wolfBoot is our secure bootloader designed to provide safety-oriented secure boot for any embedded device. Its success lies in its ability to offer security, efficiency and adaptability to many different use cases, while keeping a simple and safe design. wolfBoot is a solid choice made by many developers securing the boot mechanism on a wide range of embedded devices from every industry.
A new version of wolfBoot (v2.1.0) has been released, which introduces new features, support for more cryptography, ports to new embedded targets and improvements to existing code.
Download wofBoot 2.1.0 from our download page or clone it from github.
Support for custom fields in the manifest header
One of the most requested features by our users consisted in allowing extra parameters in the manifest header of the firmware/software images to be verified.
wolfBoot manifest header consists in a sequence of “TLV” (table-length-value) fields. By default, a signed image’s manifest header contains a SHA digest, the public-key signature itself, and a few extra fields containing metadata relative to the image and the sign process. These fields include a 32-bit version number (used to prevent rollback attacks), a 64-bit timestamp, a digest of the public key needed to verify the signature, a ‘type’ field, used by the bootloader to identify and confirm the algorithms used and the destination partition for the update.
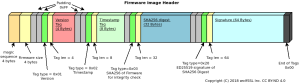
All these fields in the manifest headers, except for the digest and the signature itself, are included in the calculation of the signed digest, which means that their values cannot be altered without compromising the validity of the signature.
The new feature introduced in wolfBoot 2.1.0 consists in three new mechanism that can be used to add new TLVs to the header:
- –custom-tlv tag len val
Adds a TLV entry to the manifest header, corresponding to the type identified by “tag”, with length “len“ bytes, and assigns the value “val”.Values can be decimal or hex numbers (prefixed by ‘0x’). This is useful to add numeric values (e.g. with length 1, 2, 4, or 8). - –custom-tlv-buffer tag len buffer
Adds a TLV entry with a buffer in hex format,
e.g. –custom-tlv-buffer 0x31 6 CCBBAA998877 - –custom-tlv tag string
Adds a TLV containing a string of bytes read as ASCII characters from the “string” argument. In this case the length is implicit as the argument is null-terminated.
As usual, these fields can be accessed from wolfBoot custom modules, using the wolfBoot_find_header() parser. This function is included in libwolfboot, which means that the same parser can be invoked on any stored signed image by applications integrating the library.
New signature verification algorithm
ECC521 support has been added, further expanding the range of cryptographic algorithms available for signature verification, bolstering security for a broader spectrum of applications (and did you know that since v2.0 wolfBoot also supports post-quantum signature verification algorithms too?).
Support for new embedded platforms
We facilitate the process to integrate new ports of wolfBoot, which includes the integration of an example application to demonstrate secure boot and update out-of-the-box, with a single build command. This version introduces support for new embedded targets:
- Renesas RZ2NL
- Microchip SAM E51
- NXP MCXA-153
- NXP i.MX-RT1040
Improvements and enhancements
Version 2.1.0 addresses various bugs and introduces enhancements for existing platforms and target-specific mechanisms.
For targets supporting the DUALBANK option, i.e. the ability to swap the mapping of two “banks” inside the same flash memory support, we added some additional checks to ensure that wolfBoot copies (or “forks”) itself to the second bank only once in the lifetime of the bootloader.
For those use-cases with backup disabled, we have simplified the update mechanism, which also improved the reliability of the update across power-failures.
We have fixed an issue in the wolfTPM integration code, which was preventing the policy from being properly sealed. This issue is only affecting those configurations including the `WOLFBOOT_TPM_SEAL` option introduced in version 2.0.0.
Contacts Us
Let us know what features you value the most, what platforms you would like to see our code running on, or just tell us your story about secure-boot in your embedded systems.
If you have questions about any of the above, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now

