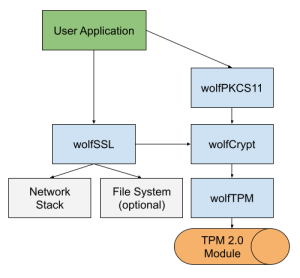
wolfSSL has implemented our own PKCS11 provider library to leverage cryptographic hardware and keystores on various systems. Recently we added support for using a TPM 2.0 module with wolfTPM (see pull request #23). We believe that this functionality is particularly useful for users that have coded to the PKCS11 standard, but need to switch to a TPM or fTPM.
The wolfTPM and wolfPKCS11 libraries are both fully portable to any RTOS or embedded system, including bare-metal. The PKCS11 interface provides a standardized API set for making cryptographic calls to a hardware module. All TPM’s support RSA and ECC keys, so when using a TPM only those two asymmetric algorithms are supported.
Our example PKCS11 applications can run on any Linux or Windows that have a TPM available. If a TPM is not available you can use the TPM simulators (see SWTPM.md). We have also successfully ported it to a bare-metal STM32 target for testing.
A TPM offers physical protection of all private keys and benefits from the TPM performance when doing asymmetric operations like signing, verification or shared secrets. All communication to the TPM uses the parameter encryption feature with AES CFB mode.
If desired the PKCS11 keystore can use the TPM NV for storing the encrypted key material.
Typical implementation including TLS support:
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now

