RECENT BLOG NEWS
Upcoming Webinar : Kernel Mode
In December 2020, wolfSSL 4.6.0 featured initial support for building as a Linux kernel module, supplying the entire native wolfCrypt and wolfSSL APIs directly to other kernel modules.
Now, with our just-released milestone 5.0.0 release, we have extended that support with in-kernel FIPS 140-3, additional accelerated cryptography options on x86, and substantial improvements in stack usage.
Porting a library as large and complex as wolfSSL to the Linux kernel has been a multi-phase undertaking, guided by three key objectives:
- A build process that is completely turnkey on supported kernel lines, via configure –enable-linuxkm and –with-linux-source=/source/tree/top.
- A source tree that remains unified: the library and the kernel module are built from the same codebase, and differ only in various settings, and in kernel-specific glue logic.
- Module builds that use the Linux in-tree Kbuild toolchain, rather than a bespoke out-of-tree build system, to facilitate simultaneous and continuing support for a wide variety of old and new kernel releases.
The Linux kernel is not a POSIX target, and many facilities commonly available to libraries and applications are unavailable (e.g. stack red zones, the C library, thread-local storage) or severely restricted (e.g. stack depth and vectorized instructions). Additionally, each minor kernel version and hardware target has peculiarities that cannot be ignored.
In this presentation, we will chronicle some of the challenges we encountered porting wolfSSL to this unusual target, and the solutions we developed.
We will discuss:
- Refactors spanning the entire wolfSSL library to strictly control peak stack usage;
- New development and QA tools developed for the kernel module project, such as fine-grained cumulative stack depth instrumentation and error-checking vector register save/restore and asserts;
- Porting wolfcrypt_test to the kernel, for comprehensive validation of all cryptographic implementations;
- Automated translation of symbol visibility to kernel namespace export directives, leveraging ELF visibility tags;
- Extending the wolfSSL autotools configuration to set up a Kbuild configuration and seamlessly hand off control to Kbuild;
- New automated testing: continually testing module builds on the latest release (currently 5.15) and a substantial cross-section of LTS kernels (currently 3.16, 4.4, 4.9, 5.4, and 5.10);
- The challenges of maintaining squeaky-clean builds on kernels as old as 3.16 (2014) and as new as 5.15 (this week) from a single unified codebase that is directly and continually impacted by the engineering decisions of the Linux kernel developers;
- The challenge of FIPS 140-3 compliance in the Linux kernel: containerizing the FIPS module, stabilizing its hash, and refactoring thread-local storage requirements;
- An example application: wireGuard kernel module crypto rip&replace, and matching rip&replace of wireGuard user space software;
- The future: example applications that exercise in-kernel TLS negotiation, more x86 accelerations, acceleration on other architectures, etc.
Watch the webinar here: Linux Kernel Mode
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Securing CAN bus with TLS 1.3
One of the greatest security issues facing the automotive and aviation worlds is securing connections over CAN bus and its derivative protocols. The big issue with these protocols is that they do not have a method for authenticating who or what they are communicating with, and don’t encrypt the traffic. This leaves them open to a variety of well known attacks, like MITM, replay, and of course eavesdropping.
As many of our users are aware, wolfSSL is transport agnostic. As such, we do TLS 1.3 grade security, complete with authentication and encryption, over any number of transports, such as Bluetooth, BTLE, Zigbee, Zwave, serial, etc. Our transport agnostic strategy brings great benefit to environments where the transport protocol does not include security, or has poor security, because of its design or history.
We are now embarking on the mission to secure CAN bus with TLS 1.3! Are you curious or interested? If you have questions on any of the above, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfMQTT Features
The wolfMQTT library is an implementation of the MQTT Client written in C for embedded use, which supports SSL/TLS via the wolfSSL library. This library was built from the ground up to be multi-platform, space conscious and extensible. And most importantly it integrates with wolfSSL to provide TLS support, for a secure solution out of the gate!
Specifications supported
- MQTT v3.1.1
- MQTT v5.0
- MQTT-SN (Sensor Network) v1.2
Application architecture
- Non-blocking support for baremetal apps
- Multithread for OS/RTOS supporting threads
Callbacks
- Publish messages that are received can trigger a registered function
- Broker disconnect for easily handling reconnects
- Networking for simple integration with any I/O
- MQTTv5 properties can be handled with a registered function
Supported build environments:
- Mac/Linux/Unix with make files
- Visual Studio solution
- Arduino
- MinGW
- Cross-compile for any target
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
While you’re there, show us some love and give the wolfMQTT project a Star!
You can download the latest release here: https://www.wolfssl.com/download/ Or clone directly from our GitHub repository: https://github.com/wolfSSL/wolfMQTT
Post-Quantum Research Results from the pq-wolfssl Team
The pq-wolfssl development team have done an excellent experimental post-quantum integration. We applaud their efforts and wanted to summarize and share some fascinating things that they published in their paper. First we will discuss their scenario and then their conclusions.
The team’s objective was to study the possibility of a two-step migration strategy for post-quantum signature schemes. In their scenario, initially, only long lived root certificates would use public keys associated with stateful hash-based signature algorithms while the intermediate and end entity certificates continue to have public keys associated with conventional algorithms such ECDSA. It is important to note here (as is done in the paper as well), that stateful hash-based signature algorithms are already specified as IETF RFCs and are generally accepted to be secure as their building blocks are well trusted hash algorithms and Merkle trees and do not depend on new or exotic mathematical constructs.
Eventually, as the other post-quantum algorithms are standardized and trust builds, intermediate certificates can be issued with public keys associated with them. At this step end-entity certificates would then be issued with public keys associated with the new post-quantum algorithms as well. This finishes the migration process.
This begs the question, why not use stateful hash-based signature algorithms all throughout the chain from the beginning? The answer lies in the state. End entity certificates hold public keys that are associated with private keys that will be used during the handshake phase of the TLS 1.3 connection. The management of this state during on-line signing operations is ill advised for reasons that are not within the scope of this blog post. More detailed explanations can be found at NIST’s website.
They found that the first step of the migration could be done practically and with very little impact on connection establishment parameters. In their final migration step where the whole certificate chain and key establishment were all under post-quantum algorithms, they found that the best case scenario was feasable in all respects except RAM usage. They found that RAM usage was significantly higher.
In the paper, the team says “Therefore, we selected the open source TLS library wolfSSL (v4.7.0) for our integrations of PQC, because it is suitable for embedded systems and supports TLS 1.3.”
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Integration of the Falcon Signature Scheme into wolfSSL
A little while ago we announced support for post-quantum KEM groups and then hybrid groups. We are now proud to announce support for the PQC NIST round 3 finalist signature scheme FALCON. With this announcement, customers can now experiment with fully quantum-safe TLS 1.3 handshakes.
From a high level perspective, for every TLS 1.3 connection, authentication and confidentiality are the two main goals that protect each connection. Authentication is maintained via signature schemes such as ECDSA. Confidentiality is maintained by key establishment algorithms such as ECDHE and then using the established key with symmetric encryption algorithms such AES to encrypt a communication stream. We can thus decompose the security of the TLS 1.3 protocol into 3 types of cryptographic algorithms:
– authentication algorithms
– key establishment algorithms
– symmetric cipher algorithms
When a cryptographically relevant quantum computer is finally developed, Shor’s algorithm completely breaks the security of modern authentication and key establishment algorithms while Grover’s algorithm reduces the security of modern symmetric cipher algorithms by half. So, we must replace our modern authentication and key establishment algorithms with quantum-safe ones and double the strength of our symmetric cipher algorithms to maintain the security of our communications.
Now that wolfSSL has integrated FALCON, we can use it for authentication. We can use any one of our new KEMs and just in case, we can hybridize it with NIST-approved ECDSA groups. And finally, since the strength of AES-128 is generally accepted to be sufficient, we can double our strength by using AES-256 by using the AES_256_GCM_SHA384 TLS 1.3 ciphersuite. To get a connection that has such a handshake, you would run the following commands:
$ examples/server/server -v 4 -l TLS_AES_256_GCM_SHA384 \ -A certs/falcon_level5_root_cert.pem \ -c certs/falcon_level5_server_cert.pem \ -k certs/falcon_level5_server_key.pem \ --oqs P521_KYBER_LEVEL5 $ examples/client/client -v 4 -l TLS_AES_256_GCM_SHA384 \ -A certs/falcon_level5_root_cert.pem \ -c certs/falcon_level5_cleint_cert.pem \ -k certs/falcon_level5_client_key.pem \ --oqs P521_KYBER_LEVEL5
You can then use a modified wireshark that recognizes our algorithms to monitor the connection and see what is really going over the wire:
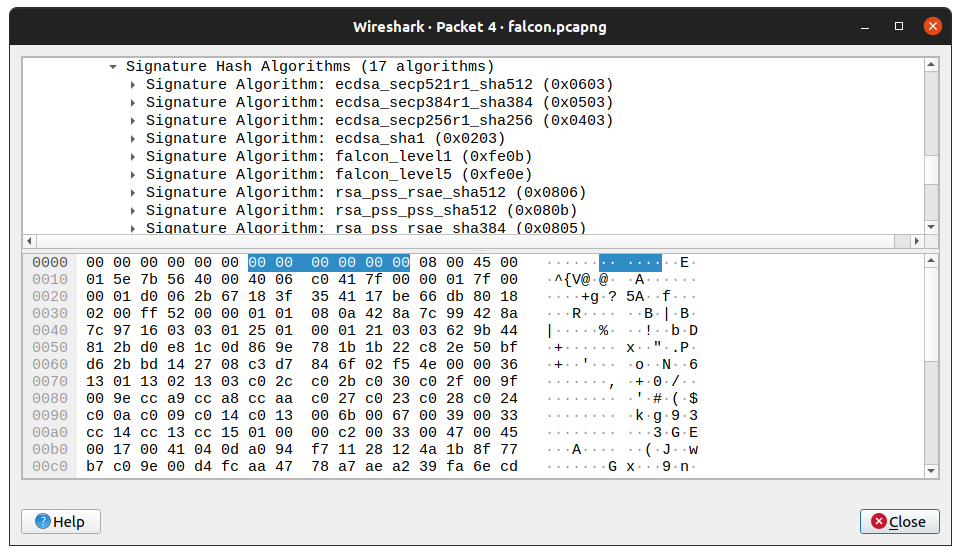
The merge request for the wireshark modifications can be found here:
https://gitlab.com/wireshark/wireshark/-/merge_requests/4924/
The pull request for instructions for making a docker image with the wireshark modifications can be found here:
https://github.com/open-quantum-safe/oqs-demos/pull/104
The integration of FALCON has made it onto our wolfSSL master branch, and will be part of the next release of wolfSSL.
One last word on the threat model and why it is important to consider post-quantum authentication sooner rather than later. Due to your application parameters or use case, it might not be cost effective or even possible to update software components. In these cases, you must carefully evaluate the lifetime of your product. If you project that we will see a cryptographically relevant quantum computer within the lifetime of your product, but it can’t be updated, then perhaps you need to start thinking about a strategy for moving to post-quantum algorithms today.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfMQTT Release v1.10.0
The fall release of wolfMQTT, v1.10.0, is now available! This release has several bug fixes and optimizations including:
- Improve FALL_THROUGH macro logic for XC32. (PR #227)
- Fix potential NULL printf in MqttSocket_Connect with verbose debug enabled. (PR #229)
- Fix non-block chunked transfer. (PR #230)
- Fix QoS responses (PR #231, 240)
- Fix MQTTv5 property handling (PR #232, 233, 234, 236, 238, 241)
- Fix fuzzing test issues (PR #242)
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
https://github.com/wolfSSL/wolfMQTT/blob/master/ChangeLog.md
While you’re there, show us some love and give the wolfMQTT project a Star!
You can download the latest release here: https://www.wolfssl.com/download/
Or clone directly from our GitHub repository: https://github.com/wolfSSL/wolfMQTT
What’s the difference between TLS vs DTLS?
The main difference is DTLS uses UDP and TLS uses TCP. DTLS stands for Datagram Transport Layer Security and is a communications protocol designed to protect data privacy and prevent eavesdropping/tampering. It is based on TLS protocol and used across web browsing, mail, and instant messaging.
Using the DTLS library of wolfSSL, sensor data is protected all the way from the client to the gateway, and then from the gateway on to the broker using standard TLS.
You can download our latest wolfSSL release here: https://www.wolfssl.com/download/
Or clone directly from our GitHub repository: https://github.com/wolfSSL/wolfssl
While you’re there, show us some love and give the wolfSSL project a Star!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL Cisco CJOSE Port
The wolfSSL embedded SSL/TLS library has maintained support for the Cisco CJOSE library since version 4.4.0. CJOSE implements Javascript Object Signing and Encryption (JOSE) in C/C++. JOSE is a framework that allows parties to exchange transfer claims in a secure way. The CJOSE library has been ported to work with wolfSSL, the best tested crypto library on the market.
To build wolfSSL for CJOSE:
./configure --enable-opensslall --enable-aeskeywrap CPPFLAGS='-DHAVE_EX_DATA -DWOLFSSL_KEY_GEN'makemake install
To build CJOSE for wolfSSL:
- Download the appropriate patch from https://github.com/wolfSSL/osp/tree/master/cjose. Choose a patch that corresponds or is closest to your version of cjose.
patch -p1 < <path/to/downloaded/patch>autoreconf./configure --with-wolfssl=/usr/localmake
To verify that this build passes the tests, run:
make check
wolfSSL currently supports CJOSE version 0.6.1, the most recent release. For details on CJOSE, visit https://github.com/cisco/cjose.
This feature has been added in commit 0cfde0794b9c5ab1c01171745b800140ee4f8662.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Open Source Project Ports: OpenLDAP
Because of the exceptional portability of our wolfCrypt library, plus our fantastic team of engineers, we’re able to frequently add new ports. We’ll continue showcasing a few of the latest open-source project ports over the next few weeks!
wolfSSL has been integrated with the OpenLDAP project, which is one of the most popular open-source implementations of LDAP. LDAP (Lightweight Directory Access Protocol) is an industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. OpenLDAP is command-line driven software that allows IT admins to build and manage an LDAP directory. For more information on LDAP and OpenLDAP, visit Introduction to OpenLDAP Directory Services.
This port allows for the use of OpenLDAP with our FIPS-validated crypto library, wolfCrypt. We’ve enabled OpenLDAP to be able to call into wolfSSL through the OpenSSL compatibility layer. You can access the GitHub page here: https://github.com/wolfSSL/osp/tree/master/openldap
Need more? Subscribe to our YouTube channel for access to wolfSSL webinars!
Love it? Star us on GitHub!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL and MIKEY-SAKKE
wolfSSL is implementing MIKEY-SAKKE!
MIKEY-SAKKE is a standard created by the UK government’s National Cyber Security Center (NCSC) designed to enable secure, cross-platform multimedia communications. It is highly scalable, requiring no prior setup between users or distribution of user certificates. It is designed to be centrally-managed, giving a domain manager full control of the security of the system. Even so, it maintains high availability, as calling does not require interaction with centralized architecture.
wolfSSL is a lightweight TLS/SSL library that is targeted for embedded devices and systems. It has support for the TLS 1.3 protocol, which is a secure protocol for transporting data between devices and across the Internet. In addition, wolfSSL uses the wolfCrypt encryption library to handle its data encryption.
Secure communications are needed across all governments, so governments create policies encouraging the development of security solutions. MIKEY-SAKKE is the answer to the security requirements from the UK government to specify secure, open, and patent-free cryptographic methods. This empowers private industry to provide the government with interoperable secure communication solutions. As a result, many private and commercial organizations perceive a sizable advantage to being MIKEY-SAKKE compliant.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
If there is a desire for wolfSSL to include other cybersecurity standards, please let us know!
Weekly updates
Archives
- April 2025 (19)
- March 2025 (22)
- February 2025 (21)
- January 2025 (23)
- December 2024 (22)
- November 2024 (29)
- October 2024 (18)
- September 2024 (21)
- August 2024 (24)
- July 2024 (27)
- June 2024 (22)
- May 2024 (28)
- April 2024 (29)
- March 2024 (21)
- February 2024 (18)
- January 2024 (21)
- December 2023 (20)
- November 2023 (20)
- October 2023 (23)
- September 2023 (17)
- August 2023 (25)
- July 2023 (39)
- June 2023 (13)
- May 2023 (11)
- April 2023 (6)
- March 2023 (23)
- February 2023 (7)
- January 2023 (7)
- December 2022 (15)
- November 2022 (11)
- October 2022 (8)
- September 2022 (7)
- August 2022 (12)
- July 2022 (7)
- June 2022 (14)
- May 2022 (10)
- April 2022 (11)
- March 2022 (12)
- February 2022 (22)
- January 2022 (12)
- December 2021 (13)
- November 2021 (27)
- October 2021 (11)
- September 2021 (14)
- August 2021 (10)
- July 2021 (16)
- June 2021 (13)
- May 2021 (9)
- April 2021 (13)
- March 2021 (24)
- February 2021 (22)
- January 2021 (18)
- December 2020 (19)
- November 2020 (11)
- October 2020 (3)
- September 2020 (20)
- August 2020 (11)
- July 2020 (7)
- June 2020 (14)
- May 2020 (13)
- April 2020 (14)
- March 2020 (4)
- February 2020 (21)
- January 2020 (18)
- December 2019 (7)
- November 2019 (16)
- October 2019 (14)
- September 2019 (18)
- August 2019 (16)
- July 2019 (8)
- June 2019 (9)
- May 2019 (28)
- April 2019 (27)
- March 2019 (15)
- February 2019 (10)
- January 2019 (16)
- December 2018 (24)
- November 2018 (9)
- October 2018 (15)
- September 2018 (15)
- August 2018 (5)
- July 2018 (15)
- June 2018 (29)
- May 2018 (12)
- April 2018 (6)
- March 2018 (18)
- February 2018 (6)
- January 2018 (11)
- December 2017 (5)
- November 2017 (12)
- October 2017 (5)
- September 2017 (7)
- August 2017 (6)
- July 2017 (11)
- June 2017 (7)
- May 2017 (9)
- April 2017 (5)
- March 2017 (6)
- January 2017 (8)
- December 2016 (2)
- November 2016 (1)
- October 2016 (15)
- September 2016 (6)
- August 2016 (5)
- July 2016 (4)
- June 2016 (9)
- May 2016 (4)
- April 2016 (4)
- March 2016 (4)
- February 2016 (9)
- January 2016 (6)
- December 2015 (4)
- November 2015 (6)
- October 2015 (5)
- September 2015 (5)
- August 2015 (8)
- July 2015 (7)
- June 2015 (9)
- May 2015 (1)
- April 2015 (4)
- March 2015 (12)
- January 2015 (4)
- December 2014 (6)
- November 2014 (3)
- October 2014 (1)
- September 2014 (11)
- August 2014 (5)
- July 2014 (9)
- June 2014 (10)
- May 2014 (5)
- April 2014 (9)
- February 2014 (3)
- January 2014 (5)
- December 2013 (7)
- November 2013 (4)
- October 2013 (7)
- September 2013 (3)
- August 2013 (9)
- July 2013 (7)
- June 2013 (4)
- May 2013 (7)
- April 2013 (4)
- March 2013 (2)
- February 2013 (3)
- January 2013 (8)
- December 2012 (12)
- November 2012 (5)
- October 2012 (7)
- September 2012 (3)
- August 2012 (6)
- July 2012 (4)
- June 2012 (3)
- May 2012 (4)
- April 2012 (6)
- March 2012 (2)
- February 2012 (5)
- January 2012 (7)
- December 2011 (5)
- November 2011 (7)
- October 2011 (5)
- September 2011 (6)
- August 2011 (5)
- July 2011 (2)
- June 2011 (7)
- May 2011 (11)
- April 2011 (4)
- March 2011 (12)
- February 2011 (7)
- January 2011 (11)
- December 2010 (17)
- November 2010 (12)
- October 2010 (11)
- September 2010 (9)
- August 2010 (20)
- July 2010 (12)
- June 2010 (7)
- May 2010 (1)
- January 2010 (2)
- November 2009 (2)
- October 2009 (1)
- September 2009 (1)
- May 2009 (1)
- February 2009 (1)
- January 2009 (1)
- December 2008 (1)

