RECENT BLOG NEWS
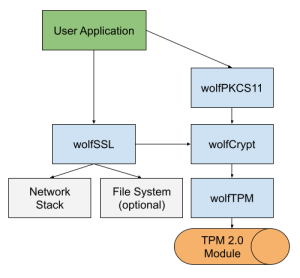
How to make your TPM talk PKCS11
wolfSSL has implemented our own PKCS11 provider library to leverage cryptographic hardware and keystores on various systems. Recently we added support for using a TPM 2.0 module with wolfTPM (see pull request #23). We believe that this functionality is particularly useful for users that have coded to the PKCS11 standard, but need to switch to a TPM or fTPM.
The wolfTPM and wolfPKCS11 libraries are both fully portable to any RTOS or embedded system, including bare-metal. The PKCS11 interface provides a standardized API set for making cryptographic calls to a hardware module. All TPM’s support RSA and ECC keys, so when using a TPM only those two asymmetric algorithms are supported.
Our example PKCS11 applications can run on any Linux or Windows that have a TPM available. If a TPM is not available you can use the TPM simulators (see SWTPM.md). We have also successfully ported it to a bare-metal STM32 target for testing.
A TPM offers physical protection of all private keys and benefits from the TPM performance when doing asymmetric operations like signing, verification or shared secrets. All communication to the TPM uses the parameter encryption feature with AES CFB mode.
If desired the PKCS11 keystore can use the TPM NV for storing the encrypted key material.
Typical implementation including TLS support:
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
wolfMQTT Releases v1.18.0
The Christmas release of wolfMQTT, v1.18.0, is now available! This release has several bug fixes and optimizations including:
- Add curl easy socket backend. by @philljj in #380
- WOLFMQTT_EXAMPLE_CERT allowing static or extern cert assignment by @gojimmypi in #354
- Tiny readme cleanup. by @philljj in #381
- Fix high coverity issues by @embhorn in #379
- Add broker check to scripts by @embhorn in #385
- Cmake build fixes by @embhorn in #384
Release 1.18.0 has been developed according to wolfSSL’s development and QA process (see link below) and successfully passed the quality criteria.
https://www.wolfssl.com/about/wolfssl-software-development-process-quality-assurance
Check out the changelog from the download for a full list of features and fixes, or contact us at facts@wolfssl.com with any questions: https://github.com/wolfSSL/wolfMQTT/blob/master/ChangeLog.md
While you’re there, show us some love and give the wolfMQTT project a Star!
Download the latest release or clone directly from our GitHub repository today.
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
wolfSSH 1.4.15 Now Available!
Merry Christmas! The Christmas release of wolfSSH is here, version 1.4.15!
Version 1.4.15 brings with it a fix for a vulnerability, bug fixes, new features, and some enhancements as well! For a description of vulnerabilities fixed, please see our vulnerability page. New features in this release include a wolfSSH client application, support for OpenSSH-style keys, and Zephyr RTOS builds.
We also have a nice round of enhancements which range from better testing, improved portability, terminal enhancements (run vim or tmux!), and more!
A list of new features and enhancements from our ChangeLog is listed below. For a full list of fixes see our complete ChangeLog on GitHub.
Vulnerability Fix
-
Fixes a potential vulnerability described in the paper “Passive SSH Key Compromise via Lattices”. While the misbehavior described hasn’t been observed in wolfSSH, the fix is now implemented. The RSA signature is verified before sending to the peer.
- Keegan Ryan, Kaiwen He, George Arnold Sullivan, and Nadia Heninger. 2023. Passive SSH Key Compromise via Lattices. Cryptology ePrint Archive, Report 2023/1711. https://eprint.iacr.org/2023/1711.
New Features
- Added wolfSSH client application.
- Added support for OpenSSH-style private keys, like those made by ssh-keygen.
- Added support for the Zephyr RTOS.
- Added support for multiple authentication schemes in the userauth callback with the error response WOLFSSH_USERAUTH_PARTIAL_SUCCESS.
Improvements
Fixes
- When setting the file permissions for a file in Zephyr, use the correct permission constants.
- Fix buffer issue in DoReceive() on some edge failure conditions.
- Prevent wolfSSHd zombie processes.
- Fixed a few references to the heap variable for user supplied memory allocation functions.
- Fixed an index update when verifying the server’s RSA signature during KEX.
- Fixed some of the guards around optional code.
- Fixed some would-block cases when using non-blocking sockets in the examples.
- Fixed some compile issues with liboqs.
- Fix for interop issue with OpenSSH when using AES-CTR.
Visit our download page or wolfSSH GitHub repository to download the release bundle, and feel free to email us at facts@wolfSSL.com or support@wolfssl.com, or call us at +1 425 245 8247 with any questions about the wolfSSH embedded SSH library or other products.
Download wolfSSL Now
Live Webinar: Getting Started with wolfSSL in 2024
Welcome to our exclusive webinar, ‘Getting Started with wolfSSL in 2024’. Join us for an insightful session presented by Chris Conlon, wolfSSL Engineering Manager. Scheduled for January 4th at 9 am PT, this webinar is your gateway to mastering wolfSSL, the ultimate Embedded SSL/TLS Library for IoT device security, advanced encryption algorithms and much more.
wolfSSL has earned a reputation for high-quality, portable, and embedded security software, securing over 2 billion applications and devices.
Watch the webinar here: Getting Started with wolfSSL in 2024
Chris will delve into a wide array of topics:
- Overview of TLS 1.3
- wolfSSL package structure
- Building wolfSSL
- wolfCrypt Test and Benchmark Applications
- wolfSSL basic API usage
- Tips on debugging
And much more
This is your chance to grasp the essential details of utilizing wolfSSL, learning its fundamentals, and discovering the best practices for leveraging wolfSSL throughout 2024.
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
wolfTPM Support for Encrypting Secrets with ECC
wolfTPM is a portable TPM 2.0 stack with backward API compatibility designed for embedded use, and the newly released wolfTPM v3.0.0 includes support for encrypting secrets with ECC keys.
TPM’s encrypt secrets to prevent their disclosure to unauthorized entities. And whereas encryption with RSA keys was already supported in wolfTPM, users now have the option to leverage ECC keys.
This enables using an ECC primary key together with an authenticated session to enable parameter encryption of sensitive data. The TCG specification defines the method for using ECDH and a custom KDF to derive a shared secret between the host and the TPM device to be used for parameter encryption with AES CFB or XOR.
wolfTPM already has full support for using ECC keys in the TPM for signing/verification (ECDSA) and shared secret ECDH(E) using TPM API’s.
Finally, don’t forget that if you are intent on adding a TPM to an embedded MCU or MPU design, wolfTPM is the obvious choice, as it runs on everything from bare metal to FreeRTOS, VxWorks, Integrity, QNX, and many others! You can also expect wolfTPM to get qualified for DO-178 in the coming year.
Contact us at facts@wolfSSL.com or call us at +1 425 245 8247 with any questions, comments or suggestions.
Download wolfSSL Now
wolfTPM STM32Cube Expansion Package for STM32 is now available!
wolfTPM is a portable TPM 2.0 stack with backward API compatibility designed for embedded use, and with the new STM32Cube Expansion Pack, STM32 developers are given a smooth sailing route to wolfTPM integration.
wolfTPM has had HAL IO Callback examples for STM32CubeMX for a while now, and supports SPI and out-of-the-box I2C for STM32CubeMX projects. The STM32Cube Pack grants easy access to wolfTPM’s features on the STM32. Some of the key features are RSA & ECC encrypt/decrypt, Key Generation/Loading, Sealing/Unsealing, Attestation, PCR Extend/Quote and Secure Root of Trust.
Download the new STM32Cube Pack from https://www.wolfssl.com/files/ide/I-CUBE-wolfTPM.pack and follow the documentation here to get started.
You can also reference this webinar for more insight on running wolfSSL on STM32 hardware. How to use wolfSSL software expansion for STM32Cube
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
Live Webinar: Security in Avionics – Tiger Lake and wolfBoot with DO-178C
Join us for our final 2023 webinar, Security in Avionics – Tiger Lake and wolfBoot with DO-178C! Explore DO-178C Secure Boot with wolfBoot on Tiger Lake UP3 11th Gen Intel® Core™ Processors alongside wolfSSL Lead Embedded Software Engineer, Tesfa Mael, on December 21st at 10 am PT.
Watch the webinar here: Security in Avionics – Tiger Lake and wolfBoot with DO-178C
Ensure the safety, functionality, and security of avionics systems with a robust foundation in secure boot and firmware updates. Achieving certifications like DO-178C is crucial, necessitating comprehensive solutions. Join Tesfa as he navigates how to establish this foundation using Intel’s secure hardware solutions alongside wolfBoot, the secure bootloader developed by wolfSSL. wolfBoot, a portable and certifiable bootloader and firmware update solution, harnesses Intel technologies like AES-NI and AVX2 to optimize boot performance and bolster security.
Don’t miss this opportunity to gain insights into maximizing avionics security through DO-178C Secure Boot with wolfBoot on Tiger Lake UP3 11th Gen Intel® Core™ Processors. Elevate your technical skills and secure your avionics systems effectively with wolfSSL.
If you have questions about any of the above, please contact us at facts@wolfSSl.com or call us at +1 425 245 8247.
Download wolfSSL Now
wolfTPM based Root of Trust for Secure Boot
wolfTPM is a portable TPM 2.0 stack with backward API compatibility designed for embedded use, and the newly released wolfTPM v3.0.0 provides examples for Secure Boot solutions to store a Root of Trust in non-volatile (NV) memory.
Secure Boot for your microcontroller is essential to protect against malware during the earliest stages of your system boot, and establishing a Root of Trust is the first step towards that direction. The example was implemented with our Secure Boot solution wolfBoot.
See the documentation examples/boot/README.md and docs/TPM.md for more details on how to set up a Root of Trust with authentication and tamper protection using wolfTPM.
The design in the example for storage of public key based Root of Trust into TPM entails using AES-CFB parameter encryption for all communication (salted and bound) and deriving a password based on unique device parameters used as “auth” to load NV (authenticate). The approach is to anchor the public key into the TPM NV storage such that it cannot be erased or tampered with. The NV stores a hash of the public key and wolfBoot keeps the public key internally and programs the TPM with the NV if not populated. The platform NV is locked and created under the platform hierarchy. It is recommended to supply a derived “authentication” value to prevent TPM tampering. This authentication value is encrypted on the bus.
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
wolfTPM support for sealing/unsealing based on externally signed PCR
wolfTPM is a portable TPM 2.0 stack with backward API compatibility designed for embedded use, and the newly released wolfTPM v3.0.0 includes support for sealing/unsealing secrets to authority signed Platform Configuration Registers (PCR’s).
One of the most important features of the TPM 2.0 specification is the resolution of PCR brittleness. PCR brittleness is encountered when secrets like keys/data are sealed to PCR values and changes to hardware/software result in changes to the PCR values. With the altered PCR values, there is a mismatch of hashes and the secrets can no longer be unsealed. With the TPM 2.0 specification, it’s possible to seal/unseal secrets via cryptographic signatures of the PCR’s, removing the requirement to unseal then seal secrets whenever changes are made to the PCR values. wolfTPM now supports this feature.
See the documentation here examples/boot#secure-boot-encryption-key-storage for a wolfTPM example of using a private key to sign the state of a PCR, then seal and unseal a secret using the signed policy and a public key.
Our secure bootloader, wolfBoot, also supports this feature. See here docs/TPM.md#sealing-and-unsealing-a-secret.
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
Live Webinar: wolfEngine vs wolfProvider
Join our insightful webinar: wolfEngine vs wolfProvider, led by wolfSSL Senior Software Developer Anthony, on December 14th at 10 am PT.
Watch the webinar here: wolfEngine vs wolfProvider
As you may be aware, the OpenSSL series 3.x has been launched, introducing a new FIPS 140-3 requirement. wolfSSL is here to simplify potentially challenging decisions for you. Anthony will explore the differences between wolfEngine and wolfProvider and demonstrate how to integrate them seamlessly with OpenSSL.
Sneak peek of the webinar:
-
- Optimal Alternative: OpenSSL Compat layer
- Understanding the OpenSSL 1.0.2, 1.1.1, and 3.x.y Branch Releases
- Determining Suitable Branches for Engines and Providers
- Utilizing wolfEngine and wolfProvider with the openssl app
- Integrating wolfEngine and wolfProvider with the OpenSSL API
- Available algorithms and cryptographic primitives
- Insights on FIPS compliance
…And much more
This is an excellent chance to discover how you can efficiently meet the new OpenSSL requirements with wolfSSL. Anthony will showcase how wolfEngine and wolfProvider act as connectors between the OpenSSL and wolfCrypt FIPS, saving you time and effort.
Make sure to Watch it today!
As always, our webinars will include Q&A sessions throughout. If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now
Weekly updates
Archives
- April 2025 (19)
- March 2025 (22)
- February 2025 (21)
- January 2025 (23)
- December 2024 (22)
- November 2024 (29)
- October 2024 (18)
- September 2024 (21)
- August 2024 (24)
- July 2024 (27)
- June 2024 (22)
- May 2024 (28)
- April 2024 (29)
- March 2024 (21)
- February 2024 (18)
- January 2024 (21)
- December 2023 (20)
- November 2023 (20)
- October 2023 (23)
- September 2023 (17)
- August 2023 (25)
- July 2023 (39)
- June 2023 (13)
- May 2023 (11)
- April 2023 (6)
- March 2023 (23)
- February 2023 (7)
- January 2023 (7)
- December 2022 (15)
- November 2022 (11)
- October 2022 (8)
- September 2022 (7)
- August 2022 (12)
- July 2022 (7)
- June 2022 (14)
- May 2022 (10)
- April 2022 (11)
- March 2022 (12)
- February 2022 (22)
- January 2022 (12)
- December 2021 (13)
- November 2021 (27)
- October 2021 (11)
- September 2021 (14)
- August 2021 (10)
- July 2021 (16)
- June 2021 (13)
- May 2021 (9)
- April 2021 (13)
- March 2021 (24)
- February 2021 (22)
- January 2021 (18)
- December 2020 (19)
- November 2020 (11)
- October 2020 (3)
- September 2020 (20)
- August 2020 (11)
- July 2020 (7)
- June 2020 (14)
- May 2020 (13)
- April 2020 (14)
- March 2020 (4)
- February 2020 (21)
- January 2020 (18)
- December 2019 (7)
- November 2019 (16)
- October 2019 (14)
- September 2019 (18)
- August 2019 (16)
- July 2019 (8)
- June 2019 (9)
- May 2019 (28)
- April 2019 (27)
- March 2019 (15)
- February 2019 (10)
- January 2019 (16)
- December 2018 (24)
- November 2018 (9)
- October 2018 (15)
- September 2018 (15)
- August 2018 (5)
- July 2018 (15)
- June 2018 (29)
- May 2018 (12)
- April 2018 (6)
- March 2018 (18)
- February 2018 (6)
- January 2018 (11)
- December 2017 (5)
- November 2017 (12)
- October 2017 (5)
- September 2017 (7)
- August 2017 (6)
- July 2017 (11)
- June 2017 (7)
- May 2017 (9)
- April 2017 (5)
- March 2017 (6)
- January 2017 (8)
- December 2016 (2)
- November 2016 (1)
- October 2016 (15)
- September 2016 (6)
- August 2016 (5)
- July 2016 (4)
- June 2016 (9)
- May 2016 (4)
- April 2016 (4)
- March 2016 (4)
- February 2016 (9)
- January 2016 (6)
- December 2015 (4)
- November 2015 (6)
- October 2015 (5)
- September 2015 (5)
- August 2015 (8)
- July 2015 (7)
- June 2015 (9)
- May 2015 (1)
- April 2015 (4)
- March 2015 (12)
- January 2015 (4)
- December 2014 (6)
- November 2014 (3)
- October 2014 (1)
- September 2014 (11)
- August 2014 (5)
- July 2014 (9)
- June 2014 (10)
- May 2014 (5)
- April 2014 (9)
- February 2014 (3)
- January 2014 (5)
- December 2013 (7)
- November 2013 (4)
- October 2013 (7)
- September 2013 (3)
- August 2013 (9)
- July 2013 (7)
- June 2013 (4)
- May 2013 (7)
- April 2013 (4)
- March 2013 (2)
- February 2013 (3)
- January 2013 (8)
- December 2012 (12)
- November 2012 (5)
- October 2012 (7)
- September 2012 (3)
- August 2012 (6)
- July 2012 (4)
- June 2012 (3)
- May 2012 (4)
- April 2012 (6)
- March 2012 (2)
- February 2012 (5)
- January 2012 (7)
- December 2011 (5)
- November 2011 (7)
- October 2011 (5)
- September 2011 (6)
- August 2011 (5)
- July 2011 (2)
- June 2011 (7)
- May 2011 (11)
- April 2011 (4)
- March 2011 (12)
- February 2011 (7)
- January 2011 (11)
- December 2010 (17)
- November 2010 (12)
- October 2010 (11)
- September 2010 (9)
- August 2010 (20)
- July 2010 (12)
- June 2010 (7)
- May 2010 (1)
- January 2010 (2)
- November 2009 (2)
- October 2009 (1)
- September 2009 (1)
- May 2009 (1)
- February 2009 (1)
- January 2009 (1)
- December 2008 (1)

