You most probably already know why you would use curl and if I'm right, you're also a fan of using the right tool for the job. But do you know why others use curl and why they switch from other solutions to relying on curl for their current and future data transfers? Let me tell you the top reasons I'm told by users.
Logging and exact error handling
What exactly happened in the transfer and why are terribly important questions to some users, and with curl you have the tools to figure that out and also be sure that curl either returns failure or the command worked. This clear and binary distinction is important to users for whom that single file every transfer is important. For example, some of the largest and most well-known banks in the world use curl in their back-ends where each file transfer can mean a transfer of extremely large sums of money.
A few years ago I helped a money transaction service switch to curl to get that exact line in the sand figured out. To know exactly and with certainty if money had been transferred - or not - for a given operation. Vital for their business.
curl does not have the browsers' lenient approach of "anything goes as long as we get something to show" when it comes to the Internet protocols.
Verbose goodness
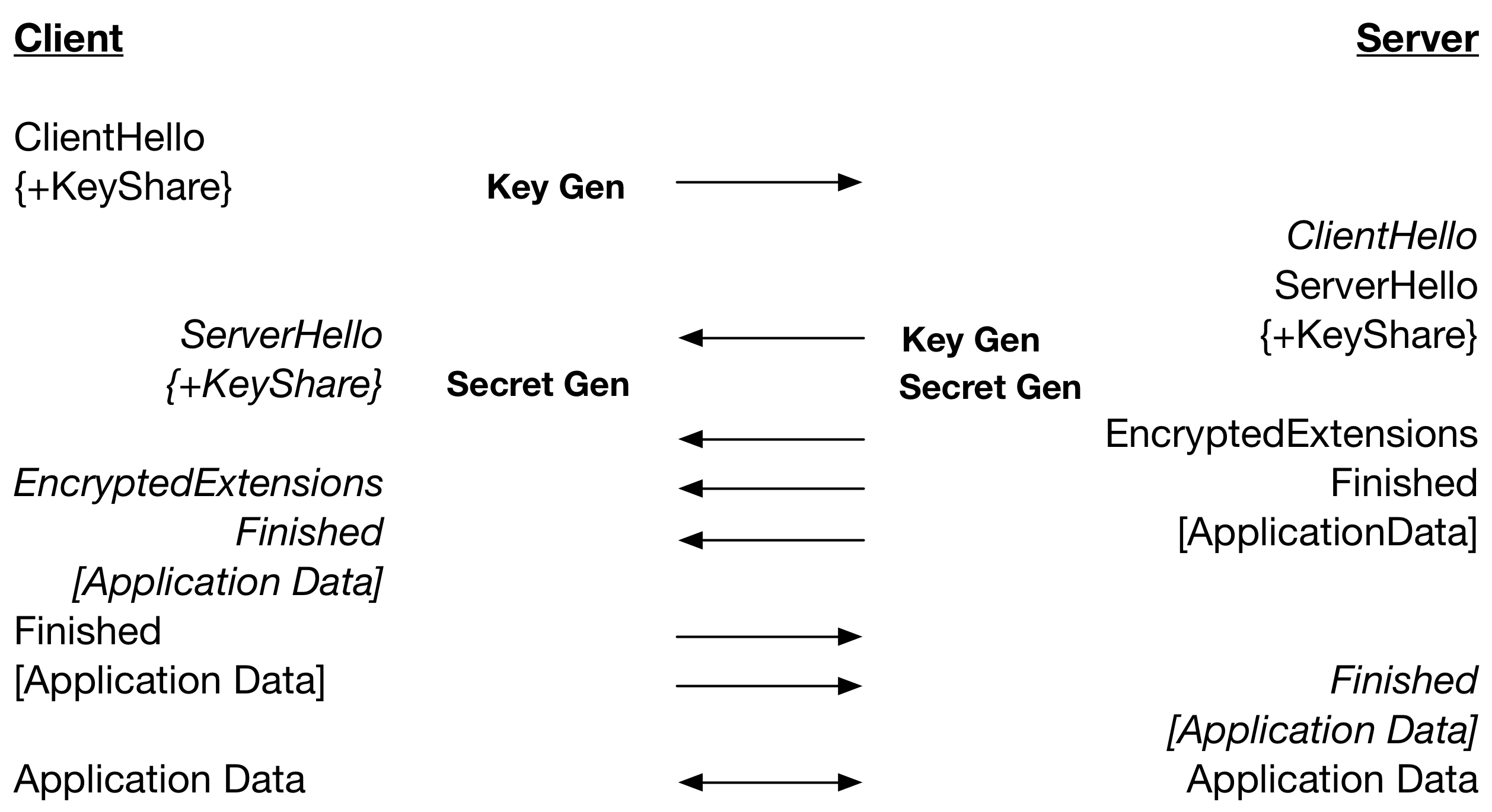
curl's verbose output options allow users to see exactly what curl sends and receives in a quick and non-complicated way. This is invaluable for developers to figure out what's happening and what's wrong, in either end involved in the data transfer.
curl's verbose options allows developers to see all sent and received data even when encryption is used. And if that is not enough, it's SSLKEYLOGFILE support allows you to take it to the next level when you need to.
Same behavior over time
Users sometimes upgrade their curl installations after several years of not having done so. Bumping a software's version after several years and many releases, any software really, can be a bit of a journey and adventure many times as things have changed, behavior is different and things that previously worked no longer do etc.
With curl however, you can upgrade to a version that is a decade newer, with lots of new fancy features and old crummy bugs fixed, only to see that everything that used to work back in the day still works - the same way. With curl, you can be sure that there's an enormous focus on maintaining old functionality when going forward.
Present on all platforms
The fact that curl is highly portable, our users can have curl and use curl on just about any platform you can think of and use it with the same options and behaviors across them all. Learn curl on one platform, then continue to use it the same way on the next system. Platforms and their individual popularity vary over time and we enjoy to allow users to pick the ones they like - and you can be sure that curl will run on them all.
Performance
When doing the occasional file transfer every once in a while, raw transfer performance doesn't matter much. Most of the time will then just be waiting on network anyway. You can easily get away with your Python and java frameworks' multiple levels of overhead and excessive memory consumption.
Users who scan the Internet or otherwise perform many thousands of transfers per second from a large number of threads and machines realize that they need fewer machines that spend less CPU time if they build their file transfer solutions on top of curl. In curl we have a focus on only doing what's required and it's a lean and trimmed solution with a well-documented API built purely for Internet data transfers.
The features you want
The author of a banking application recently explained for us that one of the top reasons why they switched to using curl for doing their Internet data transfers, is curl's ability to keep the file name from the URL.
curl is a feature-packed tool and library that most likely already support the protocols you need and provide the power features you want. With a healthy amount of "extension points" where you can extend it or hook in your custom extra solution.
Support and documentation
No other tool or library for internet transfers have even close to the same amount of documentation, examples available on the net, existing user base that can help out and friendly users to support you when you run into issues. Ask questions on the mailing lists, post a bug on the bug tracker or even show your non-working code on stackoverflow to further your project.
curl is really the only Internet transfer option available to get something that's old and battle-proven proven by the giants of the industry, that is trustworthy, high-performing and yet for which you can also buy commercial support for, today.