wolfSSL has support for the new DTLS 1.3 protocol. You can learn more about this protocol in our “What’s new in DTLS 1.3” blog post (https://www.wolfssl.com/whats-new-dtls-1-3/) and how to use it in our “DTLS 1.3 Examples and Use Cases” blog post (https://www.wolfssl.com/dtls-1-3-examples-use-cases/). In this post we will compare some benchmarks between DTLS 1.2 and 1.3. The biggest differentiators will be the decreased round trips and the use of acknowledgements.
The same ciphers were used for all connections. TLS_AES_256_GCM_SHA384 for DTLS 1.3 and TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 for DTLS 1.2. SECP256R1 was the curve used in both cases.
In all cases, 10 samples were taken and the average of the results was graphed. The error bars represent the standard deviation of the samples.
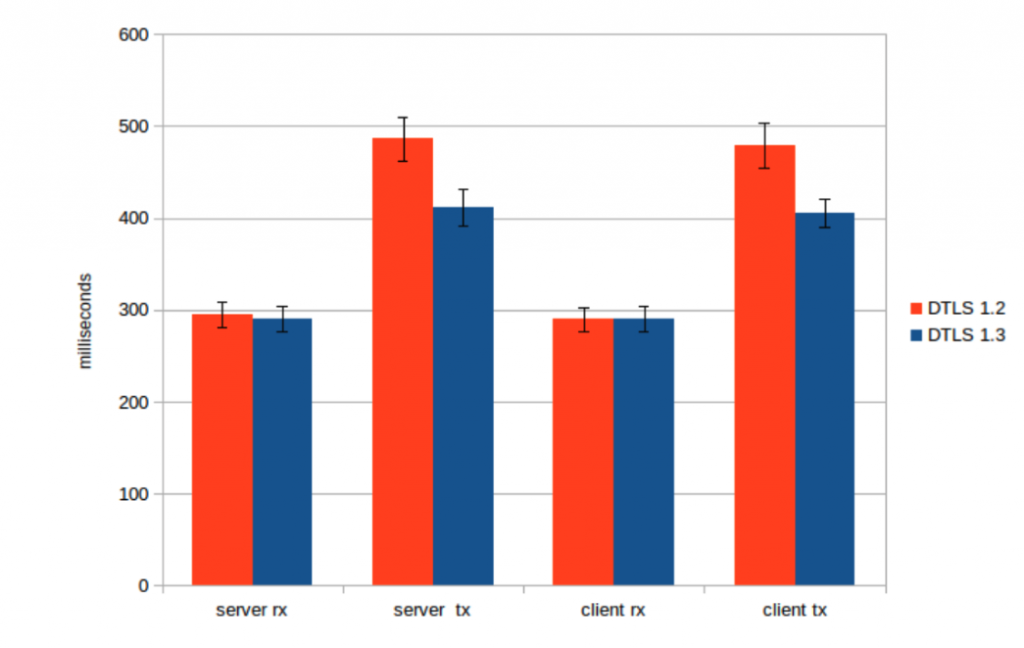
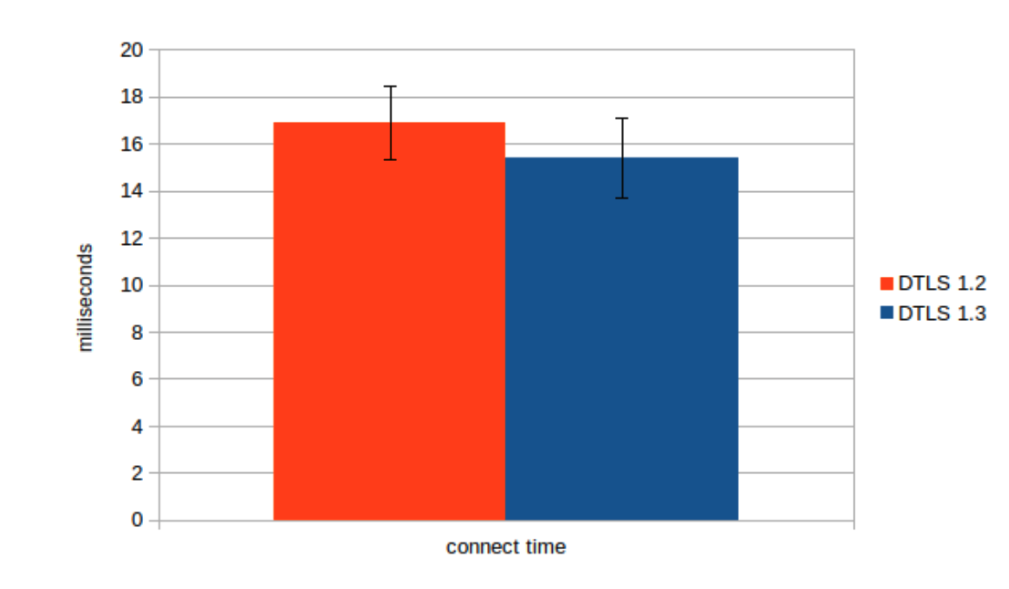
The first graph shows the time it takes to send 15 MB of data in 500 byte packets and the second graph is the time it took to complete the handshake from the client’s perspective. This benchmark was run on one machine without any latency. The throughput of DTLS 1.3 remains very similar to the throughput of DTLS 1.2. There is a slight performance gain that is the result of a more streamlined implementation. The time to complete the handshake remains the same due to the lack of latency. We are glad that the increased security of DTLS 1.3 has not negatively impacted throughput or connection speeds.
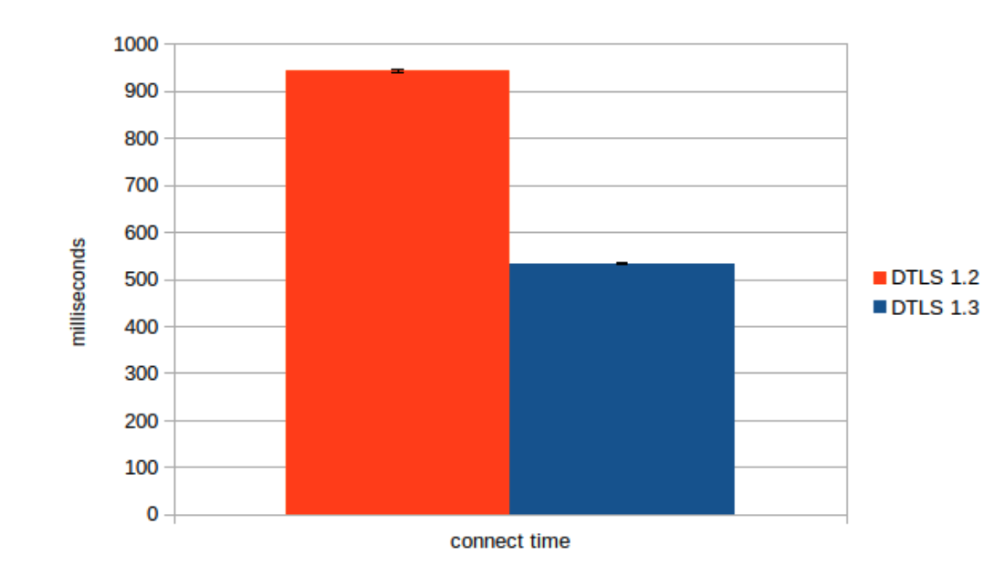
The third graph shows the same time to complete a handshake in the same setup but with a 100 ms latency introduced. The DTLS 1.3 handshake completes in half the time due to the fewer round trips required. After the handshake completes, the peers can start exchanging application data.
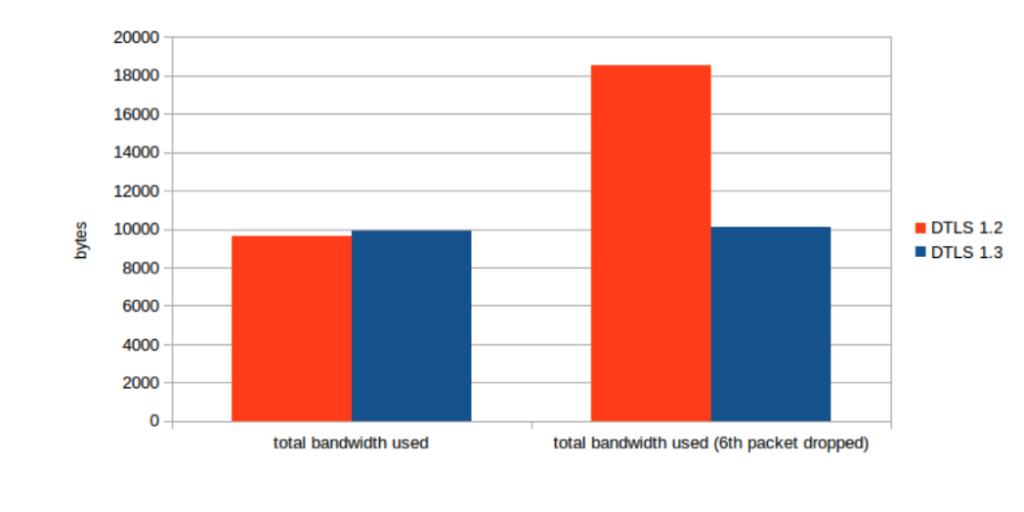
The fourth graph shows the total bandwidth used when a packet is lost. DTLS 1.3 uses about half as much bandwidth when compared to DTLS 1.2. This is achieved by using small acknowledgements to let the peer know what messages were received. The DTLS 1.2 connection needs to resend its entire previous flight to notify the peer that a message was lost and the peer needs to resend its entire previous flight as well because it doesn’t know which packet was dropped.
The improved security parameters of DTLS 1.3 also translate to an increase in performance and efficiency. This is good news for everyone and we are looking forward to moving users from DTLS 1.2 to 1.3! Additionally, DTLS 1.3 gains access to TLS 1.3 features like key updates, post handshake authentication, and post quantum cryptography.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.

