RECENT BLOG NEWS
Q&A with wolfSSL’s Engineers
Where do you see crypto heading in the next 10 years? What’s currently on wolfSSL’s roadmap?
Post-Quantum Computing (PQC) cryptographic algorithms are the biggest thing on our radar (See our updates on post-quantum wolfSSH and post-quantum cURL!). We have started with adding the Key Exchange algorithms from liboqs into our TLS implementation, as well as working on an optimized implementation of NTRU. wolfSSL now supports the round 3 finalist KEM algorithms of the NIST PQC competition which are appropriate for TLS 1.3. This means that everyone can experiment with the new up and coming algorithms that will be standardized.
Signatures are more of a problem in the context of TLS, since the CA infrastructure needs to be updated to issue certificates using the PQC algorithms before they can be used.
At the moment, it seems as though all the post-quantum algorithms have disadvantages that make it difficult to drop one in without impact. Some are too slow, while others require too much data to be sent over the wire. Embedded is even harder!
DTLS 1.3 is also on our roadmap further down the line – the specification is done but not published as an RFC yet.
Advice for people who are looking to build security apps or develop secure networking processes?
- Use TLS 1.3. All major browsers, and 47.8% of the most popular web sites, support TLS 1.3.
- Use well known algorithms like AES-GCM, SHA-2, (EC)DH, RSA and ECDSA.
- Use secure, well supported protocols like TLS 1.2 and TLS 1.3, and DTLS 1.2.
- Be prepared to change to new PQC secure algorithms. Quantum computers aren’t possible yet, but when they are, attackers can go back and decrypt old messages.
- Be prepared to sign with two signatures, first with an existing algorithm like RSA or ECDSA, and secondly with a new PQC secure algorithm. The first signature can be verified quickly right now, and the second later, if and when quantum computers come online.
- Keep your private keys safe – in hardware where possible.
For more, check out our interview with ExpressVPN!
Need more? Subscribe to our YouTube channel for access to wolfSSL webinars!
Love it? Star us on GitHub!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
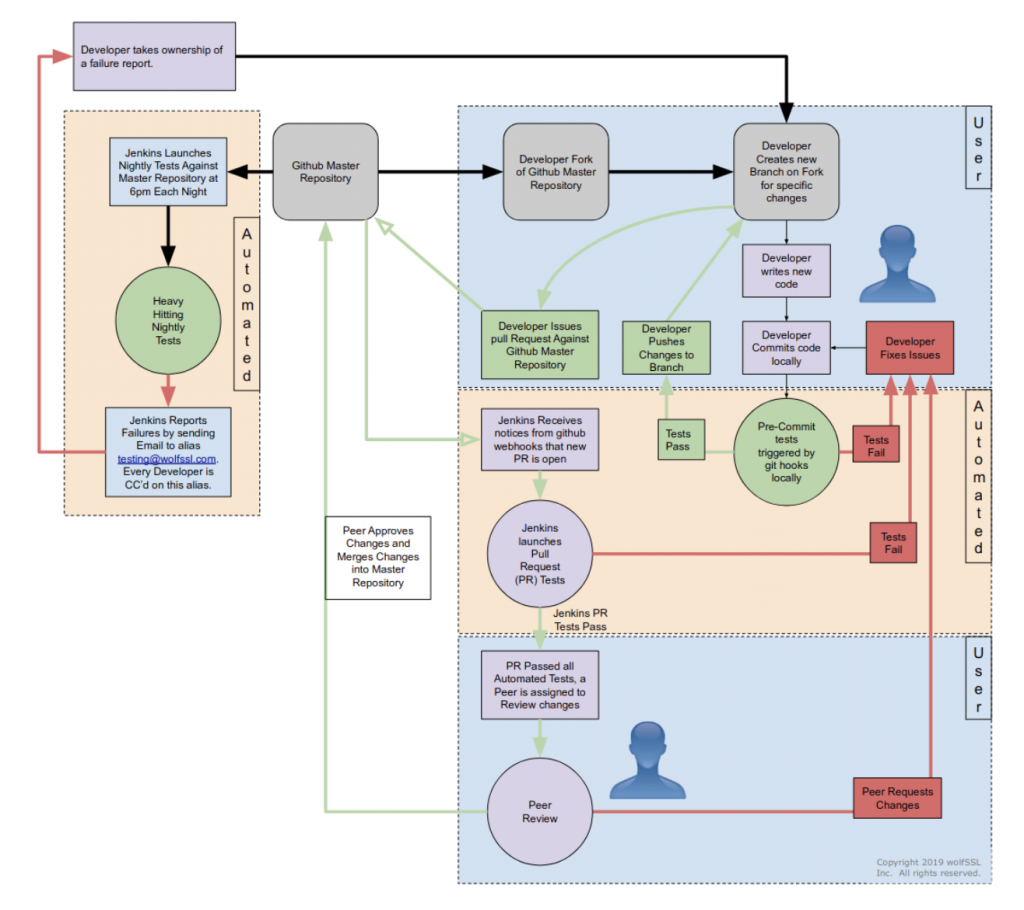
wolfSSL Quality Assurance
The wolfSSL ecosystem consists of several software modules and components, each with specific goals and purposes. We make sure all our software products are engineered using the quality standards required by our process.
Each step in the software lifetime is regulated by strict rules and testing criteria (including stringent fuzz based testing) that ensure the detection of defects and regressions in the code very early.
Quality assurance
The first verification for the functionality of the code is performed locally, on the development PC of the contributor. Git commit and push hooks ensure that the code can be submitted only if it passes a first set of functionality and unit tests. Once the pull request is published, a full round of non-regression and integration tests are automatically started and the status of the pull request is updated with the test results. In order for the pull request to be accepted for inclusion, it must pass the peer review and the non-regression and integration tests. The tests are automatically retriggered during the review process every time that the code for the pull request is modified.
Quality control automation
At wolfSSL we have deployed an hybrid (on-site + cloud based) infrastructure, using Jenkins to coordinate the workload between the nodes to apply quality control on a regular basis. This includes the execution of software tests every time a contribution is evaluated for inclusion in the mainline, as well as other types of quality control applied on a regular basis (e.g. nightly, weekly).
The reason behind the hybrid approach is due to the portability trait of the wolfSSL software ecosystem. The software must run on several different hardware architectures, and interoperate with specific hardware components, such as hardware crypto modules and TPMs. Using physical machines on some of the jenkins nodes provides mechanisms to configure and control specific hardware targets, including microcontroller boards that can be configured and programmed automatically.
Some tests require a long time to run. Continuous integration tools are very useful to split the application of the quality control jobs over a longer time, to ensure that every test is performed on a regular basis.
Formal algorithms and modules verification
In order to validate the correctness and the adherence to the standards implemented, wolfSSL software components are tested using tools and procedures recommended by NIST. This includes a full set of functional tests using a set of well-known input values (test vectors) and expected results. The correctness of many cryptographic algorithms can also be verified by inspecting the intermediate results of the calculations.
NIST also issues a series of publications (FIPS 140) coordinating the requirements and standards for cryptographic modules for use by departments and agencies of the federal Government. Through the effort of specialized accredited third-party laboratories across the U.S. and Canada, two validation programs are made available to certify the compliance with the FIPS 140 regulations. wolfCrypt has achieved the FIPS 140-2 certification, and has already applied for the recently approved FIPS 140-3 certificate. FIPS certification requires that the cryptographic module is successfully submitted through the validation of the two programs:
- Cryptographic Algorithm Validation Program (CAVP) provides validation testing of approved cryptographic algorithms implemented.
- Cryptographic Module Validation Program (CMVP) certifies the module for use by the Government and regulated industries for securing sensitive data and information.
The same types of tests used in CAVP/CMVP are repeated on the mainline automatically, to ensure that modifications in the code do not impact on the integrity of the algorithms and the modules as specified by FIPS 140.
Interoperability tests
One very effective way of verifying that the behavior of the protocols remains the same throughout the continuous integration, is by running interoperability tests with different implementations of the same standards. WolfSSL quality control infrastructure provides a number of scheduled tests that use a different implementation as the remote endpoint of the communication, and to compare results of cryptography operations starting from common vectors.
Unit tests
Unit tests are mandatory for all core modules, and run on the developer’s machine upon new commits.
The coverage of the unit tests is measured on a weekly basis, to ensure that there are no coverage regressions when adding new functionality to the code. WolfSSL developers receive a full code coverage report in their mailboxes every week thanks to the automation provided by the Jenkins infrastructure for continuous integration.
API consistency verification
One specific set of tests verifies that changes in the implementation do not alter the usage of the API from the application development perspective. These tests are never updated, with the only exception of adding new functions to the API. The API must remain consistent across versions, as it is the contract between the application and the library. Verifying all these aspects is the goal of the subset of tests that are running nightly to verify the adherence to the requirements.
Integration tests
Due to wolfSSL portability, it is necessary to expand the test domain by including custom configurations, which require to compile the software for different architectures and combination of compile-time configuration options and test applications. Both real and virtual machines are used as targets for running the test suite. Automating the tests on different architectures (x86, ARM, PowerPC, RISC-V, MIPS, …) ensures that architecture-specific regressions or bugs can be detected and identified early during the process, and the expected behavior remains consistent in all cases. Thanks to the hybrid model of our continuous integration infrastructure, several targets are connected to Jenkins nodes that are in charge of running the software tests through a wide range of specific hardware and software configurations and use cases.
Safety assessment: looking under the hood
The continuous integration infrastructure also automates the execution of several analysis tools.
Static analysis tools look for any inconsistency in the code exploring all the different combinations of compile-time options, and following different code paths. These tools can detect a wide range of programming mistakes, potential errors, and undefined behaviors in the language that may not be covered by the compiler, by applying rigorous checks at the source code level. The tools used by wolfSSL and automated in the CI include cppcheck, clang static analyzer (scan-build), Facebook infer and others.
Memory analysis is performed on a regular basis to look for bugs related to memory handling. WolfSSL uses valgrind memcheck tool, clang sanitizer and other dynamic analysis to run the code. These tools detect memory errors such as accessing uninitialized or previously freed memory, using undefined or uninitialized values, memory leaks and more.
Fuzzers are a very important resource to improve the robustness of the code towards unexpected situations. The goal of these tools is to attempt to cause malfunctions in the code by injecting a large number of random inputs in quick succession. Fuzzing is often a very effective way to detect bugs and vulnerabilities in the code that could go unnoticed for a long time. At wolfSSL we constantly run fuzzers to feed the API functions and the transport back-end, periodically rotating all the possible seed values for the PRNG regulating the output values mutation. With mutation-fuzzing, a bug that is triggered with a given seed value can be reproduced by relaunching the same test with the same seed value manually, allowing for easy reproducibility and analysis through instruments and debuggers. Since these kind of tools must be aware of the application domain, the protocol structures and the characteristics of the data, wolfSSL uses two main fuzzers that have been written for the purpose. WolfFuzz operates over memory buffers and fuzzes the internal cryptography operations. This mechanism allows very fast fuzzing and the entire range of 4 trillion PRNG seeds is tested in three months. A second tool, wolfSSL Network Fuzzer, runs over TCP/IP. For this reason it is much slower but more flexible to test the code that enables security for data in motion.
Vulnerability management
At wolfSSL we take vulnerabilities very seriously, and we are committed to release a new version of the software within 36h from the disclosure. This ensures that, in case of responsible disclosure, the vulnerability is fixed way before its details or any proof of concept to reproduce are made public.
A vulnerability claim triggers emergency procedures, consisting in a Standard Operating Procedure (S.O.P.) that has to be completed to speed up the resolution of the issue and the release of a new version. The vulnerability claim is verified within the first 120 minutes. In this phase, a document is created to be distributed internally to the engineering team, to document the issue and all available instruments along with instructions on how to reproduce it so that the error can be confirmed and the proposed fix can also be assessed to determine if the issue has been addressed completely. The fix may take between a few minutes up to 24h, depending on the complexity of the issue. When the fix is ready it is submitted either in the form of a internal patch or a public pull request when it has been determined that the fix will not leak critical information to would-be attackers that monitor the wolfSSL git repository. The path or public PR is then reviewed by multiple engineers, since code changes are still validated through both manual code reviews and the test procedures. After a few iterations in the review process loop, the automated integration server verifies the fix by running all the necessary pre-release tests. At the end of the verifications, if all the test passed, a new release is issued, and all users and customers are notified through all available communication channels.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247. wolfSSL supports TLS 1.3, FIPS 140-2/3, DO-178, and much more!
wolfSSL Software Development Process
The wolfSSL ecosystem consists of several software modules and components, each with specific goals and purposes. We make sure all our software products are engineered using the quality standards required by our process.
Each step in the software lifetime is regulated by strict rules and testing criteria (including stringent fuzz based testing) that ensure the detection of defects and regressions in the code very early.
Software engineering process overview
From a software engineering standpoint, the life cycle of the design and development of wolfSSL software components is structured in three steps:
- Identification and analysis of software requirements and specifications
- API-oriented software design
- Software module development
Each step is then verified through a specific set of quality control procedures, including:
- Unit tests and periodic coverage analysis
- API consistency tests
- Integration tests on multiple architectures/compilers and use cases/combinations of compile time configuration options
- Interoperability tests against other implementations
- Formal algorithm and module verifications
- Fuzz testing
In order to improve the safety of the code, and in order to detect potential defects or misbehaviors, additional quality controls are regularly applied to the software modules, in particular tools like static analyzers, dynamic memory diagnostic tools, fuzzers and more, being added all the time.
Distributing the source code under a GPL license and exposing the entire development process publicly on the GitHub platform guarantees that hundreds of users, contributors and people interested in the project are constantly aware about every change in the code, and the conversations generated during code reviews. Corporate security organizations, cybersecurity partners and academic researchers give very valuable contributions by constantly studying new vulnerabilities and carefully exploring the potential attack surfaces that may be harder to identify while writing the code. wolfSSL Inc. takes vulnerability management very seriously and has a precise and detailed checklists to run in case of emergency fix and rapid release.
Due to the constantly changing nature of the specifications, the software design process must be flexible enough to accommodate updates in the algorithm implementation, the usage recommendations and the guidelines to implement secure protocols and mechanisms.
NIST distributes specifications and guidelines through “Special Publications” (SP). Through its collaboration of industry organizations, government agencies and academic institutions the National Cybersecurity Center of Excellence (NCCoE) as part of NIST. Similarly to IETF publications, the approach of NIST consists in releasing frequent updates and amendments to earlier publications, in order to keep the guidelines updated. The process of updating the guidelines within NIST is regulated by the “NIST Cryptographic standards and guidelines development process” (NIST.IR.7977). Cryptographic functions in wolfCrypt follow the latest specifications from NIST regarding algorithms and their implementation process. As explained later, NIST publications and software tools play an important role in the algorithms and modules verification phase.
WolfMQTT is implemented upon the specifications provided by OASIS, initially covering MQTT version 3.1.1 approved in December 2015. WolfMQTT has since then evolved to support the specifications in OASIS MQTT Version 5.0, approved as the latest MQTT standard in March 2019.
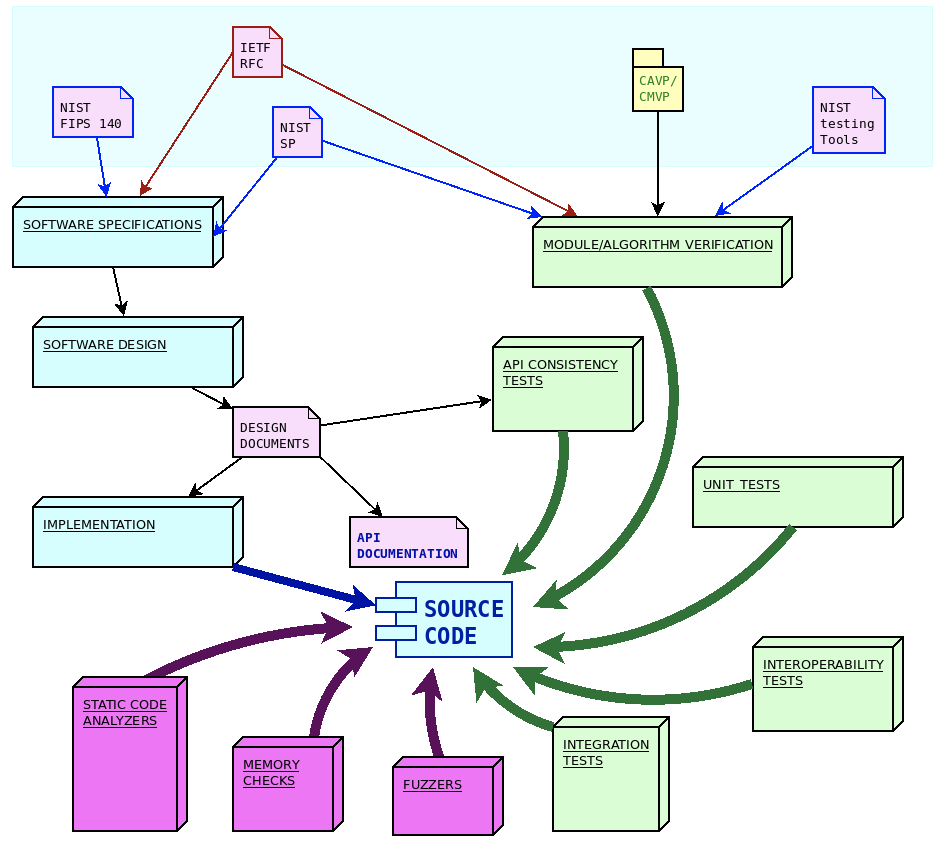
Software requirements and specifications
The guidelines for the implementation of cryptography, secure communication protocols and secure firmware updates mechanisms are described by open standards. These standards are maintained and documented by several organizations. WolfSSL software projects import specification documents from three major organizations, namely:
- IETF, the Internet Engineering Task Force, a large open international community of engineers, in charge of publishing and updating the documentation for the Internet protocols stack, which nowadays also includes secure communication protocols and algorithms used in ciphersuites
- NIST, the United States National Institute of Standards and Technology, providing guidelines for processes, modules and algorithms, recognized globally as best-practices in cryptography
- OASIS, the Organization for the Advancement of Structured Information Standards, a global nonprofit consortium that works on the development of open standards for the IoT and data exchange
IETF releases new specifications in the form of “Request for Comments” (RFC). These are individually numbered publications which are published after a peer review process, which often requires multiple draft phases. Once a RFC is assigned its unique number, it is never modified again. In order to update a standard track that has been published in a RFC, it is possible to issue a new RFC that may contain amendments, corrections or replacing of existing RFCs that were previously published. Newer RFCs can supersede older ones by making them obsolete or deprecated. RFCs cover the specifications for a large part of wolfSSL communication modules, such as the TLS protocol standard (RFC8446), DTLS (RFC6347), TLS extensions (RFC6066) and several others. The wolfCrypt library follows the recommendations for the implementation of the cryptographic primitives based on the algorithms supported, such as RSA public-key cryptography (RFC8017), or the ChaCha20/Poly1305 for AEAD (RFC8439) and many others. WolfSSH has been designed and developed upon the specifications of the RFC4250-RFC4254 series, documenting SSH-2 as proposed internet standard. WolfBoot has been initially designed and developed according to the guidelines of the draft-ietf-suit-architecture, which later on became RFC9019.
Software design
Most of the software components developed by wolfSSL are in the form of a structured library, with an API oriented design. Once functions are part of the API they will never change their signature, their purpose or the meaning of their return values. This ensures compatibility across different versions of the library. If a feature is added to an existing functionality, a new API function is created, which accepts different arguments, or extends specific interfaces. The API function calls are formally documented in the module user manual.
One of the most important aspects to keep in mind during the design phase is the correct meaning, propagation and verification of the error codes across the different layers of the API. Each error code has unique and well-defined meanings that are explained in the manual. This facilitates the identification of run-time errors in the application using the library.
Due to the dynamic, changing nature of the specifications around cryptography and secure protocols, the design process must adapt accordingly. New specifications are analyzed and integrated in the existing module architecture, ensuring that this does not break existing features by keeping the existing API function signatures immutable in time.
Software development and traceability
All software at wolfSSL is developed and maintained following the continuous integration practice, via a centralized git mainline repository. All source code is public and accessible at any time during the development, under a GPL license.
The life-cycle of software components in the wolfSSL ecosystem is different from the typical open-source development process, and it is designed to comply with modified condition decision coverage (MC/DC) process. WolfSSL owns and maintains the entire code base, which means that there are strict rules in place regarding changes and updates of the mainline. Modifications to the repositories are only allowed by wolfSSL engineers, who also have to comply with a strict peer-review policy before any change is merged into the master branch.
To contribute to wolfSSL repositories, a developer must submit a “pull request” through GitHub. The request is then reviewed by one or more wolfSSL engineers (depending on the size, the impact and the nature of the patch). This often results in requests for alignment with the purposes in the design documents, changes in the code, re-adaptations and improvements before the code is accepted for merging. Only approved contributors are allowed to submit their code to review. Contributors outside the wolfSSL engineering team must be approved beforehand before the code is considered for inclusion.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL support for the ATECC608 Crypto Coprocessor
wolfSSL embedded SSL/TLS support the latest Microchip ATECC508 and ATECC608 I2C cryptographic coprocessors.
Prerequisites:
- Requires the Microchip CryptoAuthLib (https://github.com/MicrochipTech/cryptoauthlib.git)
Examples:
- wolfSSL uses PK (Public Key) callbacks for the TLS crypto operations
- wolfCrypt uses the WOLFSSL_ATECC508A or WOLFSSL_ATECC608A macros to enable native `wc_ecc_*` API support
- The README.md and reference PK callbacks can be found here: https://github.com/wolfSSL/wolfssl/tree/master/wolfcrypt/src/port/atmel
- Additional demos for wolfSSL TLS Client/Server and wolfCrypt test/benchmarks can be found: https://github.com/wolfSSL/microchip-atecc-demos
Preprocessor Macros:
- WOLFSSL_ATECC508A
- WOLFSSL_ATECC608A
- WOLFSSL_ATECC_PKCB
- WOLFSSL_ATMEL
- WOLFSSL_ATECC_DEBUG
- WOLFSSL_ATECC_TNGTLS
PK Callbacks:
wolfSSL’s TLS layer PK callbacks expose API’s to set ECC callbacks. These are enabled with:
#define HAVE_PK_CALLBACKS or ./configure --enable-pkcallbacks.
Reference API’s:
- atcatls_create_key_cb
- atcatls_verify_signature_cb
- atcatls_sign_certificate_cb
- Atcatls_create_pms_cb
We plan on adding support for the new 608A PRF and HKDF for TLS 1.2 and TLS 1.3 speed improvements.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfCrypt FIPS 140-2 on ARM
FIPS validating a crypto library on a resource-constrained device can be more involved than doing a validation on a standard desktop-like platform. Variances in OS, Flash/RAM, filesystem (or lack of), entropy, communication, and more can make things interesting. Going through our past ARM-based validations, we have figured out how to make this process easier with wolfCrypt!
If you are interested in exploring FIPS 140-2 cryptography validations on ARM platforms.
To learn more about our FIPS 140-3 certification, please register for our webinar on October 14th!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Open Source Project Ports: Socat
Thanks to the portability of our wolfCrypt library, plus our team of expert engineers, wolfSSL is frequently adding new ports. Keep an eye out as we continue showcasing a few of the latest open source project ports over the next few weeks!
We have recently integrated wolfSSL with the socat tool for Linux. This port allows for the use of socat with our FIPS-validated crypto library, wolfCrypt. Socat is a command line based utility that allows for bidirectional data transfers between two independent channels. For more information on socat, please visit the project’s website at www.dest-unreach.org/socat.
As of wolfSSL version 4.8.0, we have enabled socat to be able to call into wolfSSL through the OpenSSL compatibility layer. You can access the GitHub page here: https://github.com/wolfSSL/osp/tree/master/socat
Need more? Subscribe to our YouTube channel for access to wolfSSL webinars!
Love it? Star us on GitHub!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Post-Quantum wolfSSH
The wolfSSL library is now safe against the “Harvest Now, Decrypt Later” post-quantum threat model with the addition of our new TLS 1.3 post-quantum groups. But where does that leave wolfSSH? It is still only using RSA and elliptic curve key exchange algorithms which are vulnerable to the threat model mentioned above.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Loading wolfSSL into the Linux Kernel – Update
wolfSSL Linux kernel module support has grown by leaps and bounds, with new support for public key (PK) cryptographic acceleration, FIPS 140-3, accelerated crypto in IRQ handlers, portability improvements, and overall feature completeness.
The module provides the entire libwolfssl API natively to other kernel modules, allowing fully kernel-resident TLS/DTLS endpoints with in-kernel handshaking. Configuration and building is turnkey via the --enable-linuxkm option, and can optionally be configured for cryptographic self-test at load time (POST), including full FIPS 140-3 core hash integrity verification and self-test.
As with library builds, the kernel module can be configured in detail to meet application requirements, while staying within target capabilities and limitations. In particular, developers can opt to link in only the wolfCrypt suite of low level cryptographic algorithms, or can include the full TLS protocol stack with TLS 1.3 support.
For PK operations, the kernel module leverages our new function-complete SP bignum implementation, featuring state of the art performance and side channel attack immunity. AVX2 and AES-NI accelerations are available on x86, and are usable from both normal kernel threads and from interrupt handler contexts. When configured for AES-NI acceleration, the module delivers AES256-GCM encrypt/decrypt at better than 1 byte per cycle.
Kernel module builds of libwolfssl are supported in wolfSSL release 4.6 and newer, and are available in our mainline github repository, supporting the 3.x, 4.x, and 5.x Linux version lines on x86-64, with limited support for ARM and MIPS. Full FIPS 140-3 support on x86-64 will be available in the forthcoming wolfSSL Version 5.0 release.
Need more? Subscribe to our YouTube channel for access to wolfSSL webinars!
Love it? Star us on GitHub!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL not affected by CVE-2021-3711, nor CVE-2021-3712
It came to our attention that OpenSSL just published two new vulnerabilities.
- CVE-2021-3711 – “SM2 decryption buffer overflow” (nakedsecurity)
- CVE-202103712 – “Read buffer overruns processing ASN.1 strings.” (nakedsecurity)
These were specific OpenSSL issues and do not affect wolfSSL. For a list of CVEs that apply to wolfSSL please watch the security page on our website here: https://www.wolfssl.com/docs/security-vulnerabilities/
We wanted to take this opportunity to remind our customers and users that wolfSSL is in no way related to OpenSSL. wolfSSL was written from the ground up and is a unique SSL/TLS implementation.
That being said, wolfSSL does support an OpenSSL compatibility layer allowing OpenSSL users to drop in wolfSSL but continue to use the most commonly found OpenSSL API’s after re-compiling their applications to link against wolfSSL.
One individual also pointed out the time delta between report and fix on the above CVEs and wolfSSL would like to remind our customers and users of how proud we are of our less than 48 hour delta between report and fix. For more on our response time and process regarding vulnerabilities check out https://www.wolfssl.com/everything-wanted-know-wolfssl-support-handles-vulnerability-reports-afraid-ask/
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfCrypt FIPS on EFM32-GG
A quick followup to the post “wolfSSLs’ Proprietary ACVP client”.
wolfSSL Inc. is proud to announce a recent addition to the wolfCrypt FIPS cert 3389!
- CMSIS-RTOS2 v2.1.3 running on a Silicon Labs EFM32G (Giant Gecko) chipset with wolfCrypt v4.6.1
Testing and standup for the EFM32 Giant Gecko was done collaboratively between wolfSSL Inc. and one of wolfSSLs’ customers. wolfCrypt had not previously been ported to or run on an EFM32 device so this was an exciting opportunity to both test on an EFM32 for the first time and to take wolfCrypt, running on the EFM32, through FIPS certification!
If you have any questions about getting wolfCrypt or wolfSSL up and running on your EFM32 target, not only is it possible, it is possible with FIPS 140-2 (and soon FIPS 140-3) certification as well!
Other OE’s added since the original ACVP client post are:
- Linux 4.14 running on ARMv8 Cortex A53 with and without PAA (module version 4.5.4)
- Windows CE 6.0 running on ARM Cortex-A8 (module version 4.6.2)
- Linux 4.19 running on ARMv8 Cortex A53 with and without PAA (module version 4.5.4)
At the time of this posting wolfSSL has:
- 10 OE additions (1SUB) in coordination phase with the CMVP to be added to cert 3389
- 4 OE additions (1SUB) that have completed all testing and are ready to be submitted to the CMVP
- 5 OE additions (1SUB) actively in the testing process
- 1 OE addition (1SUB) in the queue to start
While the CMVP is no longer accepting 3SUB and 5SUB submissions for FIPS 140-2 (Cutoff date was 22 Sep 2021) wolfSSL Inc. continues to work on 1SUB OE additions. wolfSSL Inc. will continue to work on 1SUB OE additions to cert 3389 until 7 months before the expiration date of cert 3389.
wolfSSL Inc. was one of the first to submit for FIPS 140-3 and we expect to be one of the first to receive a 140-3 certificate. If you are looking for a commercial FIPS 140-3 solution, then look no further!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Weekly updates
Archives
- April 2025 (19)
- March 2025 (22)
- February 2025 (21)
- January 2025 (23)
- December 2024 (22)
- November 2024 (29)
- October 2024 (18)
- September 2024 (21)
- August 2024 (24)
- July 2024 (27)
- June 2024 (22)
- May 2024 (28)
- April 2024 (29)
- March 2024 (21)
- February 2024 (18)
- January 2024 (21)
- December 2023 (20)
- November 2023 (20)
- October 2023 (23)
- September 2023 (17)
- August 2023 (25)
- July 2023 (39)
- June 2023 (13)
- May 2023 (11)
- April 2023 (6)
- March 2023 (23)
- February 2023 (7)
- January 2023 (7)
- December 2022 (15)
- November 2022 (11)
- October 2022 (8)
- September 2022 (7)
- August 2022 (12)
- July 2022 (7)
- June 2022 (14)
- May 2022 (10)
- April 2022 (11)
- March 2022 (12)
- February 2022 (22)
- January 2022 (12)
- December 2021 (13)
- November 2021 (27)
- October 2021 (11)
- September 2021 (14)
- August 2021 (10)
- July 2021 (16)
- June 2021 (13)
- May 2021 (9)
- April 2021 (13)
- March 2021 (24)
- February 2021 (22)
- January 2021 (18)
- December 2020 (19)
- November 2020 (11)
- October 2020 (3)
- September 2020 (20)
- August 2020 (11)
- July 2020 (7)
- June 2020 (14)
- May 2020 (13)
- April 2020 (14)
- March 2020 (4)
- February 2020 (21)
- January 2020 (18)
- December 2019 (7)
- November 2019 (16)
- October 2019 (14)
- September 2019 (18)
- August 2019 (16)
- July 2019 (8)
- June 2019 (9)
- May 2019 (28)
- April 2019 (27)
- March 2019 (15)
- February 2019 (10)
- January 2019 (16)
- December 2018 (24)
- November 2018 (9)
- October 2018 (15)
- September 2018 (15)
- August 2018 (5)
- July 2018 (15)
- June 2018 (29)
- May 2018 (12)
- April 2018 (6)
- March 2018 (18)
- February 2018 (6)
- January 2018 (11)
- December 2017 (5)
- November 2017 (12)
- October 2017 (5)
- September 2017 (7)
- August 2017 (6)
- July 2017 (11)
- June 2017 (7)
- May 2017 (9)
- April 2017 (5)
- March 2017 (6)
- January 2017 (8)
- December 2016 (2)
- November 2016 (1)
- October 2016 (15)
- September 2016 (6)
- August 2016 (5)
- July 2016 (4)
- June 2016 (9)
- May 2016 (4)
- April 2016 (4)
- March 2016 (4)
- February 2016 (9)
- January 2016 (6)
- December 2015 (4)
- November 2015 (6)
- October 2015 (5)
- September 2015 (5)
- August 2015 (8)
- July 2015 (7)
- June 2015 (9)
- May 2015 (1)
- April 2015 (4)
- March 2015 (12)
- January 2015 (4)
- December 2014 (6)
- November 2014 (3)
- October 2014 (1)
- September 2014 (11)
- August 2014 (5)
- July 2014 (9)
- June 2014 (10)
- May 2014 (5)
- April 2014 (9)
- February 2014 (3)
- January 2014 (5)
- December 2013 (7)
- November 2013 (4)
- October 2013 (7)
- September 2013 (3)
- August 2013 (9)
- July 2013 (7)
- June 2013 (4)
- May 2013 (7)
- April 2013 (4)
- March 2013 (2)
- February 2013 (3)
- January 2013 (8)
- December 2012 (12)
- November 2012 (5)
- October 2012 (7)
- September 2012 (3)
- August 2012 (6)
- July 2012 (4)
- June 2012 (3)
- May 2012 (4)
- April 2012 (6)
- March 2012 (2)
- February 2012 (5)
- January 2012 (7)
- December 2011 (5)
- November 2011 (7)
- October 2011 (5)
- September 2011 (6)
- August 2011 (5)
- July 2011 (2)
- June 2011 (7)
- May 2011 (11)
- April 2011 (4)
- March 2011 (12)
- February 2011 (7)
- January 2011 (11)
- December 2010 (17)
- November 2010 (12)
- October 2010 (11)
- September 2010 (9)
- August 2010 (20)
- July 2010 (12)
- June 2010 (7)
- May 2010 (1)
- January 2010 (2)
- November 2009 (2)
- October 2009 (1)
- September 2009 (1)
- May 2009 (1)
- February 2009 (1)
- January 2009 (1)
- December 2008 (1)

