wolfSSL provides support for use with the Espressif IoT Development Framework (ESP-IDF). It includes benchmark, client, server, and test example applications that can be used and tested with the ESP-IDF. Additionally, wolfSSL also provides support for using the hardware encryption acceleration features that are in place on some of the Espressif devices, most notably (and only, at the moment) the Espressif ESP32.
wolfSSL ESP32 Support
The wolfSSL embedded SSL/TLS library has support for running on the Espressif ESP32 platform. In addition to the portability and memory advantages to using wolfSSL on ESP32, wolfSSL supports the hardware cryptography module on ESP32-WROOM-32 device. Offloading supported cryptography operations into the hardware provides substantial performance increases.
In addition to the hardware cryptography module support, wolfSSL provides a demo program using the ESP32-WROOM-32SE and on-board ATECC608A. The Microchip ATECC608A supports ECC hardware acceleration and protected private key storage. Using wolfSSL, 32SE with ATECC608A users can benefit from both increased ECC performance and secure key storage.
Building wolfSSL with ESP-IDF Support
In order to use wolfSSL with the Espressif ESP-IDF, a development framework for intended for rapidly developing Internet-of-Things (IoT), deploy wolfSSL source files into the IDE by running a script that can be found in the <wolfssl_root>/wolfssl/IDE/Espressif/ESP-IDF/ directory.
To enable ESP32 support after deploying wolfSSL files, define WOLFSSL_ESPIDF and WOLFSSL_ESPWROOM32 or WOLFSSL_ESPWROOM32SE. The WOFLSSL_ESPIDF definition turns on ESP-IDF development framework specific settings. The WOLFSSL_ESPWROOM32 and WOLFSSL_ESPWROOM32SE definitions turn on board-specific settings, such as hardware acceleration or ATECC608A use.
To set up ESP-IDF, please view ESP-IDF's “Get Started" page here: https://docs.espressif.com/projects/esp-idf/en/latest/get-started/index.html.
Example ESP-IDF Projects
The wolfSSL package ships with several example ESP-IDF projects which developers can use to get going quickly with wolfSSL on ESP32. The following ESP-IDF example projects can be found under <wolfssl_root>/IDE/Espressif/ESP-IDF/examples:
- wolfCrypt benchmark
This project builds the wolfCrypt benchmark application that can be used on an ESP32 based device to see cryptography algorithm benchmarks.
- wolfCrypt cryptography test
This application tests the wolfCrypt cryptography modules. It is generally a good idea to run this first on an ESP32 platform after compiling wolfSSL in order to verify all underlying crypto is working correctly.
- wolfSSL client/server
These applications are simple TLS client/server example programs using Wi-Fi connections. When testing the embedded client or server on an ESP32 device, it is recommended to test against one of the standard wolfSSL example applications running on a desktop machine.
Note 1: These examples can be found under <esp-idf_root>/examples/protocol/ after deploying wolfSSL files.
ESP32 Hardware Cryptography
Supported cryptographic algorithms accelerated in hardware through the ESP32 include AES, SHA and RSA primitives (large-number modular exponentiation, large-number modular multiplication and large-number multiplication). For details regarding the ESP32 hardware acceleration, please refer to the ESP32 Technical Reference Manual.
The following benchmarks were gathered using the wolfCrypt benchmark application running on an ESP32-WROOM-32 device.
Software crypto:
AES-128-CBC-enc 1 MB took 1.001 seconds, 1.146 MB/s AES-128-CBC-dec 1 MB took 1.017 seconds, 1.104 MB/s AES-192-CBC-enc 1 MB took 1.018 seconds, 1.055 MB/s AES-192-CBC-dec 1 MB took 1.006 seconds, 1.019 MB/s AES-256-CBC-enc 1000 KB took 1.000 seconds, 1000.000 KB/s AES-256-CBC-dec 975 KB took 1.007 seconds, 968.222 KB/s AES-128-GCM-enc 350 KB took 1.055 seconds, 331.754 KB/s AES-128-GCM-dec 350 KB took 1.054 seconds, 332.068 KB/s AES-192-GCM-enc 325 KB took 1.013 seconds, 320.829 KB/s AES-192-GCM-dec 325 KB took 1.013 seconds, 320.829 KB/s AES-256-GCM-enc 325 KB took 1.041 seconds, 312.200 KB/s AES-256-GCM-dec 325 KB took 1.041 seconds, 312.200 KB/s SHA 6 MB took 1.004 seconds, 5.714 MB/s SHA-256 2 MB took 1.006 seconds, 1.747 MB/s SHA-384 1 MB took 1.011 seconds, 1.159 MB/s SHA-512 1 MB took 1.009 seconds, 1.161 MB/s HMAC-SHA 6 MB took 1.001 seconds, 5.634 MB/s HMAC-SHA256 2 MB took 1.000 seconds, 1.733 MB/s HMAC-SHA384 1 MB took 1.004 seconds, 1.046 MB/s HMAC-SHA512 1 MB took 1.002 seconds, 1.048 MB/s RSA 2048 public 16 ops took 1.056 sec, avg 66.000 ms, 15.152 ops/sec RSA 2048 private 2 ops took 2.488 sec, avg 1244.000 ms, 0.804 ops/sec ECC 256 key gen 4 ops took 1.101 sec, avg 275.250 ms, 3.633 ops/sec ECDHE 256 agree 4 ops took 1.098 sec, avg 274.500 ms, 3.643 ops/sec ECDSA 256 sign 4 ops took 1.111 sec, avg 277.750 ms, 3.600 ops/sec ECDSA 256 verify 2 ops took 1.099 sec, avg 549.500 ms, 1.820 ops/sec
Hardware crypto:
AES-128-CBC-enc 6 MB took 1.004 seconds, 5.958 MB/s AES-128-CBC-dec 5 MB took 1.002 seconds, 5.287 MB/s AES-192-CBC-enc 6 MB took 1.004 seconds, 5.958 MB/s AES-192-CBC-dec 5 MB took 1.002 seconds, 5.287 MB/s AES-256-CBC-enc 6 MB took 1.001 seconds, 5.951 MB/s AES-256-CBC-dec 5 MB took 1.004 seconds, 5.277 MB/s AES-128-GCM-enc 375 KB took 1.067 seconds, 351.453 KB/s AES-128-GCM-dec 375 KB took 1.067 seconds, 351.453 KB/s AES-192-GCM-enc 350 KB took 1.010 seconds, 346.535 KB/s AES-192-GCM-dec 350 KB took 1.009 seconds, 346.878 KB/s AES-256-GCM-enc 350 KB took 1.016 seconds, 344.488 KB/s AES-256-GCM-dec 350 KB took 1.016 seconds, 344.488 KB/s SHA 14 MB took 1.000 seconds, 14.062 MB/s SHA-256 15 MB took 1.000 seconds, 15.234 MB/s SHA-384 17 MB took 1.000 seconds, 17.383 MB/s SHA-512 18 MB took 1.001 seconds, 17.512 MB/s HMAC-SHA 14 MB took 1.000 seconds, 13.818 MB/s HMAC-SHA256 15 MB took 1.001 seconds, 14.951 MB/s HMAC-SHA384 17 MB took 1.001 seconds, 16.683 MB/s HMAC-SHA512 17 MB took 1.000 seconds, 16.943 MB/s RSA 2048 public 20 ops took 1.017 sec, avg 50.850 ms, 19.666 ops/sec RSA 2048 private 4 ops took 1.059 sec, avg 264.750 ms, 3.777 ops/sec ECC 256 key gen 4 ops took 1.092 sec, avg 273.000 ms, 3.663 ops/sec ECDHE 256 agree 4 ops took 1.089 sec, avg 272.250 ms, 3.673 ops/sec ECDSA 256 sign 4 ops took 1.101 sec, avg 275.250 ms, 3.633 ops/sec ECDSA 256 verify 2 ops took 1.092 sec, avg 546.000 ms, 1.832 ops/sec
Note 2: Fast Math library use
Note 3: Model: esp32-wroom-32 CPU speed:240MHz. ESP-IDF: v3.3-beta1-39-g6cb37ecc5(commit hash: 6cb37ecc5). OS: Ubuntu 18.04.1 LTS (Bionic Beaver)
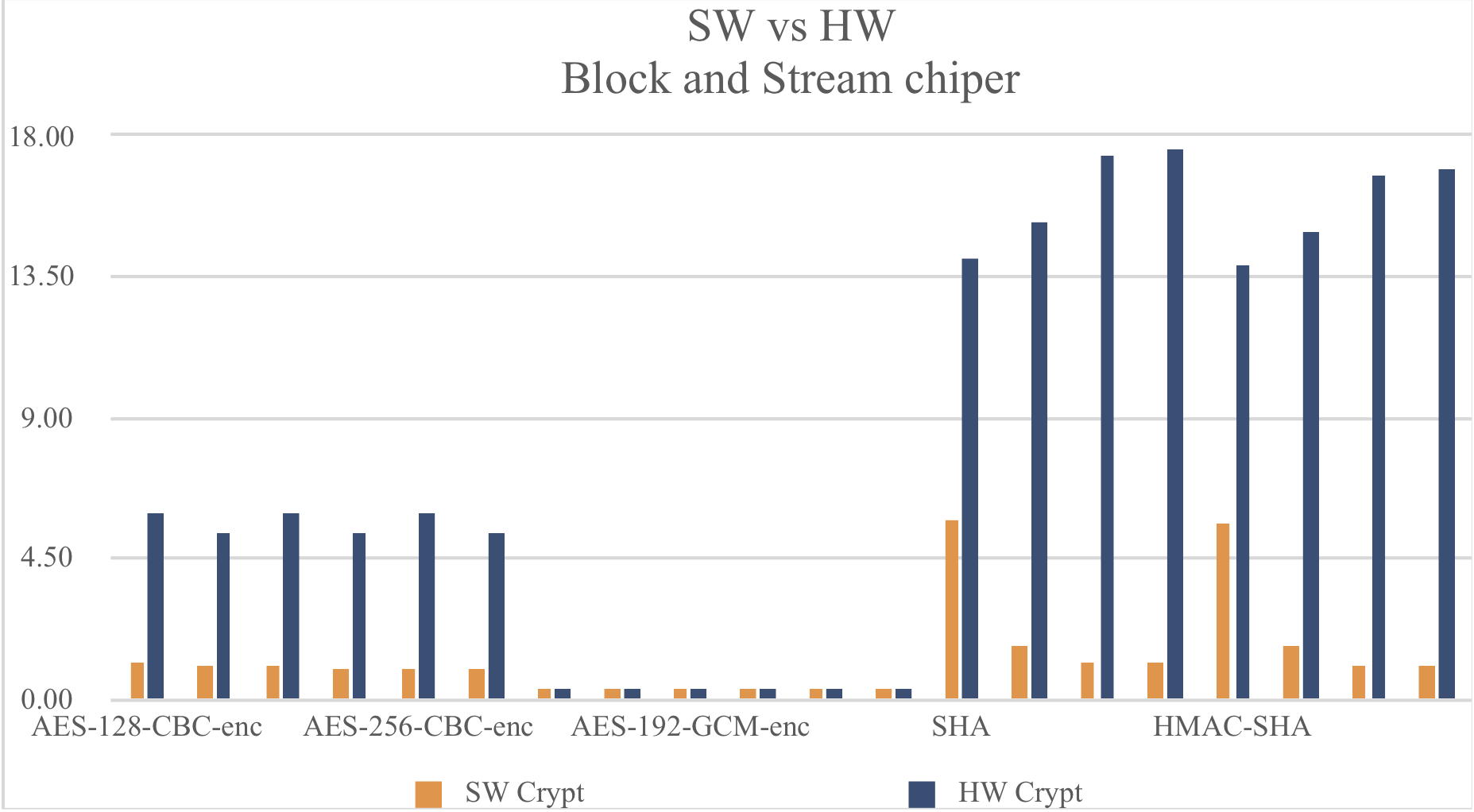
As the above benchmarks show, the hardware-based algorithms on ESP32 demonstrate faster speeds than that of their software counterparts.
ESP32-WROOM-32SE with ATECC608A
The wolfCrypt library has been already ported to include support for the Microchip ATECC508A. Thus, user can benefit by enabling the existing WOLFSSL_ATECC508A and HAVE_PK_CALLBACKS definitions. These definitions are enabled when WOLFSSL_ESPWROOM32SE is defined.
CrptoAuthLib for ATECC608A with ESP-IDF can be found in the project or in the README_32se.md file, located inside <wolfssl-root>/wolfssl/IDE/Espressif/ESP-IDF/ directory.
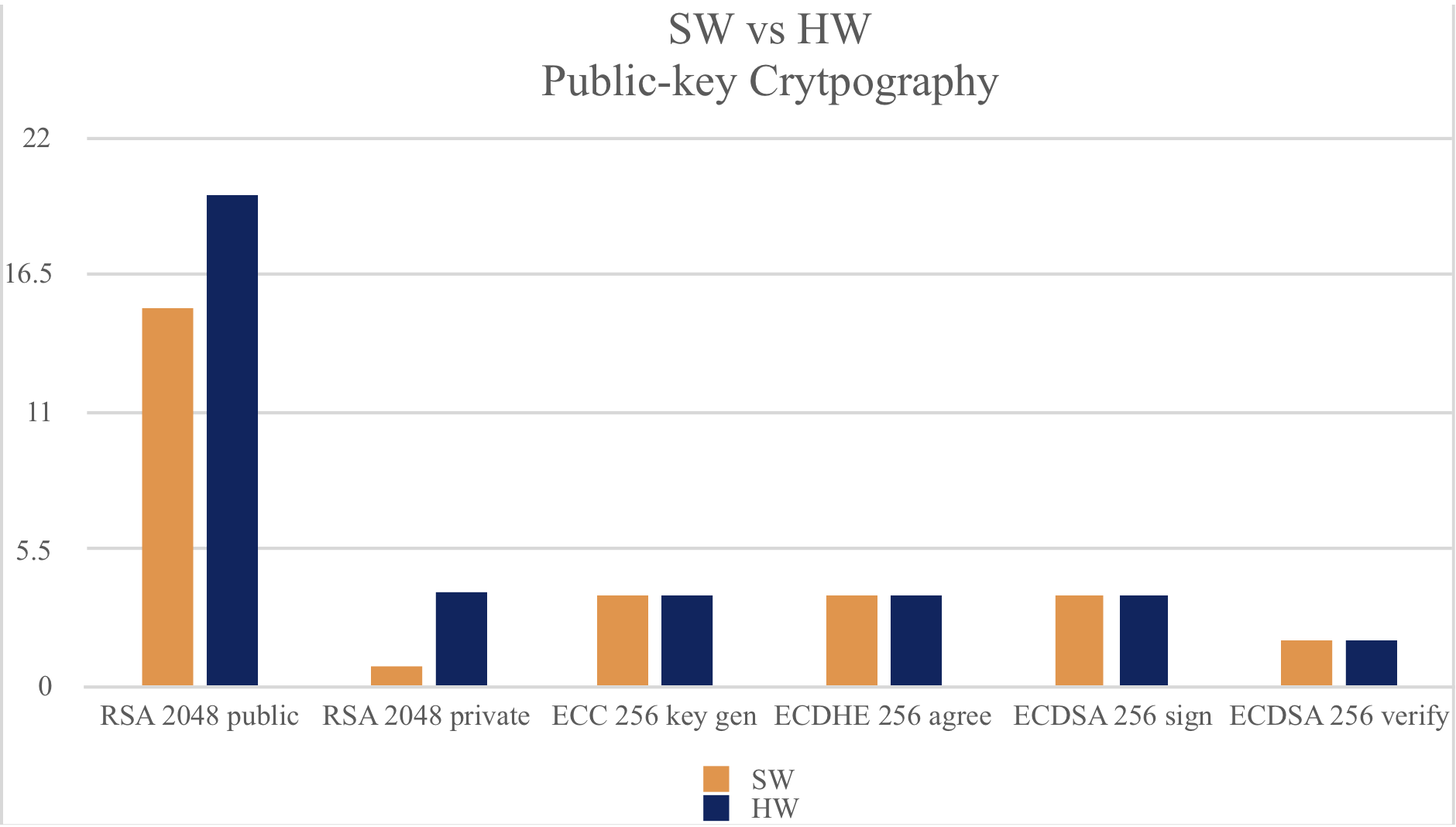
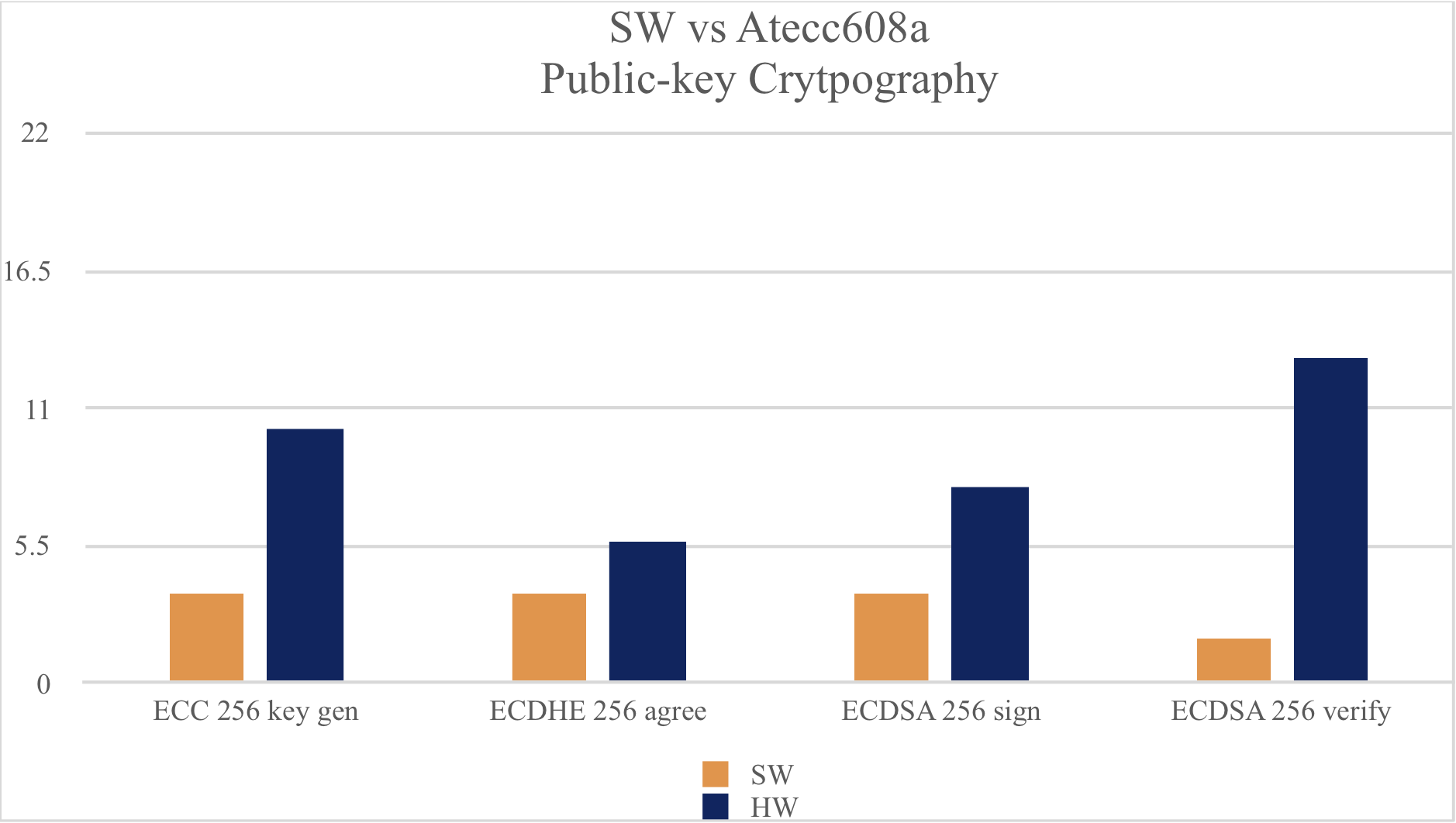
Benchmark values comparing software versus ATECC608A hardware are shown below.
Software Crypto:
ECC 256 key gen 4 ops took 1.092 sec, avg 273.000 ms, 3.663 ops/sec ECDHE 256 agree 4 ops took 1.091 sec, avg 272.750 ms, 3.666 ops/sec ECDSA 256 sign 4 ops took 1.102 sec, avg 275.500 ms, 3.630 ops/sec ECDSA 256 verify 2 ops took 1.091 sec, avg 545.500 ms, 1.833 ops/sec
ATECC608A Accelerated Implementation:
ECC 256 key gen 11 ops took 1.074 sec, avg 97.636 ms, 10.242 ops/sec ECDHE 256 agree 6 ops took 1.068 sec, avg 178.000 ms, 5.618 ops/sec ECDSA 256 sign 8 ops took 1.009 sec, avg 126.125 ms, 7.929 ops/sec ECDSA 256 verify 14 ops took 1.079 sec, avg 77.071 ms, 12.975 ops/sec
Note 4: Fast Math library use
Note 5: Model: esp32-wroom-32se CPU speed:240MHz. ESP-IDF: v3.3-beta1-39-g6cb37ecc5(commit hash: 6cb37ecc5). OS: Ubuntu 18.04.1 LTS (Bionic Beaver)
- TLS establishment time
Software only: 2040.78 milliseconds
SHA, AES and RSA primitive HW accelerated: 997.56 milliseconds
SHA, AES, RSA and w/ ATECC608A: 765.75 milliseconds
Note 6: Software only was gathered under no hardware acceleration and Fast Math library use.
Note 7: Test condition. Server program on the device and TLS v 1.3. Model: esp32-wroom-32se CPU speed:240MHz. ESP-IDF: v3.3-beta1-39-g6cb37ecc5(commit hash: 6cb37ecc5). OS: Ubuntu 18.04.1 LTS (Bionic Beaver)

