WOLFCRYPT FIPS 140-3 Available Now!
(Click here for details)
How can wolfSSL help me?
wolfSSL can help you certify your operating environment quickly and cost effectively. wolfCrypt has been validated on more than 80 operating environments (OE’s). wolfSSL can easily add additional OEs to existing wolfCrypt FIPS certificates. To learn more about this process, contact us at fips@wolfSSL.com today!
At wolfSSL, our security experts have the FIPS expertise you need. We will form a FIPS strategy that is best for you, optionally including on-site FIPS consulting! Before you search for a FIPS Consultant or begin calling several of the 22 FIPS Laboratories, contact us. We can save you time, money, and effort by leveraging our certificate instead of obtaining a new one—reducing the process from two years to just 90 days.
wolfSSL also offers FIPS-enabled extensions built on the validated wolfCrypt module. Learn how wolfProvider (OpenSSL 3.x provider) and wolfGuard (FIPS-compliant WireGuard) can extend trusted FIPS security across your environment.
Watch FIPS Training video now!
You can also find answers to common questions in wolfSSL FIPS FAQ, available both online and as a downloadable PDF.
What is FIPS 140-3?
Federal Information Processing Standards (FIPS) 140-3 is a mandatory standard for the protection of sensitive or valuable data within Federal systems.
FIPS 140-3 is an incremental advancement of FIPS 140-2, which standardized on the ISO 19790:2012 and ISO 24759:2017 specifications. Historically, ISO 19790 was based on FIPS 140-2, but has continued to advance since that time. FIPS 140-3 will now point back to ISO 19790 for security requirements. Keeping FIPS 140-3 as a separate standard will still allow NIST to mandate additional requirements on top of what the ISO standard contains when needed.
Among the changes for FIPS 140-3 are conditional algorithm self-tests, where the algorithm self-tests are only performed if used. The pre-operational self-test is now faster, as all the algorithms are not tested until needed. This helps with startup times as the public key self-testing can be time consuming. The self tests can be run at appropriate times for your application startup. Also, there is additional testing of the DRBG entropy sources.
Why is FIPS 140 Important?

Federal agencies purchasing cryptographic-based security systems must confirm an associated FIPS 140-3 certificate exists.
This procurement “check-box” item is a deal breaker. Vendor claims of “designed for FIPS” or “FIPS ready” do not pass this hurdle. Also, be careful with claims of vendor affirmation, as it is frequently a red flag for federal buyers.
No FIPS certificate = No sale
Federal buyers and auditors will also confirm FIPS validation by confirming a match between your certificate's operational environment listings and your product.
What is the status of the wolfSSL FIPS and CAVP validation efforts?
wolfSSL is currently the leader in embedded FIPS certificates. The wolfCrypt module holds the world’s first SP800-140Br1-compliant FIPS 140-3 Validation Certificate. We also maintain ongoing support for two historical FIPS 140-2 certificates for the wolfCrypt Cryptographic Module: #2425 and #3389 (services for product in the field is ongoing). Certificate #3389 includes algorithm support required for TLS 1.3 and can be used in conjunction with the wolfSSL embedded SSL/TLS library for full TLS 1.3 client and server support. Additionally, wolfSSL has obtained FIPS 140-3 Validated Certificate #4718 and #5041. Learn more about FIPS 140-3 in our blog post.
wolfSSL also supports the new ACVP (Automated Cryptographic Validation Protocol), which is the successor to the two decade old CAVP system from NIST. ACVP is intended to alleviate the manual steps of the older CAVP process, creating a more efficient and effective method for cryptographic algorithm testing and validation. Learn more about ACVP in our blog posts here and here.
For additional information contact us at fips@wolfssl.com.
wolfCrypt FIPS 140-3 Level 1 Certificate #5041
wolfCrypt FIPS 140-3 Level 1 Certificate #4718
Historical cert list:
wolfCrypt v4 FIPS 140-2 Level 1 Certificate #3389
wolfCrypt FIPS 140-2 Level 1 Certificate #2425
For a full list of currently validated Operating Environments, please see the section below.
I am a Techie. What is so great about the wolfCrypt FIPS module?
wolfCrypt is a cryptographic software API library. Your application may rely on wolfCrypt to provide all of the cryptographic processing. Instead of performing your own FIPS validation, you may claim that you are using an embedded FIPS cryptographic module. This will make your Federal customers happy.
wolfCrypt is compliant with FIPS 140-3 Implementation Guidance 9.10. We implemented a default entry point to run self-tests automatically. The FIPS OpenSSL module does not provide a default entry point.
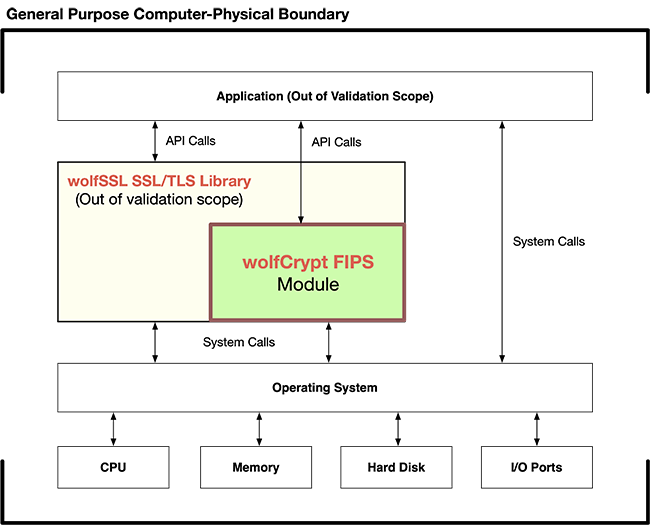
wolfCrypt FIPS Boundary Design
wolfSSL has defined the wolfCrypt FIPS boundary specifically around a subset of the wolfCrypt algorithms such that it is easy and painless to update to new wolfSSL releases while maintaining an existing wolfCrypt FIPS validation. Most bugs and vulnerabilities happen in the SSL/TLS layer code - outside the cryptographic module code itself. With the FIPS boundary drawn around only the wolfCrypt cryptography algorithms, this allows users to update to newer versions of the wolfSSL SSL/TLS code and keep the same validated wolfCrypt FIPS code underneath. With a current wolfSSL support package in place, our FIPS customers receive new wolfSSL SSL/TLS release bundles packaged with their existing validated version of wolfCrypt, making it easy to stay secure and up to date! For Post-Quantum security, wolfSSL has you covered with a reliable, adaptable codebase to keep you ready for future cryptographic standards. Learn more!
Can I get a FIPS certificate in my company’s name?
Yes. You have the option of rebranding the wolfCrypt module and NIST will issue a FIPS 140-3 certificate in your company’s name. Your sales team will thank you.
FIPS 203 and FIPS 204
wolfSSL FIPS Ready
wolfSSL also provides support for a wolfCrypt FIPS Ready version of the library! wolfCrypt FIPS Ready is our FIPS enabled cryptography layer code included in the wolfSSL source tree that you can enable and build. You do not get a FIPS certificate, you are not FIPS approved, but you will be FIPS Ready. FIPS Ready means that you have included the FIPS code into your build and that you are operating according to the FIPS enforced best practices of default entry point, and power on self test.
wolfCrypt FIPS Ready can be downloaded from the wolfSSL download page located here: https://www.wolfssl.com/download/. More information on getting set up with wolfCrypt FIPS Ready can be found in our FIPS Ready User Guide.
Currently Validated Operating Environments
wolfCrypt has been validated on a number of Operating Environments (OEs). The current list of planned OEs for the wolfCrypt FIPS 140-3 certificate (#4718) and the validated OE list for both wolfCrypt FIPS 140-2 certificates (#2425 and #3389) are listed here for reference. wolfSSL can easily add additional OEs to existing wolfCrypt FIPS certificates. To learn more about this process, contact us today!
Certificate #TBD with module v5.2.4 Current OE List:
| Operating System | Processor | Processor Algorithm Acceleration | Product (TBA = To Be Announced at a later time) |
|---|---|---|---|
| IGEL OS 12.8 FIPS (User space) | AMD Ryzen Embedded V2546 | No | HP Elite t755 |
| IGEL OS 12.8 FIPS (Kernel space) | AMD Ryzen Embedded V2546 | No | HP Elite t755 |
Certificate #4718 Current OE List:
| Operating System | Processor | Processor Algorithm Acceleration | Product (TBA = To Be Announced at a later time) |
|---|---|---|---|
| Android 13 | Exynos 9611 without PAA | No | Samsung Galaxy XCover Pro |
| Linux 5.4 | BCM56260B0IFSBG - Sabre2 | No | WTM 4000 |
| Red Hat Enterprise Linux Workstation 8.9 | Intel® Xeon® W-2255 @ 3.7GHz | No | Precision 5820 Tower |
| FreeRTOS v10.4 | Renesas R7FA6E10F | No | Network Interface Card for Aclara RF |
| Linux 5.15 | Freescale i.MX7 Dual Arm Cortex A-7 | No | iSTAR physical access controller |
| Linux 4.14 | Intel® Atom® E3930 @1.30GHz | No | Ricoh IM C3010 |
| Linux 4.14 | Intel® Atom® E3940 @1.60GHz | No | Ricoh IM C4510 |
| NET+OS v7.6 | Digi International NS9210 | No | Spectrum Infusion System |
| Yocto (kirkstone) 4.0 | NXP i.MX6UL | No | Novum IQ Infusion Platform |
| MQX 3.4 | NXP PowerQUICC II MPC8313e 32bit | No | FEI-Zyfer Time and Frequency System |
| CodeOS v1.4 | CodeCorp CT8200 (ARM FA626TE) | No | Series CR2700 Code Reader(s) |
| OpenRTOS v10.5 | STM32L4R5 | No | Teledyne Webb SOM Module |
| Endace Crypto Firmware 2.1 | Intel® Xeon® Silver 4316 CPU @2.30GHz | No | EndaceProbe 2144 |
| Endace Crypto Firmware 2.1 | Intel® Xeon® Silver 4316 CPU @2.30GHz | Yes | EndaceProbe 2144 |
| Endace Crypto Firmware 2.1 | Intel® Xeon® Gold 6338N CPU @2.20GHz | No | EndaceProbe 2184 |
| Endace Crypto Firmware 2.1 | Intel® Xeon® Gold 6338N CPU @2.20GHz | Yes | EndaceProbe 2184 |
| Endace Crypto Firmware 2.1 | Intel® Xeon® Gold 5418N CPU @1.80GHz | Yes | EndaceProbe 94C8 |
| Endace Crypto Firmware 2.1 | Intel® Xeon® Gold 6230N CPU @2.30GHz | Yes | EndaceProbe 92C8 |
| Anyware Trusted Zero Client Firmware Kernel 6.1 | AMD Ryzen Embedded R1305G | No | Anyware Trusted Zero Client |
| Anyware Trusted Zero Client Firmware Kernel 6.1 | AMD Ryzen Embedded R1305G | Yes | Anyware Trusted Zero Client |
| Anyware Trusted Zero Client Firmware Kernel 6.1 | AMD Ryzen Embedded R2314 | Yes | HP tz655 Trusted Zero Client |
| Fusion Embedded RTOS 5.0 | Analog Devices ADSP-BF516 (Blackfin) | No | Classone ® IP Radio Gateway |
| Linux 5.4 | NXP i.MX8M | No | Harman MUSE MU Controller |
| Linux 4.9 | ARM Cortex-A7 | No | Harman N2612S Video encoder/decoder |
| Linux 5.10 | NXP i.MX8 | No | Harman N4321D audio transcoder |
| REDACTED Linux 5.4 | Xilinx Zynq-7000 SoC | No | TBA |
| REDACTED Linux 5.4 | Xilinx Zynq-7000 SoC | Yes | TBA |
| REDACTED Linux 4.19 | Xilinx Zynq Ultrascale+ | No | TBA |
| REDACTED Linux 4.19 | Xilinx Zynq Ultrascale+ | Yes | TBA |
| REDACTED Linux 4.9 | Ambarella S5L SoC | No | TBA |
| REDACTED Linux 4.9 | Ambarella S5L SoC | Yes | TBA |
| REDACTED Linux 5.4 | i.MX8 Quad Max SoC | No | TBA |
| REDACTED Linux 5.4 | i.MX8 Quad Max SoC | Yes | TBA |
| FreeRTOS v10.4 | NXP i.MX RT1051 | No | Harman CE-REL8 Universal Control Extender |
| Linux 5.15 | MTK MT8395 | No | Harman N3322D Video encoder/decoder |
| Android 14 | Qualcomm SM8350 Snapdragon | No | Samsung Galaxy S21 |
| Android 14 | Qualcomm SM8350 Snapdragon | Yes | Samsung Galaxy S21 |
| Linux 6.6 | Xilinx Zynq Ultrascale+ | No | SEL Switch |
| Linux 6.6 | Altera SoC FPGA | No | SEL-2740 |
| Linux 5.15 | i.MX6UL | No | TBA |
| Debian 12.5 | Intel® Xeon® E3-1275v6 @3.80GHz | No | TBA |
| OS: Ubuntu Version 22.04 Hypervisor: VMWare ESXi Version 7.0.3 | Intel® Xeon® E5-2697 v3 | No | TBA |
| Nucleus 3.0 version 2013.08.1 | Freescale Vybrid VF500 | No | XL200P Radio |
| Yocto 4.0-r7 (kirkstone) | STM32MP157 | No | Claria Plus |
| Linux 6.6 | Freescale i.MX7 Dual Arm Cortex A-7 | No | TBA |
| Linux 6.6 | Freescale i.MX7 Dual Arm Cortex A-7 | Yes | TBA |
| HP Imaging & Printing Linux 4.9 Kernel | ARM Cortex-A72 | No | HP PN 3PZ95-60002 |
| HP Imaging & Printing Linux 4.9 Kernel | ARM Cortex-A72 | Yes | HP PN 3PZ95-60002 |
| HP Imaging & Printing Linux 4.9 Kernel | ARM Cortex-A53 | No | HP PN 6QN27-60001A |
| HP Imaging & Printing Linux 4.9 Kernel | ARM Cortex-A53 | Yes | HP PN 6QN27-60001A |
| Microsoft Windows CE 6.0 | ARM Cortex-A8 | No | HP Color LaserJet Enterprise M553 |
| OS: RHEL 8.10 Hypervisor: qemu-kvm 6.2 on RHEL 8.10 | Intel® Xeon® Gold 6526Y @2.80GHz | No | Dell R660 |
| OS: RHEL 8.10 Hypervisor: qemu-kvm 6.2 on RHEL 8.10 | Intel® Xeon® Gold 6526Y @2.80GHz | Yes | Dell R660 |
| Windows 11 Pro | Intel® Core™ i7-1255U @ 1.70 Ghz | No | Dell Precision 3570 |
| Windows 11 Pro | Intel® Core™ i7-1255U @ 1.70 Ghz | Yes | Dell Precision 3570 |
| Android 13 | Qualcomm Snapdragon 8 Gen 2 (SoC) | No | Samsung Galaxy S23 |
| Android 13 | Qualcomm Snapdragon 8 Gen 2 (SoC) | Yes | Samsung Galaxy S23 |
| iOS 17.3 | Apple A15 Bionic | No | iPhone 14 |
| iOS 17.3 | Apple A15 Bionic | Yes | iPhone 14 |
| Linux 5.4 | Dual ARM Cortex A7 | No | Lenovo XClarity Controller |
| Linux 5.4 | Dual ARM Cortex A7 | Yes | Lenovo XClarity Controller |
| Linux 6.6 | Dual ARM Cortex A7 | No | Lenovo XClarity Controller |
| Linux 6.6 | Dual ARM Cortex A7 | Yes | Lenovo XClarity Controller |
| Android 11 | MTK MT6762 | No | TBA |
| Linux 4.14 | MIPS 24Kc V7.4 | No | TBA |
| Ubuntu 20.04.6 | NXP i.MX8M | No | TBA |
| UEFI Specification Version 2.3.1 (32-bit) | Intel® Atom™ Processor Z3745D | No | Dell Venue 8 Pro |
| UEFI Specification Version 2.6.0 (64-bit) | Intel Core i5-7300U | No | Dell Latitude 7480 |
| UEFI Specification Version 2.6.0 (64-bit) | Intel Core i5-7300U | Yes | Dell Latitude 7480 |
| Linux 5.15 Yocto (Kirkstone) | NXP i.MX8M Mini Quad Cortex®-A53 | No | TBA |
| QNX 6.6 | NXP i.MX6 | No | TBA |
| Windows Server 2022 | Intel® Xeon® Gold 6414U CPU | No | PowerEdge R660 Rack Server |
| Cesium 2.93 | STM32H753 | No | TBA |
| HP Imaging & Printing Linux 5.10 | ARM Cortex-A72 without PAA | No | HP Color LaserJet Enterprise 6700 |
| HP Imaging & Printing Linux 5.10 | ARM Cortex-A72 with PAA | Yes | HP Color LaserJet Enterprise 6700 |
| HP Imaging & Printing Linux 5.10 | ARM Cortex-A53 without PAA | No | HP Color LaserJet Enterprise 5700 |
| HP Imaging & Printing Linux 5.10 | ARM Cortex-A53 with PAA | Yes | HP Color LaserJet Enterprise 5700 |
| Linux 6.6 | NXP LS1012 | No | TBA |
| Debian GNU/Linux 8 (jessie) | Broadcom BCM56771 | No | TBA |
| Linux IPHO00559B23 3.4 | Broadcom BCM6838 | No | TBA |
| Linux IPHO00550F22 4.1 | Broadcom BCM6858 | No | TBA |
| Debian GNU/Linux 8 (jessie) | Broadcom BCM5634 | No | TBA |
| Digi Embedded Yocto 5.0 | NXP i.mx6UL | No | TBA |
Certificate #3389 Current OE List:
| Operating System | Processor | Platform |
|---|---|---|
| OpenRTOS v10.1.1 | STM32L4Rx | STMicroelectronics STM32L4R9I-DISCO (Discovery Kit) |
| HP Imaging & Printing Linux 4.9 | ARMv8 Cortex-A72/A53 | HP PN 3PZ95-60002 |
| Windows 10 Enterprise | Intel® Core™ i7-7820 x4 | Radar FCL Package Utility |
| Linux socfpga cyclone V | Armv7 rev 0, Cortex A-9 | SEL 2700 Series 24-Port Ethernet Switch |
| Fusion Embedded RTOS 5.0 | Analog Devices ADSP-BF516 (Blackfin) | Classone ® IP Radio Gateway |
| Linux 4.12 Yocto Standard | Freescale i.MX6 DualLite ARMv7 Cortex-A9 x2 | Metasys® SNC Series Network Control Engine |
| Nucleus 3.0 version 2013.08.1 | Freescale Vybrid VF500 | XL200 Radio |
| CodeOS v1.4 | CT8200 (ARM FA626TE) | HP ProLiant DL360 |
| Linux 4.14 | Armv8 Cortex-A53 | SEL-2742S |
| CMSIS-RTOS v2.1.3 | Silicon Labs EFM32G | Alto™ |
| Windows CE 6.0 | ARM Cortex-A8 | HP LaserJet Enterprise |
| QNX 6.6 | NXP i.MX 6SoloX Arm® Cortex®-A9 | Zebra ZT610 |
| QNX 7.0 | NXP i.MX7 Arm® Cortex®-A7 (x2) | Zebra ZD621 |
| QNX 6.5 | NXP i.MX25 Arm9™ | Zebra ZQ630 |
| QNX 7.0 | NXP i.MX 6ULL Arm® Cortex®-A7 | Zebra ZT421 |
| SUSE Linux Enterprise hosted in Hypervisor Vmware ESXi 6.7.0 | Intel® Xeon® E-2234 | Dell PowerEdge T340 |
| Linux 4.14 | Dual ARM Cortex A9 | Lenovo XClarity Controller |
| Swoop Kernel 1.5 | Xilinx Zynq Ultrascale+ XCZU9EG™ | Skipper |
| Windows Server 2016 | Intel® Xeon® E5-2603 | Dell PowerEdge R430 |
| NET+OS v7.6 | NS9210 | Sigma IV Infusion Pump |
| Windows 10 Pro | Intel® Core™ i7-7600U | Lenovo Thinkpad T470 |
| Windows Server 2019 | Intel® Xeon® Silver 4116 (x24) | HPE ProLiant DL360 |
| Android 11 | Qualcomm Snapdragon 865 (SoC) | Samsung Galaxy S20 5G |
| Linux 5.4 | Freescale i.MX7 Dual ARM® Cortex-A7 | iSTAR physical access controller |
| Linux 5.4 | Intel® Xeon® E-2244G | Dell PowerEdge R340 Rack Server |
| Linux 4.12 | Intel® Core™ i3-7101 | HP PageWide XL |
| Linux 4.9 | Freescale i.MX7 Dual ARM® Cortex-A7 | ZOLL Communications Module |
| NetBSD v6.0.1 | Intel(R) Atom(R) E3930 | RICOH IM C2500 |
| NetBSD v6.0.1 | Intel(R) Atom(R) E3940 | RICOH IM C6000 |
| Android 6.0 (Linux 4.1) | Freescale i.MX6 Quad/DualLite | RICOH IM C6000 |
| iOS 14 | Apple A14 Bionic | iPhone 12 |
| Android 8.1 (Linux 4.4) | Qualcomm Snapdragon 835 (APQ8098 / MSM8998) | EchoNous Kosmos® Bridge |
| CentOS Linux 7.9 on VMware ESXi 6.7 | Intel® Xeon® X5650 @2.67GHz | HP ProLiant DL360 |
| Linux 3.10 (CentOS 7) | Intel® Atom™ CPU D525 @1.80GHz | Beckman Coulter PROService RAP BOX |
| Yocto (dunfell) 3.1 | AMD GX-412TC SoC | LinkGuard |
| Linux 5.4 | Intel® Xeon® Gold 5218 CPU @ 2.30GHz | LiveAction LiveNX Appliance |
| Windows 10 Pro | Intel® Core™ i7-1255U @1.70 GHz | Dell Precision 3570 |
| FreeBSD 10.3 on VMWare ESXi 7.0 | Intel® Xeon® Silver 4210 @2.20GHz | Supermicro X11DPH-i (vnc-wolf) |
| Linux 5.15 on VMWare ESXi 7.0 | Intel® Xeon® Silver 4210 @2.20GHz | Supermicro X11DPH-i (sdlc-wolf) |
| Debian GNU/Linux 8 (jessie) | Broadcom BCM5634 | Corning 1LAN-SDDP-24POE (onl-armel) |
| Linux IPHO00550F22 4.1 | Broadcom BCM6858 | Corning 1LAN-SDAN-7691 (bcm6858x) |
| Debian GNU/Linux 8 (jessie) | Intel® Atom™ C2558 @ 2.40GHz | ufiSpace Cloud and Data Center Switch S7810-54QS (onl-x86_64) |
| Linux IPHO00559B23 3.4 | Broadcom BCM6838 | Corning 1LAN-SDAN-7290 (bcm683xx) |
| VxWorks 7 SR0630 | Intel® Core™ i7-5850EQ @2.70GHz | F-16 WASP |
| macOS Monterey 12.5 | Intel® Core™ i7-8569U @2.80GHz | MacBook Pro |
| macOS Monterey 12.5 | Apple M1 Max | MacBook Pro |
| Windows 11 Enterprise | Intel® Core™ i7-10610U @1.80GHz | Dell Latitude 7410 |
| Endace Crypto Firmware 1.0 | Intel® Xeon® Silver 4316 CPU @2.30GHz | EndaceProbe 2144 |
| macOS Monterey 12.5 | Apple M1 | MacBook Air |
| Vortec Scheduler | StarCore SC3850 DSP | Avaya MP160 |
| VxWorks 7 | NXP T1024 | G450 Media Gateway |
| VxWorks 6.9 | NXP MPC8650 | G430 Media Gateway |
| VxWorks 6.9 | TNETV1050 | Sectéra vIPer™ Phone |
| VxWorks 5.5 | Marvell Poncat2 Sheeva™ | ML6416E |
| Janteq Zynq Linux 5.4 | Xilinx Zynq-7000 SoC | AviTr3 |
| Janteq Zynq Linux 4.19 | Xilinx Zynq Ultrascale+ | Bronte3 |
| Janteq S5L Linux 4.9 | Ambarella S5L SoC | Maximo |
| Endace Crypto Firmware 1.0 | Intel® Xeon® Gold 6338N CPU @2.20GHz | EndaceProbe 2184 |
| Endace Crypto Firmware 1.0 | Intel® Xeon® Gold 5418N CPU @1.80GHz | EndaceProbe 94C8 |
| Endace Crypto Firmware 1.0 | Intel® Xeon® Gold 6230N CPU @2.30GHz | EndaceProbe 92C8 |
| Janteq iMX8QM Linux version 5.4 | i.MX8 Quad Max SoC | Flip2 |
| Android 13 | QualComm SnapDragon 8 SoC | Samsung Galaxy S22 |
Certificate #2425 Current OE List:
| Operating System | Processor | Platform |
|---|---|---|
| Linux 3.13 (Ubuntu) | Intel® Core™ i7-3720QM CPU @2.60GHz x 8 | HP EliteBook |
| iOS 8.1 | Apple™ A8 | iPhone™ 6 |
| Android 4.4 | Qualcomm Krait 400 | Samsung Galaxy S5 |
| FreeRTOS 7.6 | ST Micro STM32F | uTrust TS Reader |
| Windows 7 (64-bit) | Intel® Core™ i5 | Sony Vaio Pro |
| Linux 3.0 (SLES 11 SP4, 64-bit) | Intel® Xeon® E3-1225 | Imprivata OneSign |
| Linux 3.0 (SLES 11 SP4, 64-bit) on Microsoft Hyper-V 2012R2 Core | Intel® Xeon® E5-2640 | Dell® PowerEdge™ r630 |
| Linux 3.0 (SLES 11 SP4, 64-bit) on VMWare ESXi 5.5.0 | Intel® Xeon® E5-2640 | Dell® PowerEdge™ r630 |
| Windows 7 (64-bit) on VMWare ESXi 5.5.0 | Intel® Xeon® E5-2640 | Dell® PowerEdge™ r630 |
| Android Dalvik 4.2.2 | NXP i.MX6 | MXT‐700‐NC 7” touch panel |
| Linux 4.1.15 | NXP i.MX5 | NX‐1200 NetLinx NX Integrated Controller |
| Debian 8.8 | Intel Xeon® 1275v3 | CA PAM 304L Server |
| Windows Server 2012R2 | Intel® Xeon® E5335 | CA Technologies PAMHAF995 |
| Windows 7 Professional SP1 | Intel® Core™ i7‐2640M | Dell™ Latitude™ E6520 |
| Debian 8.7.0 | Intel ® Xeon® E3 Family with SGX support | Intel® x64 Server System R1304SP |
| Windows 10 Pro | Intel ® Core ™ i5 with SGX support | Dell™ Latitude™ 7480 |
| NET+OS v7.6 | Digi International NS9210 | Sigma IV infusion pump |
| Linux 4.4 (SLES 12 SP3, 64‐ bit) on Microsoft Hyper‐V 2016 Core | Intel® Xeon® E5‐2650 | Dell® PowerEdge™ r720 |
| Linux 4.4 (SLES 12 SP3, 64‐ bit) on VMWare ESXi 6.5.0 | Intel® Xeon® E5‐2403 | Dell® PowerEdge™ r420 |

