- August 2021 (10)
- July 2021 (16)
- June 2021 (13)
- May 2021 (9)
- April 2021 (13)
- March 2021 (24)
- February 2021 (22)
- January 2021 (18)
- December 2020 (19)
- November 2020 (11)
- October 2020 (3)
- September 2020 (20)
- August 2020 (11)
- July 2020 (7)
- June 2020 (14)
- May 2020 (13)
- April 2020 (14)
- March 2020 (4)
- February 2020 (21)
- January 2020 (18)
- December 2019 (7)
- November 2019 (16)
- October 2019 (14)
- September 2019 (18)
- August 2019 (16)
- July 2019 (8)
- June 2019 (9)
- May 2019 (28)
- April 2019 (27)
- March 2019 (15)
- February 2019 (10)
- January 2019 (16)
- December 2018 (24)
- November 2018 (9)
- October 2018 (15)
- September 2018 (15)
- August 2018 (5)
- July 2018 (15)
- June 2018 (29)
- May 2018 (12)
- April 2018 (6)
- March 2018 (18)
- February 2018 (6)
- January 2018 (11)
- December 2017 (5)
- November 2017 (12)
- October 2017 (5)
- September 2017 (7)
- August 2017 (6)
- July 2017 (11)
- June 2017 (7)
- May 2017 (9)
- April 2017 (5)
- March 2017 (6)
- January 2017 (8)
- December 2016 (2)
- November 2016 (1)
- October 2016 (15)
- September 2016 (6)
- August 2016 (5)
- July 2016 (4)
- June 2016 (9)
- May 2016 (4)
- April 2016 (4)
- March 2016 (4)
- February 2016 (9)
- January 2016 (6)
- December 2015 (4)
- November 2015 (6)
- October 2015 (5)
- September 2015 (5)
- August 2015 (8)
- July 2015 (7)
- June 2015 (9)
- May 2015 (1)
- April 2015 (4)
- March 2015 (12)
- January 2015 (4)
- December 2014 (6)
- November 2014 (3)
- October 2014 (1)
- September 2014 (11)
- August 2014 (5)
- July 2014 (9)
- June 2014 (10)
- May 2014 (5)
- April 2014 (9)
- February 2014 (3)
- January 2014 (5)
- December 2013 (7)
- November 2013 (4)
- October 2013 (7)
- September 2013 (3)
- August 2013 (9)
- July 2013 (7)
- June 2013 (4)
- May 2013 (7)
- April 2013 (4)
- March 2013 (2)
- February 2013 (3)
- January 2013 (8)
- December 2012 (12)
- November 2012 (5)
- October 2012 (7)
- September 2012 (3)
- August 2012 (6)
- July 2012 (4)
- June 2012 (3)
- May 2012 (4)
- April 2012 (6)
- March 2012 (2)
- February 2012 (5)
- January 2012 (7)
- December 2011 (5)
- November 2011 (7)
- October 2011 (5)
- September 2011 (6)
- August 2011 (5)
- July 2011 (2)
- June 2011 (7)
- May 2011 (11)
- April 2011 (4)
- March 2011 (12)
- February 2011 (7)
- January 2011 (11)
- December 2010 (17)
- November 2010 (12)
- October 2010 (11)
- September 2010 (9)
- August 2010 (20)
- July 2010 (12)
- June 2010 (7)
- May 2010 (1)
- January 2010 (2)
- November 2009 (2)
- October 2009 (1)
- September 2009 (1)
- May 2009 (1)
- February 2009 (1)
- January 2009 (1)
- December 2008 (1)

