In a well-designed modular system there is a dedicated component that performs cryptographic operations. It can be a discrete physical chip, a software library or a mix. Whenever a system component needs a cryptographic operation like hashing, signature verification, encryption, key creation, etc. it delegates the operation to the “cryptographic provider”.
But how to interact with the cryptographic provider?
Ideally, with a (good) standardized application programming interface (API). Having a common interface for cryptographic providers has several advantages: the provider becomes interchangeable, the software is more maintainable and easier to audit, and as a consequence, it’s safer. Unfortunately, designing a good API is an overwhelming task: the abstraction has to be clean and easy to use and read, but at the same time flexible and secure.
Public Key Cryptographic Standard 11 (PKCS#11) and Platform Security Architecture (PSA) Crypto API specifications try to accomplish this daunting task: defining a common API for cryptographic providers.
What about Trusted Platform Module (TPM) 2.0?
The TPM2.0 is aimed at a specific category of cryptographic devices, quoting from the TPM 2.0 specification:
“…a device that enables trust in computing platforms in general”. A TPM is a device that, besides normal cryptographic functions, provides the necessary foundation to enable device identification and overall system integrity reporting. Very early stages of software typically use it in a platform to establish a Root of Trust and allow secure boot and remote attestation features. So while PSA and PKCS#11 both define only an API to access cryptographic providers, TPM2.0 has a much larger scope, as it defines the system architecture to achieve the “trust” of the platform alongside the interface with the TPM device. Moreover, the interface to the TPM is described in terms of commands and responses that a compliant TPM device will understand, unlike PKCS#11 and PSA where the interface is described using C function prototypes and data structure.
But even if PKCS#11 and PSA are both C-based, they show several differences in how they model the cryptographic operations and the terminology used. As an example, PKCS#11 uses a hierarchical sophisticated object model to represent keys, algorithms (called mechanisms), devices (called tokens), etc, while PSA Crypto aims for a more flat and simpler model, where algorithms and keys are just a typedef of an integer type.
wolfSSL support for TPM2.0, PKCS#11 and PSA
Regarding TPM 2.0, wolfTPM library abstracts away the details of the communication with the device and exposes a 1:1 mapping of the TPM commands defined in the specification, plus wrappers that hide away the complexity of using the commands directly.
For PKCS#11 and PSA Crypto API wolfSSL can both expose its functionality using the defined interface and consume cryptographic functions from a provider of the interface.
This not only means that wolfSSL can use cryptographic providers that expose one of the three interfaces, not only that wolfSSL can be used by any software that uses one of the three interfaces, but that wolfSSL can also act as a sort of polyglot translator between software components!
You can refer to here as an example of this, where an application can use wolfPKCS11 to talk with a TPM, thanks to wolfCrypt using wolfTPM to talk with the latter. I report here a diagram of the article as a reference:
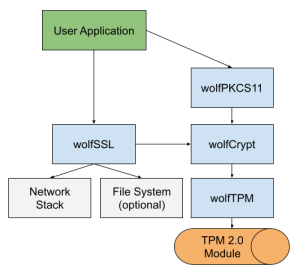
So no matter what interfaces you need, wolfSSL has you covered! Do you need more info about a specific use-case? Do you have any suggestions? or if you have questions about any of the above, feel free to drop a line at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now


