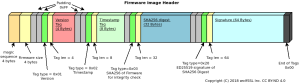
WolfSSL is excited to announce that WolfBoot, our secure bootloader, now supports the STM32H5 microcontroller series. This new integration brings robust secure boot features and efficient update mechanisms to the STM32H5, following the guidelines of RFC9019 for a safe and reliable secure boot solution.
wolfBoot already offers several unique features compared to the SBSFU expansion for STM32Cube, or other open-source secure bootloaders designed uniquely for microcontrollers, like mcuboot.
This includes:
-
A wider selection of cryptographic algorithms for signature verification to choose from
(RSA, ECC, ed25519, ed448). including a few recently added post-quantum algorithms (LMS, XMSS)
-
FIPS 140-2 and FIPS 140-3 certified cryptographic engine
-
Support for bootloader’s self-updates
-
Customizable trust anchor storage, as the keystore containing the public keys can be placed virtually anywhere in the system
-
Support for a large number of secure elements including full support for TPM to implement measured boot
-
Multiple keys allowed to authenticate different components in multiple partitions through a partition access control bitmask
-
The possibility of receiving incremental binary patches to perform delta updates
-
A safety-oriented design, facilitating safety certifications such as ASIL or DO-178C
-
Independence from the update transport mechanism, allowing remote updates over any channel or protocol
-
Flexible and portable keytools command line applications, easy to integrate with any provisioning strategy including third party signing actors and continuous deployment
-
A solid and proven set of countermeasures against specific attacks targeting secure boot mechanisms, such as fault injections and glitch attacks inducing instruction skipping
The STM32H5 series stands out within the STM32 family for its advanced performance and security features. These microcontrollers are built around the Arm Cortex-M33 core, which offers a significant boost in computational power and efficiency compared to previous generations. The STM32H5 series integrates TrustZone-M technology, providing hardware-assisted isolation between secure and non-secure executing domains, which enhances security and simplifies the development of secure applications. The STM32H5 series also offer extensive memory options, with up to 2 MB of flash memory and 640 KB of SRAM, supporting complex and memory-intensive applications. The dual-bank flash memory architecture allows for instant firmware updates by swapping the logical mapping of the two banks. Its advanced cryptographic hardware accelerators, cryptographic grade TRNG complete the picture, making the STM32H5 series an excellent choice for high-performance and secure embedded applications.
wolfBoot extends its support within the STM32 family by including some target-specific security features offered by the STM32H5 series. Let’s explore these features and their role in a system secured using wolfBoot, wolfCrypt and wolfPKCS11.
Secure boot and public key storage in OTP FLASH
The main requirement to secure the boot process consists in a so-called “trust anchor”. RFC6024 specifies the requirements for the management and the storage of the anchor, which must be immutable and immune to tampering, suggesting the use of hardware assisted mechanisms to provide strong protection against tampering and unauthorized access.
STM32H5 provides 2KB of OTP FLASH memory that meets the requirements to properly store the trust anchor. Once the keys are provisioned, the OTP FLASH memory cannot be erased, and can also be explicitly protected against further write access. wolfBoot uses the OTP memory to store the “keystore” structure containing the trust anchors. During the boot process, wolfBoot verifies the firmware’s authenticity against the stored trust anchors. By storing these anchors in OTP memory, wolfBoot ensures that the verification process is based on a reliable and tamper-proof reference.
Once provisioned, the OTP FLASH memory is available for read-only access on STM32H5 at address 0x08FFF000 : 0x08FFF7FF. The memory can be accessed in read-only mode also from the application so the same trust anchors can be also reused for other purposes.
Firmware update via dual bank swapping
STM32H5 FLASH is organized in two banks of the same size, mapped at 0x08000000 and 0x08100000 in non-secure mode and at 0x0C000000 and 0x0C100000 in secure mode. The microcontroller exposes one bit in the configuration registers to swap the mapping of the two banks in the bootloader stage. This feature ensures that the updated firmware can be installed instantly to match its hardcoded boot address. In the example configuration provided in the repository, wolfBoot reserves 256KB of FLASH memory on both banks for the bootloader code and the secure supervisor, so the boot partition has a fixed address after 0x08040000.

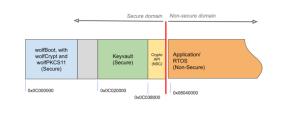
Support for TrustZone-M: wolfCrypt in secure world
TrustZone creates a secure execution environment, separating secure and non-secure code. wolfBoot uses this technology to implement a hypervisor that supports the PKCS#11 standard interface. This allows applications in the non-secure world to perform cryptographic operations without direct access to the cryptographic keys.
In this setup, wolfCrypt and wolfPKCS11 run as the cryptographic engine within the secure domain. The PKCS#11 interface provides a standardized API for cryptographic operations, ensuring that sensitive keys remain protected within the secure world. Applications can thus perform necessary cryptographic tasks while keeping the keys and secrets hidden from non-secure code, enhancing overall security.
wolfBoot configures the Global TrustZone Controller (GTZC) and the Security Attribution Unit (SAU) to separate the FLASH and the RAM available on the system into the two TrustZone domains. The lower half of the total RAM available is reserved for the cryptographic engine to store secret keys and other sensitive data that must not be accessible from the applications, while the upper 320KB are available for the other tasks executing in the non-secure domain.
Each Bank on FLASH memory is divided into secure and non-secure areas. After verifying the integrity and the authenticity of the selected firmware image and swapping the banks accordingly, the selected application or RTOS is executed in the non-secure domain. This basically means that the executing software has limited access to the resources available on the system, including FLASH.
Software running in the non-secure domain cannot access secrets contained in the key vault, which are in the secure-domain portion of the FLASH. Instead, an application will unlock the vault then call TrustZone Non-Secure Callable (NSC) functions through its PKCS11 standard interface, which will then use those secret keys. Each key is referred to as a slot number in the vault. wolfBoot reserves the necessary space to contain the implementation of those PKCS11 API functions in a specific area, marked as NSC in the SAU.
Support for TrustZone-M: wolfCrypt in secure world
The integration of WolfBoot with STM32H5 significantly enhances the security and reliability of an embedded system based on this series. By leveraging TrustZone technology for secure cryptographic operations, utilizing OTP memory for tamper-resistant key storage, and implementing dual bank swapping for seamless firmware updates, wolfBoot provides a robust and efficient, ready to use secure boot solution.
In addition to these features, WolfBoot offers unique capabilities such as support for post-quantum cryptographic (PQC) authentication methods like LMS and XMSS, and protection against glitching attacks, further enhancing its security profile. These features make wolfBoot an ideal choice for developers seeking a secure and reliable bootloader solution for their STM32H5-based projects.
Do you want to know more about secure boot and embedded security? Let’s talk! Send us an email to facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now