BENCHMARKING WOLFSSL AND WOLFCRYPT
Reference benchmarks
- wolfJSSE vs. SunJSSE
- SiFive
- HiFive Unleashed
- Xilinx ZCU102 Petalinux
- Renesas RX65N with TSIP (Trusted Secure IP)
- Renesas AP-RX71M-0A
- Renesas Synergy DK-S7G2
- Espressif ESP32 WROOM
- Intel x86_64
- NXP i.MX6
- Apple iPhone X
- Microchip PIC32MZ
- STM32 (STM32F439, STM32F756)
- STM32F777NI
- Apple iPhone 8/8 Plus/X (Apple A11 Bionic)
- Intel SGX
- Intel QuickAssist
- ARMv8
- AVX1, AVX2
- Atmel SAMD21
- STM32F221G-EVAL
- Texas Instruments – Tiva C Series TM4C1294XL – Connected Launchpad
- Freescale TWR-K70F120M
- Apple TV 2
- mbed
- Relative Cipher Performance
- Post-Quantum Kyber Benchmarks (Linux)
- Post-Quantum Kyber Benchmarks (ARM Cortex-M4)
- Post-Quantum Kyber Benchmarks (MacOS)
- Raspberry Pi Pico-W
The wolfSSL embedded SSL/TLS library was written from the ground-up with portability, performance, and memory usage in mind. Here you will find a collection of existing benchmark information for wolfSSL and the wolfCrypt cryptography library as well as information on how to benchmark wolfSSL on your own platform. If you would like additional benchmark data or have any questions about your specific platform, please contact us at facts@wolfssl.com.
wolfCrypt Benchmark Application
Many users are curious about how the wolfSSL embedded SSL/TLS library will perform on a specific hardware device or in a specific environment. Because of the wide variety of different platforms and compilers used today in embedded, enterprise, and cloud-based environments, it is hard to give generic performance calculations.
To help wolfSSL users and customers in determining performance for wolfSSL and wolfCrypt, a benchmark application is bundled with wolfSSL. Because the underlying cryptography is a very performance-critical aspect of SSL/TLS, our benchmark application runs performance tests on wolfCrypt’s algorithms.
Running the benchmark
The benchmark utility is located in the “./wolfcrypt/benchmark” directory of the wolfSSL package. After building wolfSSL and the associated examples and apps, the benchmark application can be run by issuing the following command from the package directory root:
./wolfcrypt/benchmark/benchmark
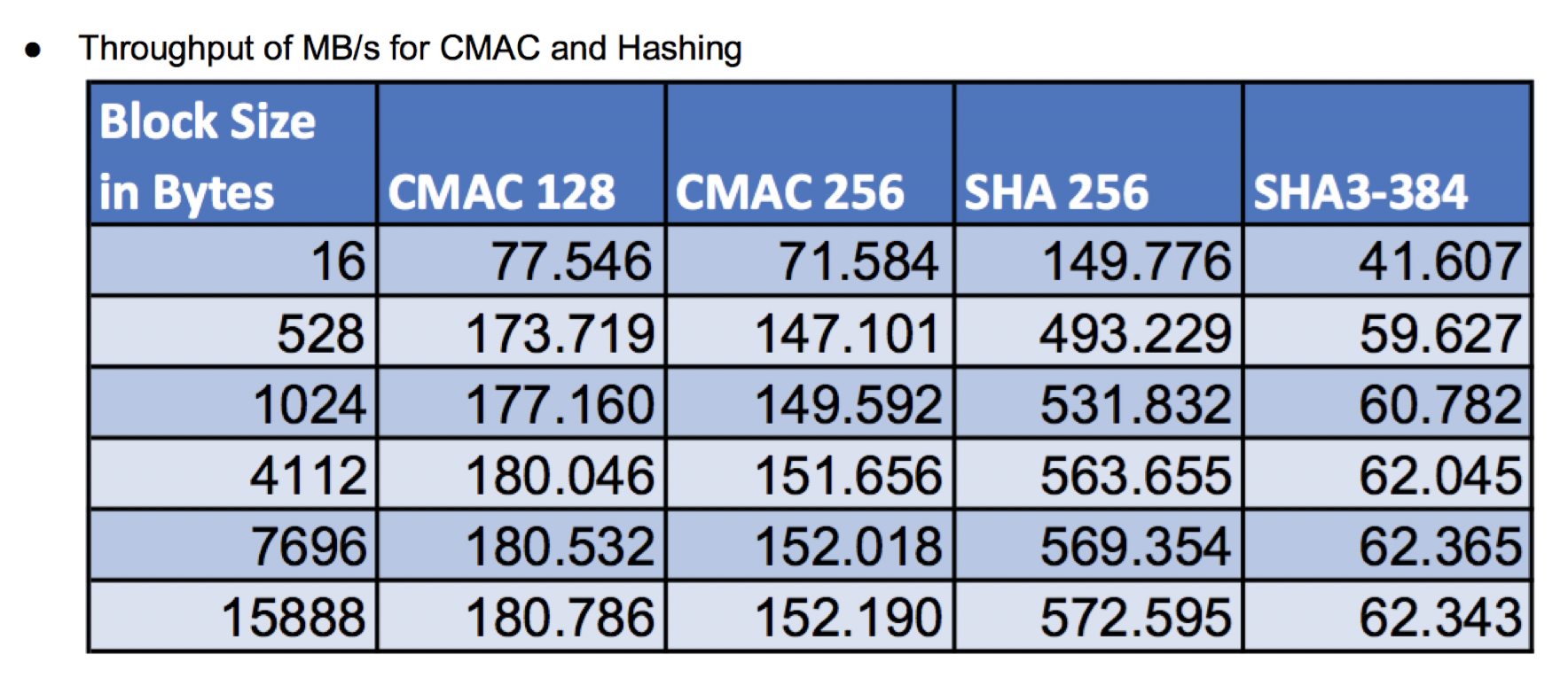
Typical output will look similar to the output below (showing throughput in MB/s as well as cycles per byte):
wolfCrypt Benchmark (block bytes 1048576, min 1.0 sec each) RNG 100 MB took 1.047 seconds, 95.466 MB/s Cycles per byte = 22.92 AES-128-CBC-enc 200 MB took 1.020 seconds, 196.027 MB/s Cycles per byte = 11.16 AES-128-CBC-dec 215 MB took 1.008 seconds, 213.318 MB/s Cycles per byte = 10.26 AES-192-CBC-enc 175 MB took 1.016 seconds, 172.265 MB/s Cycles per byte = 12.70 AES-192-CBC-dec 180 MB took 1.009 seconds, 178.405 MB/s Cycles per byte = 12.27 AES-256-CBC-enc 150 MB took 1.007 seconds, 148.932 MB/s Cycles per byte = 14.69 AES-256-CBC-dec 160 MB took 1.026 seconds, 155.994 MB/s Cycles per byte = 14.03 AES-128-GCM-enc 60 MB took 1.010 seconds, 59.427 MB/s Cycles per byte = 36.82 AES-128-GCM-dec 65 MB took 1.070 seconds, 60.750 MB/s Cycles per byte = 36.02 AES-192-GCM-enc 60 MB took 1.050 seconds, 57.138 MB/s Cycles per byte = 38.30 AES-192-GCM-dec 60 MB took 1.024 seconds, 58.590 MB/s Cycles per byte = 37.35 AES-256-GCM-enc 55 MB took 1.029 seconds, 53.438 MB/s Cycles per byte = 40.95 AES-256-GCM-dec 60 MB took 1.090 seconds, 55.069 MB/s Cycles per byte = 39.74 CHACHA 360 MB took 1.001 seconds, 359.628 MB/s Cycles per byte = 6.09 CHA-POLY 285 MB took 1.014 seconds, 280.943 MB/s Cycles per byte = 7.79 MD5 450 MB took 1.010 seconds, 445.573 MB/s Cycles per byte = 4.91 POLY1305 1265 MB took 1.000 seconds, 1264.402 MB/s Cycles per byte = 1.73 SHA 475 MB took 1.000 seconds, 474.914 MB/s Cycles per byte = 4.61 SHA-224 210 MB took 1.018 seconds, 206.308 MB/s Cycles per byte = 10.61 SHA-256 210 MB took 1.018 seconds, 206.200 MB/s Cycles per byte = 10.61 SHA-384 280 MB took 1.016 seconds, 275.520 MB/s Cycles per byte = 7.94 SHA-512 275 MB took 1.000 seconds, 274.868 MB/s Cycles per byte = 7.96 SHA3-224 240 MB took 1.006 seconds, 238.506 MB/s Cycles per byte = 9.18 SHA3-256 225 MB took 1.007 seconds, 223.454 MB/s Cycles per byte = 9.79 SHA3-384 175 MB took 1.002 seconds, 174.610 MB/s Cycles per byte = 12.53 SHA3-512 125 MB took 1.031 seconds, 121.254 MB/s Cycles per byte = 18.05 HMAC-MD5 445 MB took 1.001 seconds, 444.651 MB/s Cycles per byte = 4.92 HMAC-SHA 470 MB took 1.009 seconds, 465.749 MB/s Cycles per byte = 4.70 HMAC-SHA224 200 MB took 1.001 seconds, 199.874 MB/s Cycles per byte = 10.95 HMAC-SHA256 205 MB took 1.004 seconds, 204.228 MB/s Cycles per byte = 10.72 HMAC-SHA384 290 MB took 1.009 seconds, 287.401 MB/s Cycles per byte = 7.61 HMAC-SHA512 290 MB took 1.013 seconds, 286.214 MB/s Cycles per byte = 7.65 RSA 2048 public 2800 ops took 1.014 sec, avg 0.362 ms, 2761.995 ops/sec RSA 2048 private 300 ops took 1.308 sec, avg 4.359 ms, 229.402 ops/sec DH 2048 key gen 735 ops took 1.001 sec, avg 1.361 ms, 734.608 ops/sec DH 2048 key agree 800 ops took 1.123 sec, avg 1.404 ms, 712.131 ops/sec ECC 256 key gen 1108 ops took 1.001 sec, avg 0.903 ms, 1107.306 ops/sec ECDHE 256 agree 1200 ops took 1.043 sec, avg 0.869 ms, 1150.329 ops/sec ECDSA 256 sign 1200 ops took 1.078 sec, avg 0.898 ms, 1113.279 ops/sec ECDSA 256 verify 1700 ops took 1.045 sec, avg 0.615 ms, 1627.064 ops/sec
This application is especially useful for comparing the public key speed before and after changing the math library. You can test the results using the normal math library (./configure), the fastmath library (./configure –enable-fastmath), the fasthugemath library (./configure –enable-fasthugemath), and the sp-math-all library (./configure –enable-sp-math-all).
Note: By default the reported units scale based on the value of each benchmark. To force consistent, fixed units for all reported values build the application defining WOLFSSL_BENCHMARK_FIXED_UNITS_XX, where XX is GB, MB, KB, or B (ytes). For example, ./configure CFLAGS=”-DWOLFSSL_BENCHMARK_FIXED_UNITS_MB” displays all values in MB.
Memory Usage
Footprint sizes (compiled binary size) for wolfSSL range between 20-100kB depending on build options and the compiler being used. Typically on an embedded system with an embedded and optimized compiler, build sizes will be around 60kB. This will include a full-featured TLS 1.2 client and server. For details on build options and ways to further customize wolfSSL, please see Chapter 2 of the CyaSSL Manual, or the wolfSSL Tuning Guide.
Regarding runtime memory usage, wolfSSL will generally consume between 1-36 kB per SSL/TLS session. The RAM usage per connection will vary depending the size of the input/output buffers being used, public key algorithm, and key size. The I/O buffers in wolfSSL default to 128 bytes and are controlled by the RECORD_SIZE define in ./wolfssl/internal.h. The maximum size is 16 kB per buffer (as specified by the SSL/TLS RFC). As an example, with standard 16kB buffers, the total runtime memory usage of wolfSSL with a single connection would be 3kB (the library) + 16kB (input buffer) + 16kB (output buffer) = around 35kB.
The TLS context (WOLFSSL_CTX) is shared between all TLS connections of either a client or server. The runtime memory usage can vary depending on how many certificates are being loaded and what size the certificate files are. It will also vary depending on the session cache and whether or not storing session certificates is turned on (–enable-session-certs). If you are concerned with reducing the session cache size, you can define SMALL_SESSION_CACHE (reduce the default session cache from 33 session to 6 sessions) and save almost 2.5 kB. You can disable the session cache by defining NO_SESSION_CACHE, reducing memory by nearly 3 kB.
Reference Benchmarks
As we port wolfSSL to various platforms, we oftentimes conduct benchmarks on these platforms. Below you will find a collection of some of those benchmarks for reference. If you have benchmarked wolfSSL on a specific platform, please send us your benchmark numbers (with specific platform and library configuration) and we’ll add them to the list!
Platform:
wolfSSL JSSE Provider(vs. default SunJSSE) on Mac OSX
Benchmark:
The following benchmarks show the performance improvement when using the wolfSSL Java JSSE Provider versus the default SunJSSE provider.
| Client and Configuration | Avg. Connection Time |
|---|---|
| wolfSSL C only (no Java, software) | 9.694 ms |
| wolfSSL C only (no Java, intelasm + sp + sp-asm) | 7.302 ms |
| wolfJSSE Client (software only) | 10.92 ms |
| wolfJSSE Client (sp + intelasm) | 8.42 ms |
| wolfJSSE Client (TLS 1.3 sp + intelasm) | 8.04 ms |
| SunJSSE Provider client (default on Mac) | 13.34 ms |
More information on using the wolfSSL JSSE Provider can be found in the User Manual.
Return to top of page
Platform:
SiFive:SiFive HiFive1 Rev B
Benchmark:
The benchmark values were collected with a clock speed of 320MHz. Configuration includes 4608 bytes for the stack and 2048 bytes for the heap.
wolfCrypt Benchmark (block bytes 1024, min 1.0 sec each) RNG 250 KB took 1.098 seconds, 227.714 KB/s AES-128-CBC-enc 50 KB took 1.132 seconds, 44.175 KB/s AES-128-CBC-dec 50 KB took 1.142 seconds, 43.778 KB/s AES-192-CBC-enc 50 KB took 1.250 seconds, 40.007 KB/s AES-192-CBC-dec 50 KB took 1.260 seconds, 39.677 KB/s AES-256-CBC-enc 50 KB took 1.368 seconds, 36.552 KB/s AES-256-CBC-dec 50 KB took 1.378 seconds, 36.279 KB/s AES-128-GCM-enc 25 KB took 1.225 seconds, 20.412 KB/s AES-128-GCM-dec 25 KB took 1.225 seconds, 20.402 KB/s AES-192-GCM-enc 25 KB took 1.290 seconds, 19.373 KB/s AES-192-GCM-dec 25 KB took 1.291 seconds, 19.366 KB/s AES-256-GCM-enc 25 KB took 1.352 seconds, 18.487 KB/s AES-256-GCM-dec 25 KB took 1.353 seconds, 18.478 KB/s CHACHA 1 MB took 1.006 seconds, 1.020 MB/s CHA-POLY 700 KB took 1.032 seconds, 678.045 KB/s POLY1305 2 MB took 1.007 seconds, 2.255 MB/s SHA 2 MB took 1.002 seconds, 1.511 MB/s SHA-256 525 KB took 1.011 seconds, 519.279 KB/s SHA-512 275 KB took 1.017 seconds, 270.477 KB/s HMAC-SHA 1 MB took 1.013 seconds, 1.399 MB/s HMAC-SHA256 525 KB took 1.019 seconds, 515.020 KB/s HMAC-SHA512 275 KB took 1.032 seconds, 266.351 KB/s ECC 256 key gen 2 ops took 1.104 sec, avg 551.834 ms, 1.812 ops/sec ECDHE 256 agree 2 ops took 1.101 sec, avg 550.400 ms, 1.817 ops/sec ECDSA 256 sign 2 ops took 1.173 sec, avg 586.502 ms, 1.705 ops/sec ECDSA 256 verify 2 ops took 2.153 sec, avg 1076.294 ms, 0.929 ops/sec CURVE 25519 key gen 2 ops took 1.629 sec, avg 814.423 ms, 1.228 ops/sec CURVE 25519 agree 2 ops took 1.626 sec, avg 813.156 ms, 1.230 ops/sec ED 25519 key gen 1 ops took 1.436 sec, avg 1436.096 ms, 0.696 ops/sec ED 25519 sign 2 ops took 2.913 sec, avg 1456.421 ms, 0.687 ops/sec ED 25519 verify 2 ops took 5.012 sec, avg 2506.012 ms, 0.399 ops/sec
Return to top of page
Platform:
HiFive Unleashed at 1.4GHz
Benchmark:
The new asm is like 50 times faster
./configure --enable-riscv-asm && make root@HiFiveU:~/wolfssl-riscv# ./wolfcrypt/benchmark/benchmark -aes-cbc -aes-gcm------------------------------------------------------------------------------ wolfSSL version 5.7.0 ------------------------------------------------------------------------------ Math: Multi-Precision: Wolf(SP) word-size=64 bits=3072 sp_int.c wolfCrypt Benchmark (block bytes 1048576, min 1.0 sec each) AES-128-CBC-enc 20 MiB took 1.076 seconds, 18.588 MiB/s AES-128-CBC-dec 20 MiB took 1.083 seconds, 18.473 MiB/s AES-192-CBC-enc 20 MiB took 1.245 seconds, 16.062 MiB/s AES-192-CBC-dec 20 MiB took 1.246 seconds, 16.047 MiB/s AES-256-CBC-enc 15 MiB took 1.057 seconds, 14.189 MiB/s AES-256-CBC-dec 15 MiB took 1.055 seconds, 14.212 MiB/s AES-128-GCM-enc 15 MiB took 1.300 seconds, 11.543 MiB/s AES-128-GCM-dec 15 MiB took 1.300 seconds, 11.535 MiB/s AES-192-GCM-enc 15 MiB took 1.425 seconds, 10.526 MiB/s AES-192-GCM-dec 15 MiB took 1.425 seconds, 10.523 MiB/s AES-256-GCM-enc 10 MiB took 1.032 seconds, 9.687 MiB/s AES-256-GCM-dec 10 MiB took 1.032 seconds, 9.691 MiB/s GMAC Table 4-bit 31 MiB took 1.025 seconds, 30.251 MiB/s Benchmark complete
On master
./configure —enable-all && make root@HiFiveU:~/wolfssl# ./wolfcrypt/benchmark/benchmark -aes-cbc -aes-gcm ------------------------------------------------------------------------------ wolfSSL version 5.7.0 ------------------------------------------------------------------------------ Math: Multi-Precision: Wolf(SP) word-size=64 bits=4096 sp_int.c wolfCrypt Benchmark (block bytes 1048576, min 1.0 sec each) AES-128-CBC-enc 5 MiB took 12.798 seconds, 0.391 MiB/s AES-128-CBC-dec 5 MiB took 12.672 seconds, 0.395 MiB/s AES-192-CBC-enc 5 MiB took 15.301 seconds, 0.327 MiB/s AES-192-CBC-dec 5 MiB took 15.181 seconds, 0.329 MiB/s AES-256-CBC-enc 5 MiB took 17.820 seconds, 0.281 MiB/s AES-256-CBC-dec 5 MiB took 17.669 seconds, 0.283 MiB/s AES-128-GCM-enc 5 MiB took 12.870 seconds, 0.388 MiB/s AES-128-GCM-dec 5 MiB took 12.870 seconds, 0.388 MiB/s AES-192-GCM-enc 5 MiB took 15.375 seconds, 0.325 MiB/s AES-192-GCM-dec 5 MiB took 15.376 seconds, 0.325 MiB/s AES-256-GCM-enc 5 MiB took 17.878 seconds, 0.280 MiB/s AES-256-GCM-dec 5 MiB took 17.896 seconds, 0.279 MiB/s AES-128-GCM-STREAM-enc 5 MiB took 12.878 seconds, 0.388 MiB/s AES-128-GCM-STREAM-dec 5 MiB took 12.878 seconds, 0.388 MiB/s AES-192-GCM-STREAM-enc 5 MiB took 15.379 seconds, 0.325 MiB/s AES-192-GCM-STREAM-dec 5 MiB took 15.385 seconds, 0.325 MiB/s AES-256-GCM-STREAM-enc 5 MiB took 17.881 seconds, 0.280 MiB/s AES-256-GCM-STREAM-dec 5 MiB took 17.888 seconds, 0.280 MiB/s GMAC Table 4-bit 30 MiB took 1.006 seconds, 29.831 MiB/s Benchmark complete
Platform:
Renesas:Renesas RX65N (R5F565NEHDFB)
Benchmark:
The following benchmarks show the performance improvement when using hardware cryptography on the Renesas RX65N through the Renesas TSIP driver.
With H/W accelerator(with TSIP) wolfCrypt Benchmark (block bytes 1024, min 1.0 sec each) RNG 2 MB took 1.001 seconds, 1.928 MB/s AES-128-CBC-enc 3 MB took 1.005 seconds, 2.818 MB/s AES-128-CBC-dec 3 MB took 1.002 seconds, 2.631 MB/s AES-256-CBC-enc 3 MB took 1.001 seconds, 2.779 MB/s AES-256-CBC-dec 3 MB took 1.002 seconds, 2.680 MB/s AES-128-GCM-enc 3 MB took 1.007 seconds, 2.740 MB/s AES-128-GCM-dec 3 MB took 1.005 seconds, 2.647 MB/s AES-256-GCM-enc 3 MB took 1.002 seconds, 2.679 MB/s AES-256-GCM-dec 3 MB took 1.005 seconds, 2.649 MB/s ARC4 3 MB took 1.001 seconds, 3.440 MB/s RABBIT 4 MB took 1.004 seconds, 3.987 MB/s 3DES 200 KB took 1.053 seconds, 189.988 KB/s MD5 6 MB took 1.004 seconds, 5.790 MB/s SHA 23 MB took 1.001 seconds, 23.104 MB/s SHA-256 26 MB took 1.000 seconds, 25.974 MB/s SHA-512 275 KB took 1.063 seconds, 258.702 KB/s HMAC-MD5 6 MB took 1.003 seconds, 5.722 MB/s HMAC-SHA 22 MB took 1.001 seconds, 22.321 MB/s HMAC-SHA256 25 MB took 1.000 seconds, 24.995 MB/s HMAC-SHA512 275 KB took 1.079 seconds, 254.795 KB/s PBKDF2 672 bytes took 1.005 seconds, 668.790 bytes/s RSA 2048 public 12 ops took 1.015 sec, avg 84.608 ms, 11.819 ops/sec RSA 2048 private 2 ops took 2.388 sec, avg 1194.200 ms, 0.837 ops/sec DH 2048 key gen 4 ops took 1.268 sec, avg 316.900 ms, 3.156 ops/sec DH 2048 agree 4 ops took 1.652 sec, avg 412.950 ms, 2.422 ops/sec ECC 256 key gen 3 ops took 1.061 sec, avg 353.667 ms, 2.828 ops/sec ECDHE 256 agree 4 ops took 1.407 sec, avg 351.725 ms, 2.843 ops/sec ECDSA 256 sign 4 ops took 1.476 sec, avg 369.050 ms, 2.710 ops/sec ECDSA 256 verify 2 ops took 1.451 sec, avg 725.450 ms, 1.378 ops/sec CURVE 25519 key gen 3 ops took 1.412 sec, avg 470.500 ms, 2.125 ops/sec CURVE 25519 agree 4 ops took 1.882 sec, avg 470.475 ms, 2.126 ops/sec ED 25519 key gen 92 ops took 1.001 sec, avg 10.878 ms, 91.926 ops/sec ED 25519 sign 64 ops took 1.007 sec, avg 15.733 ms, 63.561 ops/sec ED 25519 verify 30 ops took 1.027 sec, avg 34.220 ms, 29.223 ops/sec
S/W only(without TSIP) wolfCrypt Benchmark (block bytes 1024, min 1.0 sec each) RNG 325 KB took 1.003 seconds, 323.899 KB/s AES-128-CBC-enc 675 KB took 1.003 seconds, 672.780 KB/s AES-128-CBC-dec 650 KB took 1.011 seconds, 643.182 KB/s AES-192-CBC-enc 625 KB took 1.022 seconds, 611.426 KB/s AES-192-CBC-dec 600 KB took 1.027 seconds, 584.511 KB/s AES-256-CBC-enc 575 KB took 1.026 seconds, 560.320 KB/s AES-256-CBC-dec 550 KB took 1.027 seconds, 535.749 KB/s AES-128-GCM-enc 275 KB took 1.053 seconds, 261.258 KB/s AES-128-GCM-dec 275 KB took 1.053 seconds, 261.258 KB/s AES-192-GCM-enc 275 KB took 1.094 seconds, 251.348 KB/s AES-192-GCM-dec 275 KB took 1.094 seconds, 251.279 KB/s AES-256-GCM-enc 250 KB took 1.035 seconds, 241.569 KB/s AES-256-GCM-dec 250 KB took 1.033 seconds, 242.084 KB/s ARC4 3 MB took 1.001 seconds, 3.439 MB/s RABBIT 4 MB took 1.000 seconds, 3.906 MB/s 3DES 200 KB took 1.086 seconds, 184.179 KB/s MD5 6 MB took 1.000 seconds, 5.784 MB/s SHA 2 MB took 1.006 seconds, 1.893 MB/s SHA-256 750 KB took 1.023 seconds, 733.138 KB/s SHA-512 275 KB took 1.029 seconds, 267.198 KB/s HMAC-MD5 6 MB took 1.004 seconds, 5.715 MB/s HMAC-SHA 2 MB took 1.002 seconds, 1.877 MB/s HMAC-SHA256 750 KB took 1.032 seconds, 726.956 KB/s HMAC-SHA512 275 KB took 1.045 seconds, 263.133 KB/s PBKDF2 96 bytes took 1.054 seconds, 91.056 bytes/s RSA 2048 public 12 ops took 1.024 sec, avg 85.292 ms, 11.724 ops/sec RSA 2048 private 2 ops took 2.388 sec, avg 1193.750 ms, 0.838 ops/sec DH 2048 key gen 4 ops took 1.265 sec, avg 316.275 ms, 3.162 ops/sec DH 2048 agree 4 ops took 1.644 sec, avg 410.950 ms, 2.433 ops/sec ECC 256 key gen 3 ops took 1.064 sec, avg 354.667 ms, 2.820 ops/sec ECDHE 256 agree 4 ops took 1.435 sec, avg 358.725 ms, 2.788 ops/sec ECDSA 256 sign 4 ops took 1.498 sec, avg 374.425 ms, 2.671 ops/sec ECDSA 256 verify 2 ops took 1.437 sec, avg 718.300 ms, 1.392 ops/sec CURVE 25519 key gen 2 ops took 1.005 sec, avg 502.350 ms, 1.991 ops/sec CURVE 25519 agree 2 ops took 1.004 sec, avg 502.100 ms, 1.992 ops/sec ED 25519 key gen 91 ops took 1.008 sec, avg 11.076 ms, 90.287 ops/sec ED 25519 sign 66 ops took 1.026 sec, avg 15.538 ms, 64.359 ops/sec ED 25519 verify 30 ops took 1.023 sec, avg 34.090 ms, 29.334 ops/sec
| Algorithm | Software Crypto | TSIP Accelerated Crypto |
|---|---|---|
| RNG | 231.160 KB/s | 1.423 MB/s |
| SHA | 1.239 MB/s | 22.254 MB/s |
| SHA-256 | 515.565 KB/s | 25.217 MB/s |
| Cipher Suite | Software Crypto (sec) | TSIP Accelerated Crypto (sec) |
|---|---|---|
| TLS_RSA_WITH_AES_128_CBC_SHA | 0.381 | 0.028 |
| TLS_RSA_WITH_AES_128_CBC_SHA256 | 0.383 | 0.028 |
| TLS_RSA_WITH_AES_256_CBC_SHA | 0.382 | 0.030 |
| TLS_RSA_WITH_AES_256_CBC_SHA256 | 0.385 | 0.029 |
More information on using wolfSSL in combination with Renesas and wolfSSL’s support for Renesas can be found here: https://www.wolfssl.com/docs/renesas/
Return to top of page
Platform:
Renesas: Renesas RX72N (RTK5RX72N0C00000BJ)
Benchmark:
With H/W accelerator(with TSIP) wolfCrypt Benchmark (block bytes 1024, min 1.0 sec each) RNG 4 MB took 1.004 seconds, 3.818 MB/s AES-128-CBC-enc 5 MB took 1.001 seconds, 4.852 MB/s AES-128-CBC-dec 5 MB took 1.004 seconds, 4.692 MB/s AES-256-CBC-enc 5 MB took 1.000 seconds, 4.688 MB/s AES-256-CBC-dec 5 MB took 1.002 seconds, 4.534 MB/s AES-128-GCM-enc 4 MB took 1.005 seconds, 4.348 MB/s AES-128-GCM-dec 4 MB took 1.001 seconds, 4.292 MB/s AES-256-GCM-enc 4 MB took 1.004 seconds, 4.257 MB/s AES-256-GCM-dec 4 MB took 1.004 seconds, 4.206 MB/s ARC4 7 MB took 1.001 seconds, 7.120 MB/s RABBIT 9 MB took 1.000 seconds, 9.155 MB/s 3DES 525 KB took 1.035 seconds, 507.050 KB/s MD5 15 MB took 1.001 seconds, 14.998 MB/s SHA 30 MB took 1.001 seconds, 30.084 MB/s SHA-256 35 MB took 1.000 seconds, 34.588 MB/s SHA-512 750 KB took 1.001 seconds, 749.475 KB/s HMAC-MD5 15 MB took 1.000 seconds, 14.844 MB/s HMAC-SHA 29 MB took 1.000 seconds, 29.440 MB/s HMAC-SHA256 34 MB took 1.000 seconds, 33.709 MB/s HMAC-SHA512 750 KB took 1.016 seconds, 738.334 KB/s PBKDF2 1 KB took 1.025 seconds, 1.219 KB/s RSA 2048 public 26 ops took 1.020 sec, avg 39.212 ms, 25.503 ops/sec RSA 2048 private 2 ops took 1.101 sec, avg 550.250 ms, 1.817 ops/sec DH 2048 key gen 7 ops took 1.037 sec, avg 148.114 ms, 6.752 ops/sec DH 2048 agree 6 ops took 1.184 sec, avg 197.250 ms, 5.070 ops/sec ECC 256 key gen 7 ops took 1.069 sec, avg 152.743 ms, 6.547 ops/sec ECDHE 256 agree 8 ops took 1.231 sec, avg 153.825 ms, 6.501 ops/sec ECDSA 256 sign 8 ops took 1.271 sec, avg 158.825 ms, 6.296 ops/sec ECDSA 256 verify 4 ops took 1.242 sec, avg 310.475 ms, 3.221 ops/sec CURVE 25519 key gen 5 ops took 1.055 sec, avg 211.080 ms, 4.738 ops/sec CURVE 25519 agree 6 ops took 1.266 sec, avg 211.050 ms, 4.738 ops/sec ED 25519 key gen 208 ops took 1.004 sec, avg 4.828 ms, 207.109 ops/sec ED 25519 sign 154 ops took 1.001 sec, avg 6.502 ms, 153.800 ops/sec ED 25519 verify 66 ops took 1.016 sec, avg 15.400 ms, 64.935 ops/sec S/W only(without TSIP) wolfCrypt Benchmark (block bytes 1024, min 1.0 sec each) RNG 850 KB took 1.020 seconds, 833.578 KB/s AES-128-CBC-enc 2 MB took 1.006 seconds, 1.626 MB/s AES-128-CBC-dec 2 MB took 1.001 seconds, 1.537 MB/s AES-192-CBC-enc 2 MB took 1.013 seconds, 1.494 MB/s AES-192-CBC-dec 1 MB took 1.003 seconds, 1.412 MB/s AES-256-CBC-enc 1 MB took 1.007 seconds, 1.382 MB/s AES-256-CBC-dec 1 MB took 1.008 seconds, 1.308 MB/s AES-128-GCM-enc 750 KB took 1.001 seconds, 749.026 KB/s AES-128-GCM-dec 750 KB took 1.002 seconds, 748.503 KB/s AES-192-GCM-enc 725 KB took 1.007 seconds, 719.817 KB/s AES-192-GCM-dec 725 KB took 1.008 seconds, 719.317 KB/s AES-256-GCM-enc 700 KB took 1.010 seconds, 693.001 KB/s AES-256-GCM-dec 700 KB took 1.011 seconds, 692.589 KB/s ARC4 7 MB took 1.001 seconds, 7.120 MB/s RABBIT 9 MB took 1.000 seconds, 9.154 MB/s 3DES 525 KB took 1.034 seconds, 507.835 KB/s MD5 15 MB took 1.000 seconds, 14.990 MB/s SHA 6 MB took 1.003 seconds, 5.574 MB/s SHA-256 2 MB took 1.002 seconds, 1.827 MB/s SHA-512 750 KB took 1.009 seconds, 743.089 KB/s HMAC-MD5 15 MB took 1.000 seconds, 14.838 MB/s HMAC-SHA 6 MB took 1.003 seconds, 5.527 MB/s HMAC-SHA256 2 MB took 1.010 seconds, 1.812 MB/s HMAC-SHA512 750 KB took 1.025 seconds, 732.064 KB/s PBKDF2 256 bytes took 1.096 seconds, 233.619 bytes/s RSA 2048 public 26 ops took 1.027 sec, avg 39.488 ms, 25.324 ops/sec RSA 2048 private 2 ops took 1.104 sec, avg 551.800 ms, 1.812 ops/sec DH 2048 key gen 7 ops took 1.037 sec, avg 148.171 ms, 6.749 ops/sec DH 2048 agree 6 ops took 1.188 sec, avg 198.017 ms, 5.050 ops/sec ECC 256 key gen 7 ops took 1.070 sec, avg 152.843 ms, 6.543 ops/sec ECDHE 256 agree 8 ops took 1.228 sec, avg 153.550 ms, 6.513 ops/sec ECDSA 256 sign 8 ops took 1.272 sec, avg 159.025 ms, 6.288 ops/sec ECDSA 256 verify 4 ops took 1.249 sec, avg 312.150 ms, 3.204 ops/sec CURVE 25519 key gen 5 ops took 1.056 sec, avg 211.220 ms, 4.734 ops/sec CURVE 25519 agree 6 ops took 1.267 sec, avg 211.100 ms, 4.737 ops/sec ED 25519 key gen 204 ops took 1.003 sec, avg 4.916 ms, 203.410 ops/sec ED 25519 sign 154 ops took 1.004 sec, avg 6.517 ms, 153.448 ops/sec ED 25519 verify 66 ops took 1.018 sec, avg 15.418 ms, 64.858 ops/sec
More information on using wolfSSL in combination with Renesas and wolfSSL’s support for Renesas can be found here: https://www.wolfssl.com/docs/renesas/
Return to top of page
Platform:
Renesas: Renesas RX MPU (R5F571MLDDFC)
Benchmark:
These values were collected by running the wolfCrypt benchmark application on an Alpha Project board (AP-RX71M-0A)
wolfCrypt Benchmark (block bytes 1024, min 1.0 sec each) RNG 775 KB took 1.031 seconds, 751.916 KB/s AES-128-CBC-enc 2 MB took 1.006 seconds, 1.505 MB/s AES-128-CBC-dec 1 MB took 1.010 seconds, 1.450 MB/s AES-192-CBC-enc 1 MB took 1.010 seconds, 1.378 MB/s AES-192-CBC-dec 1 MB took 1.011 seconds, 1.328 MB/s AES-256-CBC-enc 1 MB took 1.019 seconds, 1.270 MB/s AES-256-CBC-dec 1 MB took 1.014 seconds, 1.227 MB/s AES-128-GCM-enc 675 KB took 1.025 seconds, 658.858 KB/s AES-128-GCM-dec 675 KB took 1.026 seconds, 658.087 KB/s AES-192-GCM-enc 650 KB took 1.027 seconds, 633.220 KB/s AES-192-GCM-dec 650 KB took 1.028 seconds, 632.603 KB/s AES-256-GCM-enc 625 KB took 1.025 seconds, 609.697 KB/s AES-256-GCM-dec 625 KB took 1.026 seconds, 609.102 KB/s RABBIT 9 MB took 1.001 seconds, 8.534 MB/s 3DES 475 KB took 1.035 seconds, 458.893 KB/s MD5 13 MB took 1.001 seconds, 13.275 MB/s SHA 5 MB took 1.002 seconds, 4.778 MB/s SHA-256 2 MB took 1.006 seconds, 1.650 MB/s SHA-384 675 KB took 1.034 seconds, 653.057 KB/s SHA-512 675 KB took 1.034 seconds, 652.994 KB/s HMAC-MD5 13 MB took 1.001 seconds, 13.142 MB/s HMAC-SHA 5 MB took 1.004 seconds, 4.768 MB/s HMAC-SHA256 2 MB took 1.014 seconds, 1.638 MB/s HMAC-SHA384 650 KB took 1.010 seconds, 643.437 KB/s HMAC-SHA512 650 KB took 1.011 seconds, 643.182 KB/s RSA 2048 public 26 ops took 1.067 sec, avg 41.038 ms, 24.367 ops/sec RSA 2048 private 2 ops took 1.157 sec, avg 578.500 ms, 1.729 ops/sec DH 2048 key gen 6 ops took 1.049 sec, avg 174.883 ms, 5.718 ops/sec DH 2048 agree 6 ops took 1.191 sec, avg 198.433 ms, 5.039 ops/sec ECC 256 key gen 7 ops took 1.162 sec, avg 165.943 ms, 6.026 ops/sec ECDHE 256 agree 8 ops took 1.323 sec, avg 165.325 ms, 6.049 ops/sec ECDSA 256 sign 6 ops took 1.044 sec, avg 174.017 ms, 5.747 ops/sec ECDSA 256 verify 4 ops took 1.281 sec, avg 320.300 ms, 3.122 ops/sec CURVE 25519 key gen 5 ops took 1.137 sec, avg 227.300 ms, 4.399 ops/sec CURVE 25519 agree 6 ops took 1.366 sec, avg 227.583 ms, 4.394 ops/sec ED 25519 key gen 198 ops took 1.003 sec, avg 5.064 ms, 197.467 ops/sec ED 25519 sign 146 ops took 1.005 sec, avg 6.885 ms, 145.245 ops/sec ED 25519 verify 62 ops took 1.001 sec, avg 16.147 ms, 61.932 ops/sec
More information on using wolfSSL in combination with Renesas and wolfSSL’s support for Renesas can be found here: https://www.wolfssl.com/docs/renesas/
Return to top of page
Platform:
Renesas: Renesas Synergy DK-S7G2
Benchmark:
Benchmarks using Renesas DK-S7G2 board (ThreadX + NetX) and wolfSSL 4.3.0 :
3X speed up with SHA256 operations, 1.5X speed up with AES, and over 4X speed up of public key operations when SP math was enabled.
Average TLS client connection times on the board with hardware acceleration and SP math :
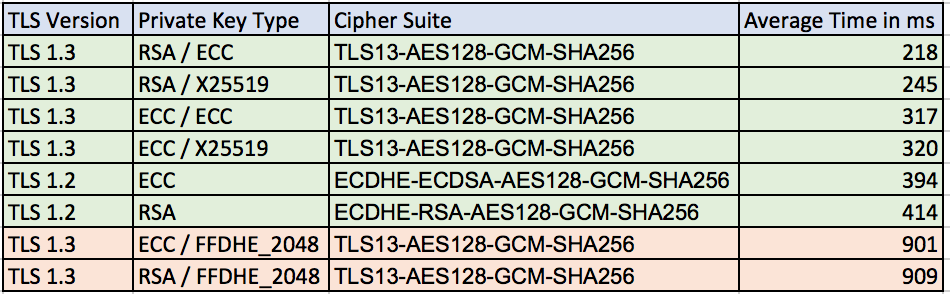
Software only speeds without SP math library:
AES-128-CBC-enc 2 MB took 1.010 seconds, 1.910 MB/s SHA-256 4 MB took 1.000 seconds, 3.638 MB/s HMAC-SHA256 4 MB took 1.010 seconds, 3.626 MB/s RSA 2048 public 24 ops took 1.080 sec, avg 45.000 ms, 22.222 ops/sec RSA 2048 private 2 ops took 1.840 sec, avg 920.000 ms, 1.087 ops/sec ECC 256 key gen 3 ops took 1.170 sec, avg 390.000 ms, 2.564 ops/sec ECDHE 256 agree 4 ops took 1.560 sec, avg 390.000 ms, 2.564 ops/sec ECDSA 256 sign 4 ops took 1.570 sec, avg 392.500 ms, 2.548 ops/sec ECDSA 256 verify 2 ops took 1.560 sec, avg 780.000 ms, 1.282 ops/sec
Hardware acceleration on plus use of SP math enabled:
AES-128-CBC-enc 3 MB took 1.010 seconds, 2.901 MB/s SHA-256 11 MB took 1.000 seconds, 11.353 MB/s HMAC-SHA256 11 MB took 1.000 seconds, 11.206 MB/s RSA 2048 public 94 ops took 1.010 sec, avg 10.745 ms, 93.069 ops/sec RSA 2048 private 4 ops took 1.530 sec, avg 382.500 ms, 2.614 ops/sec ECC 256 key gen 129 ops took 1.000 sec, avg 7.752 ms, 129.000 ops/sec ECDHE 256 agree 32 ops took 1.040 sec, avg 32.500 ms, 30.769 ops/sec ECDSA 256 sign 90 ops took 1.000 sec, avg 11.111 ms, 90.000 ops/sec ECDSA 256 verify 26 ops took 1.030 sec, avg 39.615 ms, 25.243 ops/sec
Time for Ed25519 and Curve25519:
CURVE 25519 key gen 36 ops took 1.020 sec, avg 28.333 ms, 35.294 ops/sec CURVE 25519 agree 36 ops took 1.010 sec, avg 28.056 ms, 35.644 ops/sec ED 25519 key gen 99 ops took 1.000 sec, avg 10.101 ms, 99.000 ops/sec ED 25519 sign 82 ops took 1.000 sec, avg 12.195 ms, 82.000 ops/sec ED 25519 verify 32 ops took 1.010 sec, avg 31.562 ms, 31.683 ops/sec
More information on using wolfSSL in combination with Renesas and wolfSSL’s support for Renesas can be found here: https://www.wolfssl.com/docs/renesas/
Return to top of page
Platform:
Benchmark:
 wolfSSL only:
wolfSSL only: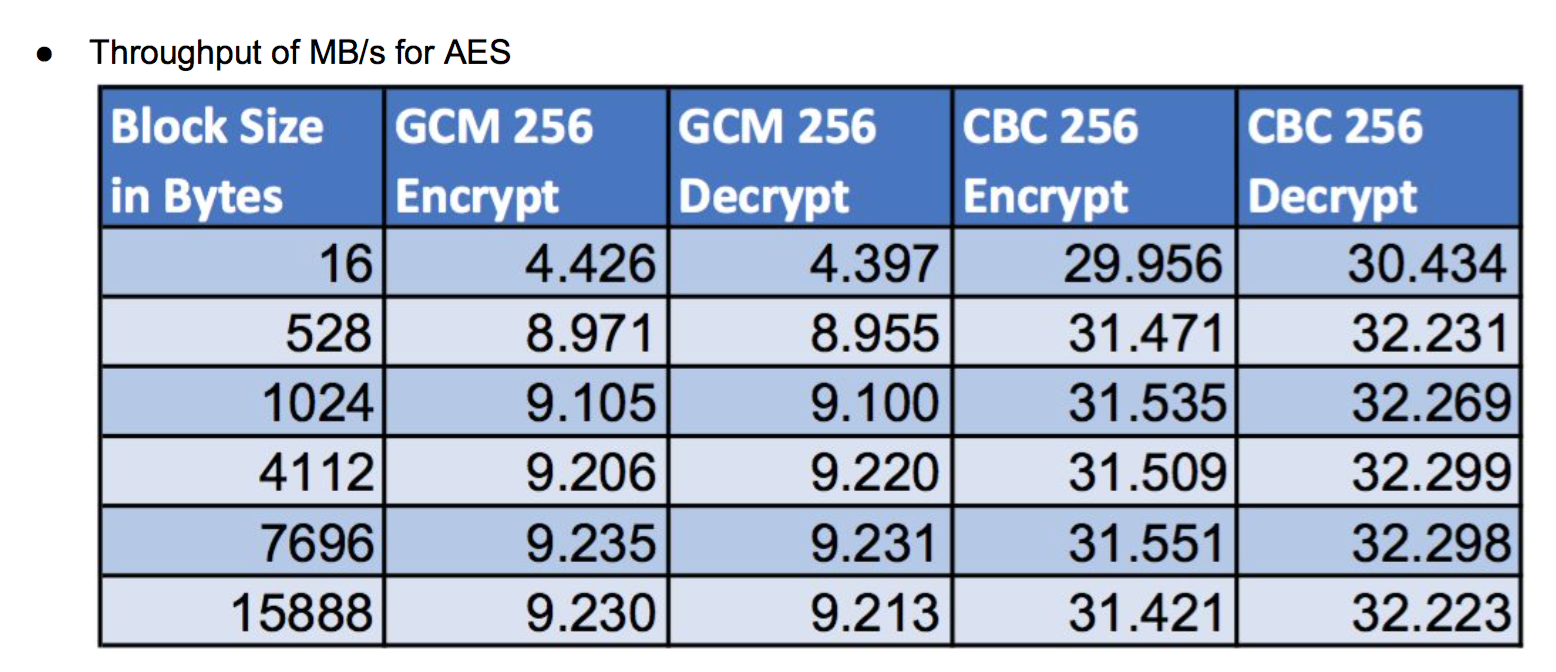
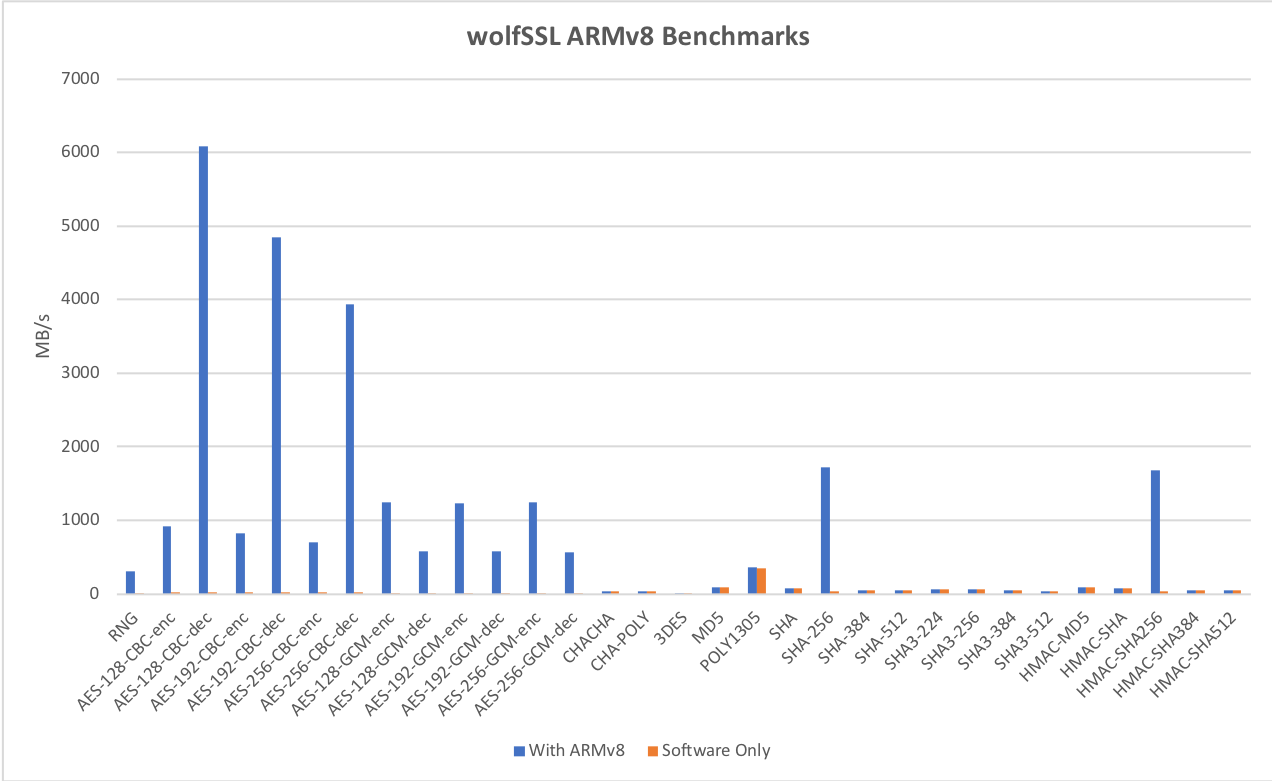
 wolfSSL and ARMv8:
wolfSSL and ARMv8: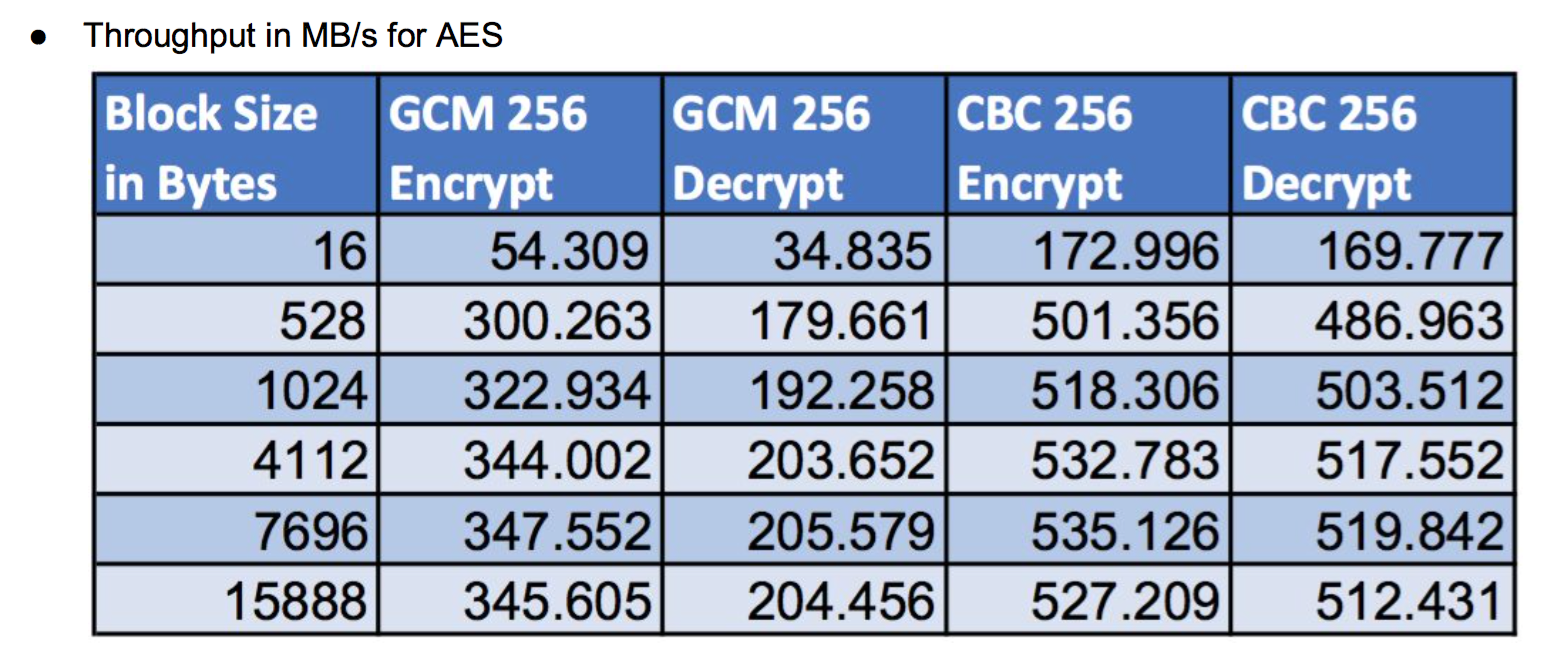
Platform:
Benchmark:
These benchmark values were collected with the fastmath library in use, on an esp32-wroom-32 with CPU speed:240MHz, ESP-IDF version v3.3-beta1-39-g6cb37ecc5(commit hash: 6cb37ecc5), and operating system Ubuntu 18.04.1 LTS (Bionic Beaver).Software encryption:
AES-128-CBC-enc 1 MB took 1.001 seconds, 1.146 MB/s AES-128-CBC-dec 1 MB took 1.017 seconds, 1.104 MB/s AES-192-CBC-enc 1 MB took 1.018 seconds, 1.055 MB/s AES-192-CBC-dec 1 MB took 1.006 seconds, 1.019 MB/s AES-256-CBC-enc 1000 KB took 1.000 seconds, 1000.000 KB/s AES-256-CBC-dec 975 KB took 1.007 seconds, 968.222 KB/s AES-128-GCM-enc 350 KB took 1.055 seconds, 331.754 KB/s AES-128-GCM-dec 350 KB took 1.054 seconds, 332.068 KB/s AES-192-GCM-enc 325 KB took 1.013 seconds, 320.829 KB/s AES-192-GCM-dec 325 KB took 1.013 seconds, 320.829 KB/s AES-256-GCM-enc 325 KB took 1.041 seconds, 312.200 KB/s AES-256-GCM-dec 325 KB took 1.041 seconds, 312.200 KB/s SHA 6 MB took 1.004 seconds, 5.714 MB/s SHA-256 2 MB took 1.006 seconds, 1.747 MB/s SHA-384 1 MB took 1.011 seconds, 1.159 MB/s SHA-512 1 MB took 1.009 seconds, 1.161 MB/s HMAC-SHA 6 MB took 1.001 seconds, 5.634 MB/s HMAC-SHA256 2 MB took 1.000 seconds, 1.733 MB/s HMAC-SHA384 1 MB took 1.004 seconds, 1.046 MB/s HMAC-SHA512 1 MB took 1.002 seconds, 1.048 MB/s RSA 2048 public 16 ops took 1.056 sec, avg 66.000 ms, 15.152 ops/sec RSA 2048 private 2 ops took 2.488 sec, avg 1244.000 ms, 0.804 ops/sec ECC 256 key gen 4 ops took 1.101 sec, avg 275.250 ms, 3.633 ops/sec ECDHE 256 agree 4 ops took 1.098 sec, avg 274.500 ms, 3.643 ops/sec ECDSA 256 sign 4 ops took 1.111 sec, avg 277.750 ms, 3.600 ops/sec ECDSA 256 verify 2 ops took 1.099 sec, avg 549.500 ms, 1.820 ops/sec
Hardware encryption
AES-128-CBC-enc 6 MB took 1.004 seconds, 5.958 MB/s AES-128-CBC-dec 5 MB took 1.002 seconds, 5.287 MB/s AES-192-CBC-enc 6 MB took 1.004 seconds, 5.958 MB/s AES-192-CBC-dec 5 MB took 1.002 seconds, 5.287 MB/s AES-256-CBC-enc 6 MB took 1.001 seconds, 5.951 MB/s AES-256-CBC-dec 5 MB took 1.004 seconds, 5.277 MB/s AES-128-GCM-enc 375 KB took 1.067 seconds, 351.453 KB/s AES-128-GCM-dec 375 KB took 1.067 seconds, 351.453 KB/s AES-192-GCM-enc 350 KB took 1.010 seconds, 346.535 KB/s AES-192-GCM-dec 350 KB took 1.009 seconds, 346.878 KB/s AES-256-GCM-enc 350 KB took 1.016 seconds, 344.488 KB/s AES-256-GCM-dec 350 KB took 1.016 seconds, 344.488 KB/s SHA 14 MB took 1.000 seconds, 14.062 MB/s SHA-256 15 MB took 1.000 seconds, 15.234 MB/s SHA-384 17 MB took 1.000 seconds, 17.383 MB/s SHA-512 18 MB took 1.001 seconds, 17.512 MB/s HMAC-SHA 14 MB took 1.000 seconds, 13.818 MB/s HMAC-SHA256 15 MB took 1.001 seconds, 14.951 MB/s HMAC-SHA384 17 MB took 1.001 seconds, 16.683 MB/s HMAC-SHA512 17 MB took 1.000 seconds, 16.943 MB/s RSA 2048 public 20 ops took 1.017 sec, avg 50.850 ms, 19.666 ops/sec RSA 2048 private 4 ops took 1.059 sec, avg 264.750 ms, 3.777 ops/sec ECC 256 key gen 4 ops took 1.092 sec, avg 273.000 ms, 3.663 ops/sec ECDHE 256 agree 4 ops took 1.089 sec, avg 272.250 ms, 3.673 ops/sec ECDSA 256 sign 4 ops took 1.101 sec, avg 275.250 ms, 3.633 ops/sec ECDSA 256 verify 2 ops took 1.092 sec, avg 546.000 ms, 1.832 ops/sec
Return to top of page
Platform:
Intel x86_64:
Benchmark:
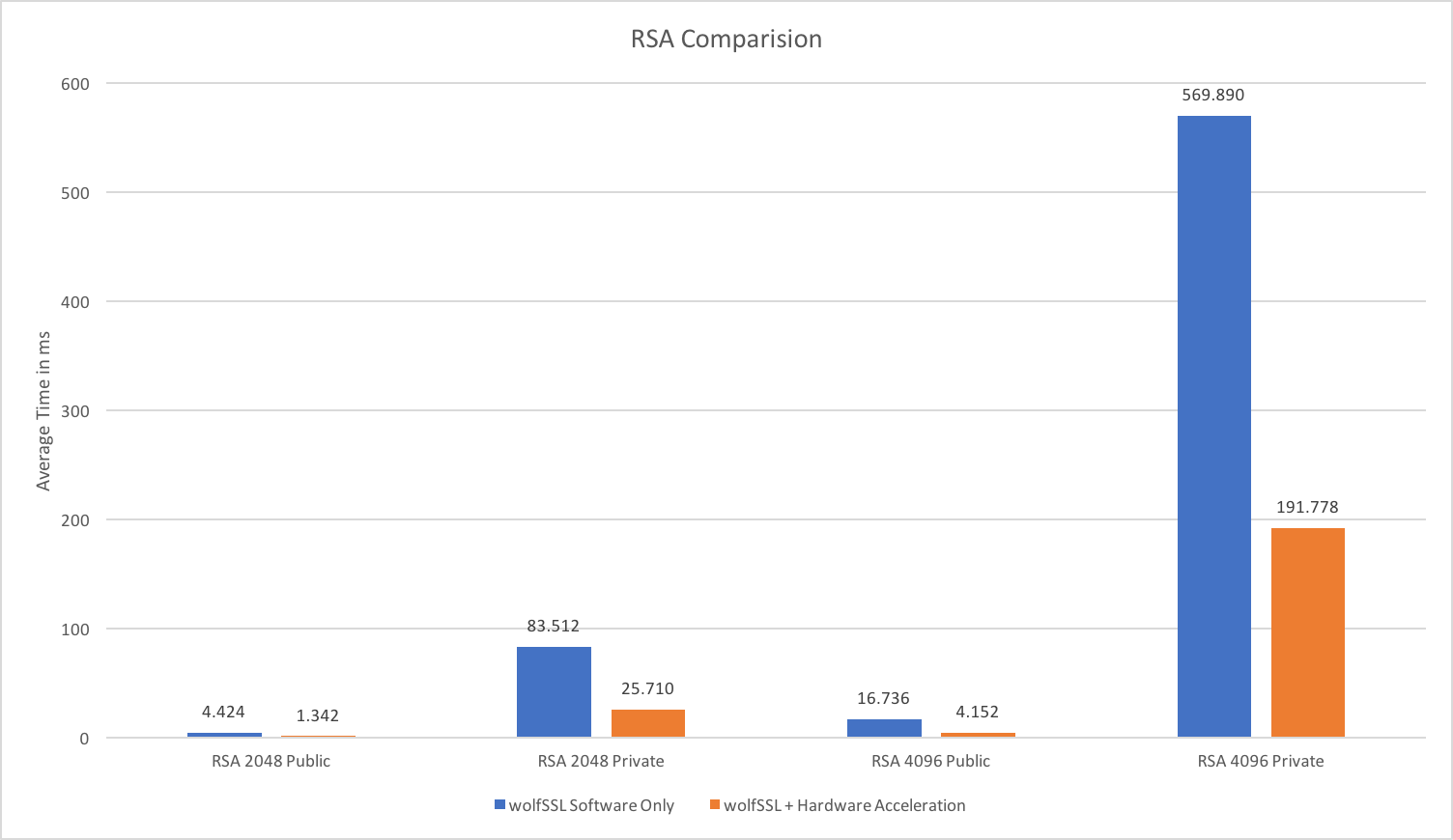
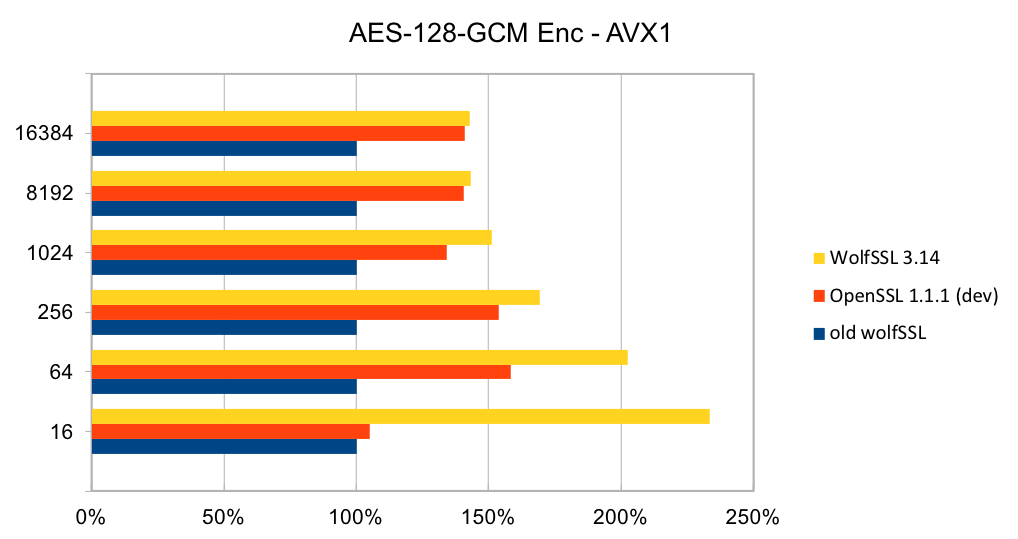
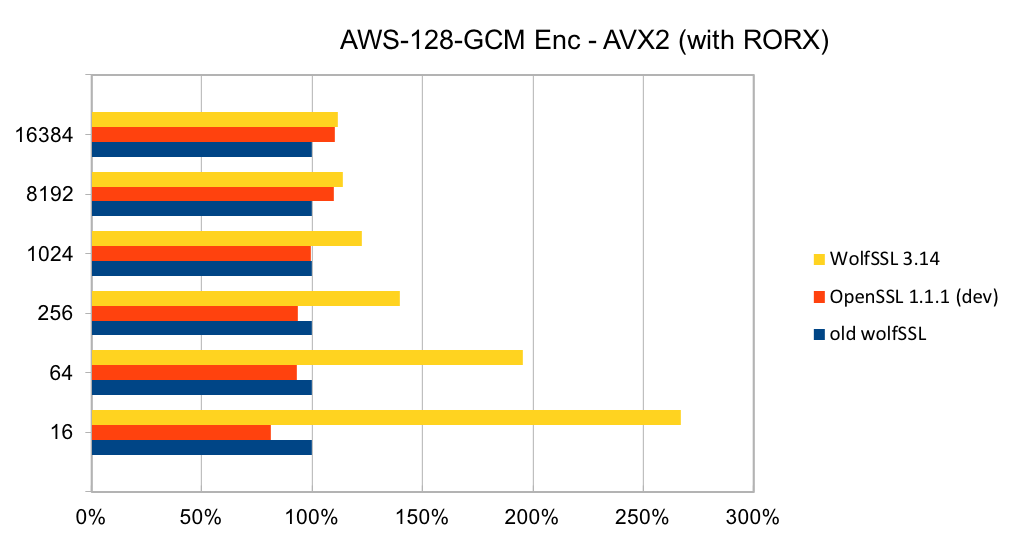
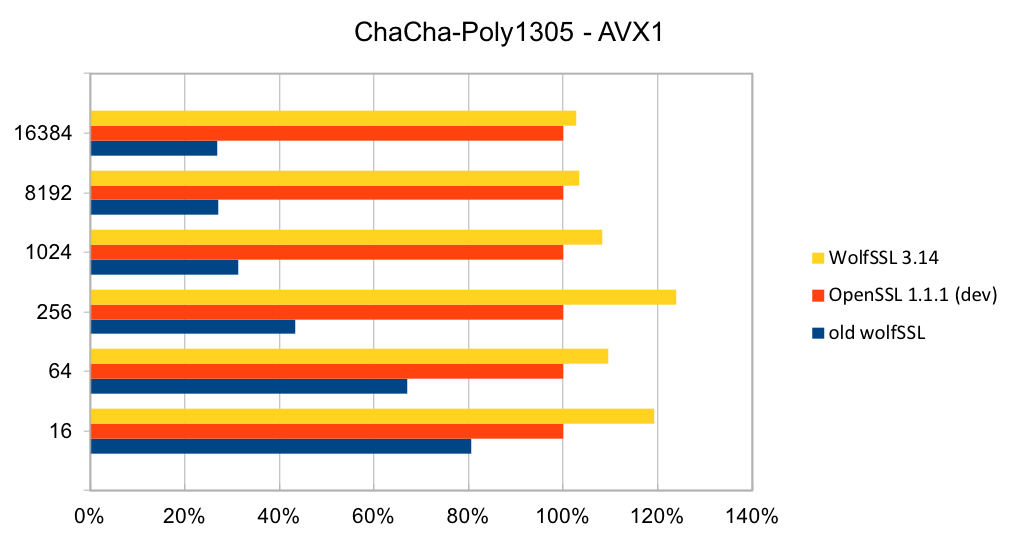
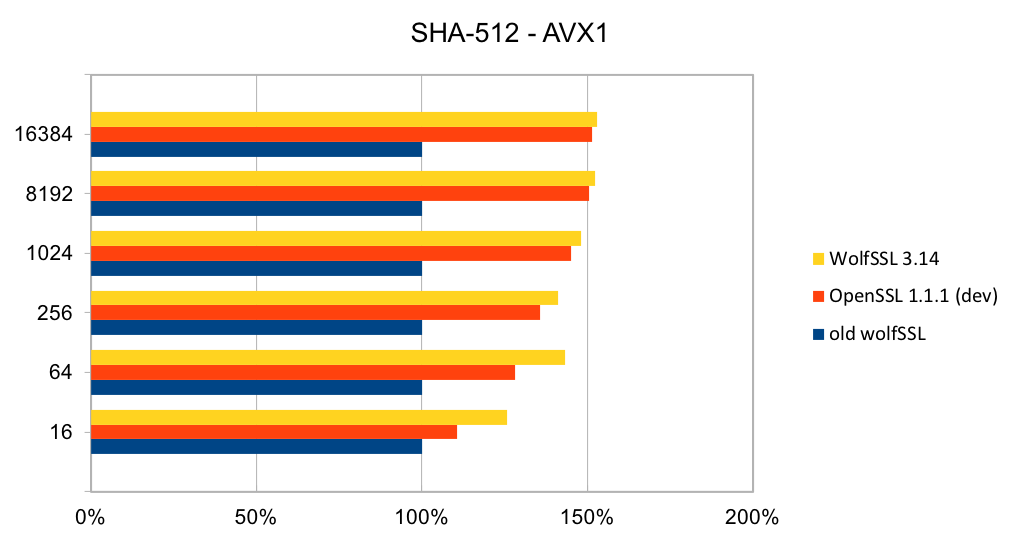
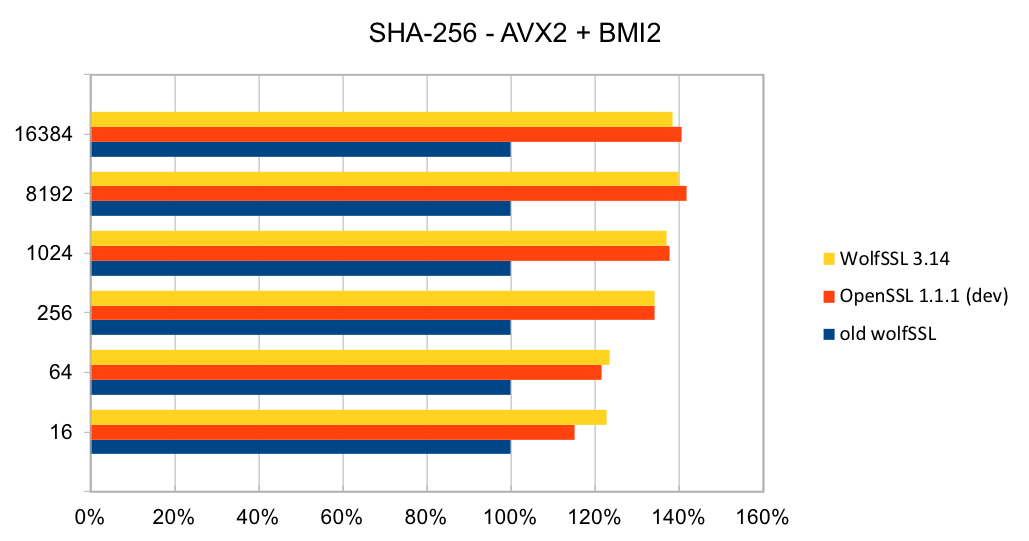
Recent releases of wolfSSL have included new assembly code targeted at the Intel x86_64 platform. Large performance gains have been made, and the first two graphs pertain to performance increases with AES-GCM.In the graphs for these benchmarks, the Y-axis signifies block size, while the X-axis signifies relative speed to the prior version of wolfSSL.
The assembly code for AES-GCM has been rewritten to take best advantage of the AVX1 and AVX2 instructions. The performance of AES-GCM is now as good or better than OpenSSL.
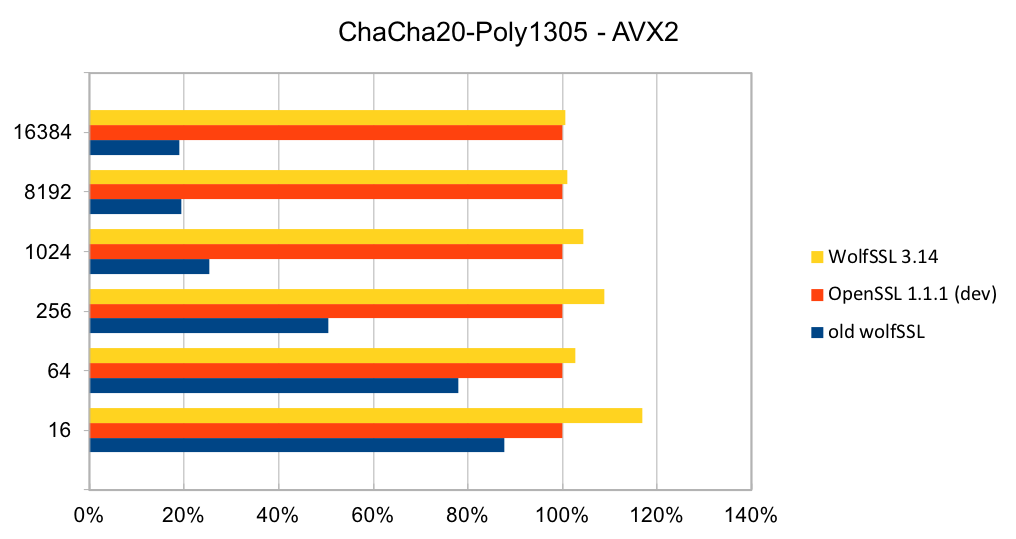
ChaCha20-Poly1305 is a relatively new authenticated encryption algorithm. It was designed as an alternative to AES-GCM. The algorithm is simple and fast on CPUs that do not have hardware acceleration for AES and GCM.
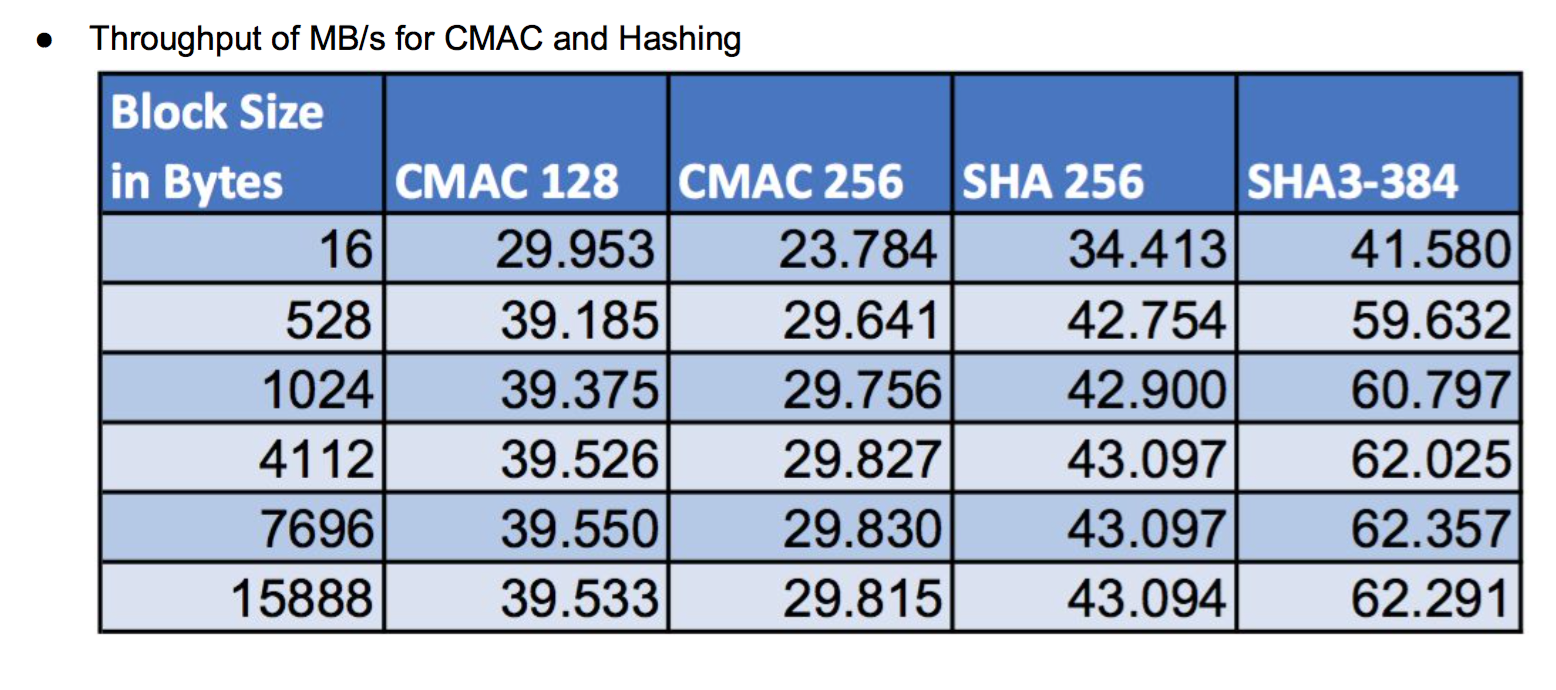
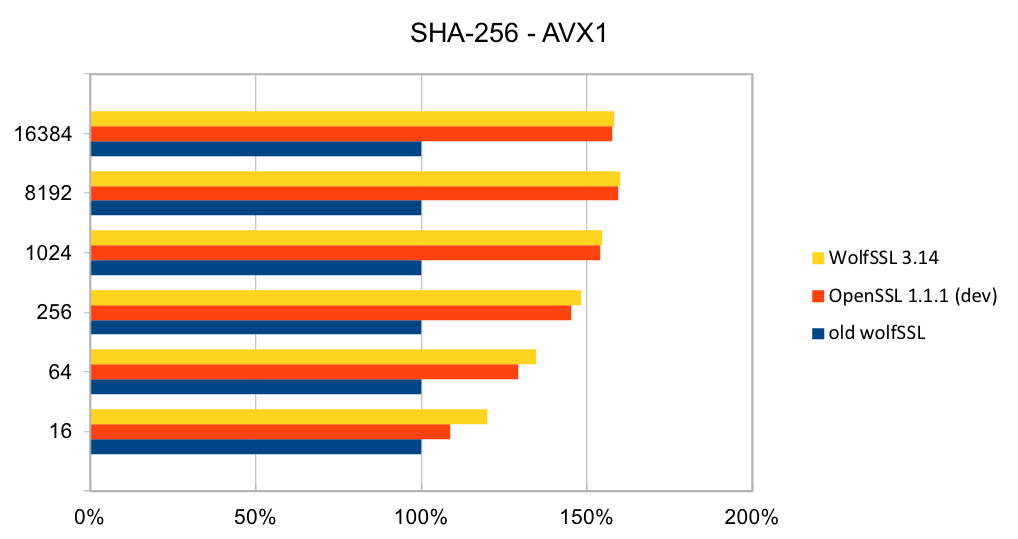
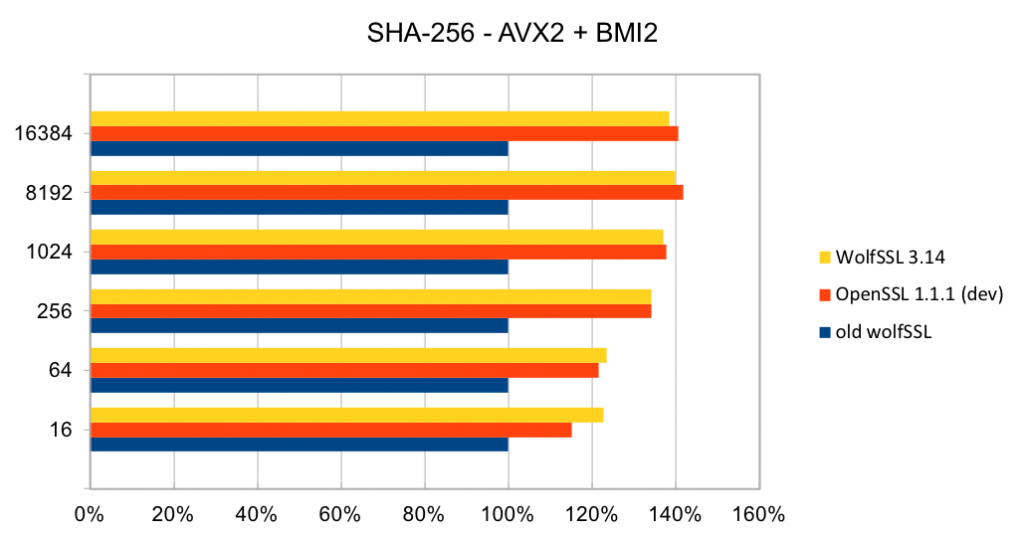
The most commonly used digest algorithms are SHA-256 and SHA-384. With the introduction of AES-GCM in TLS, SHA-256 and SHA-384 are less commonly used for application data authentication. But, they are still used for handshake message authentication, as a one-way function (as required in a pseudo-random number generator) and digital signatures.
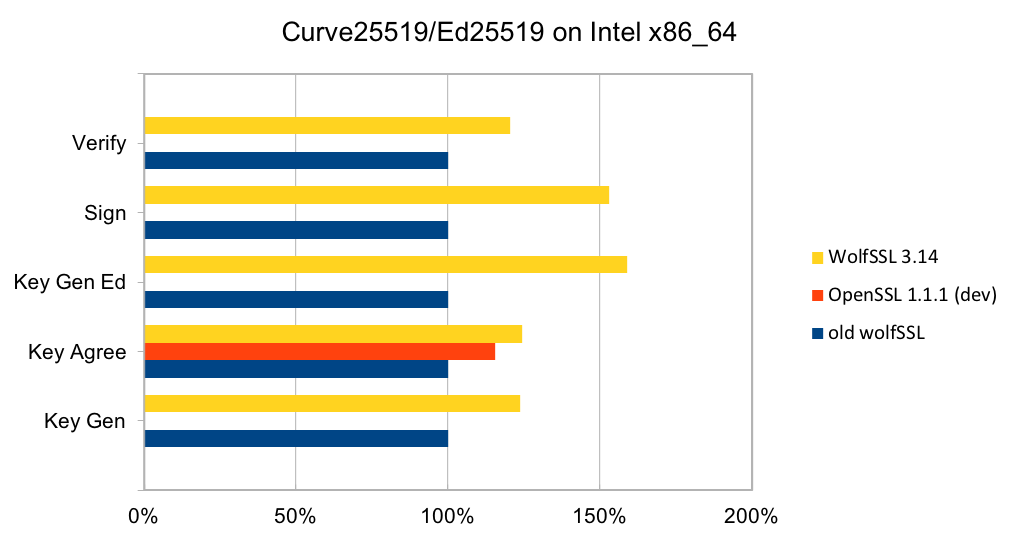
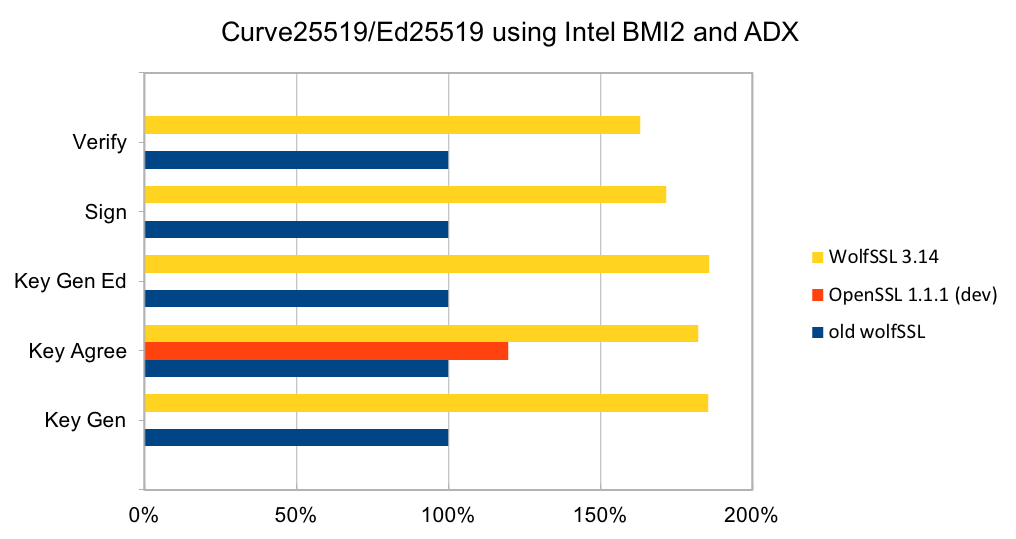
Curve25519 is set of parameters for a Montgomery elliptic curve and has ~128-bit security. It is used in key exchange and has become popular due to its speed and inclusion in standards. The algorithm is included as part of TLS v1.3 and NIST is considering it as part of SP 800-186. Ed25519 is set of parameters for a Twisted Edwards curve and is mathematically related to Curve25519 and has the same security properties. A new signature scheme has been designed over Twisted Edwards curves that is fast and included as part of TLS v1.3. A draft specification has been written describing digital certificates using EdDSA with Ed25519.
RSA is the most commonly used public key algorithm for certificates. When performing a TLS handshake, the server will sign a hash of the messages seen so far and the client will verify the signature of certificates in the certificate chain and verify the hash of messages with the public key in the certificate. Signing and verifying are the most time-consuming operations in a handshake.
DH has been the key exchange algorithm of choice in handshakes but is falling out of favor as the Elliptic Curve variants are considerably faster at the same security level. Performing the key exchange is the second most time-consuming operation in a TLS handshake.
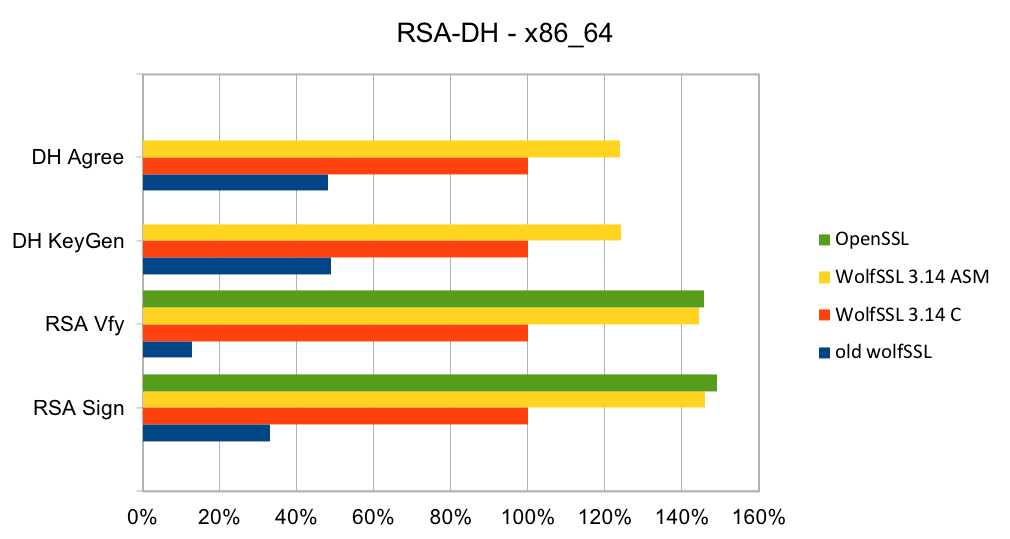
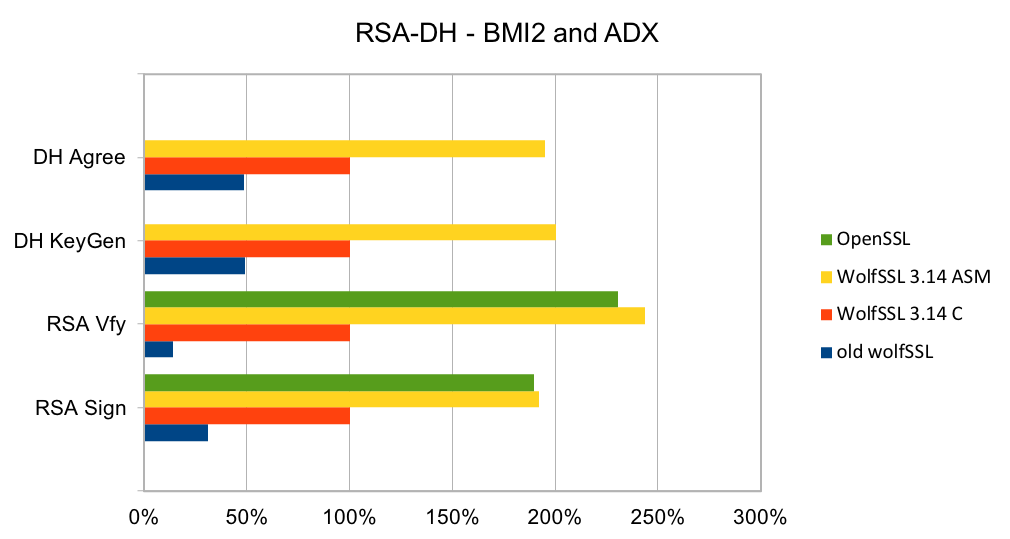
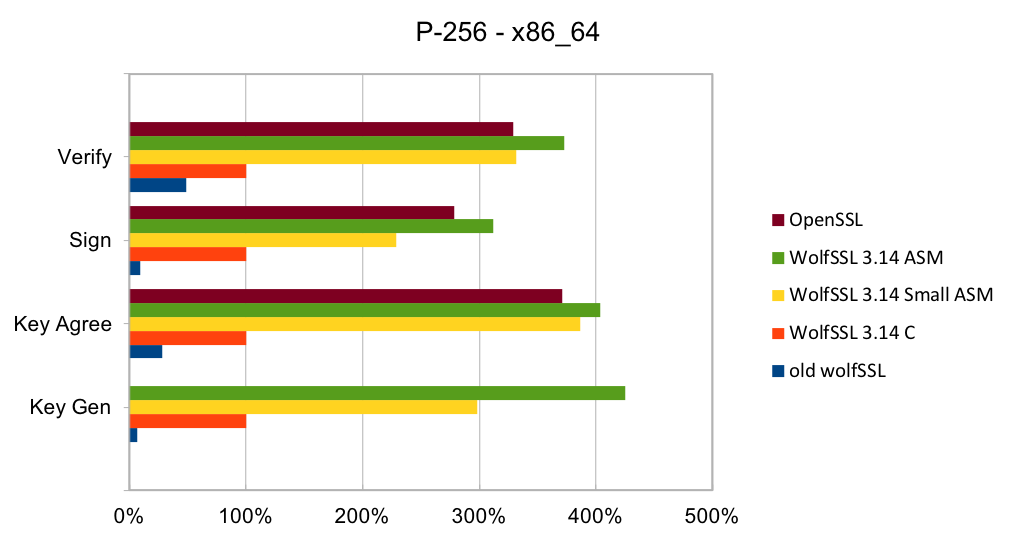
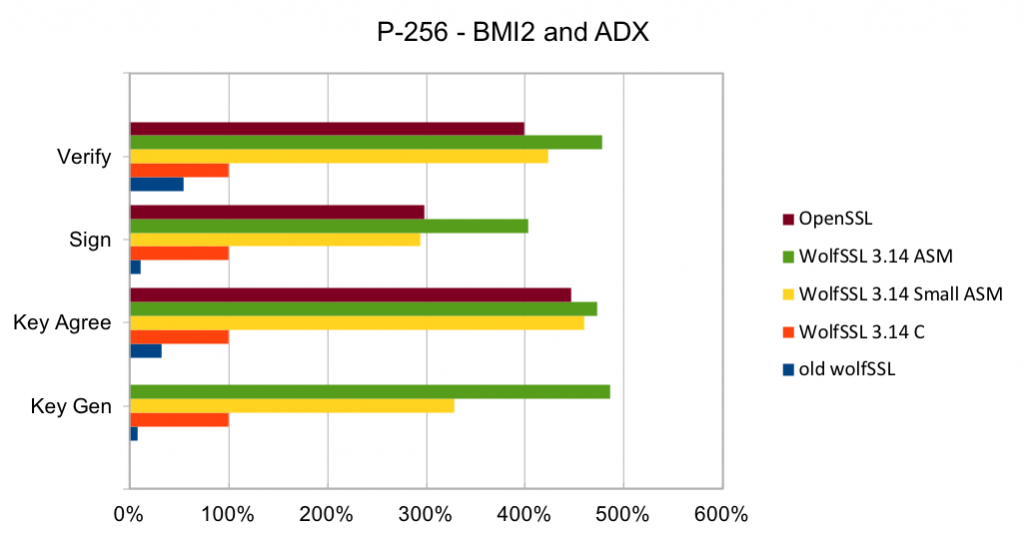
Elliptic curve cryptography (ECC) is the alternative to finite field (FF) cryptography which has algorithms like RSA, DSA and DH. ECDSA is the elliptic curve variant of RSA and DSA while ECDH is the elliptic curve variant of DH. ECDSA and ECDH can be used anywhere their FF counterparts can be used. ECC requires a pre-defined curve to perform the operations on. The most commonly used curve is P-256 as it has 128-bit strength and is in many standards including TLS, for certificates in IETF, and NIST’s FIPS 186-4. Browsers and web servers are preferring ECDH over DH as it is much faster.
If you have questions about using the wolfSSL embedded TLS library on your platform, or about performance optimization of the library, contact us at support@wolfssl.com.
Return to top of page
Platform:
NXP i.MX6
Benchmark:
This benchmark data was collected for Green Hills INTEGRITY OS on an NXP i.MX6, running the wolfSSL benchmark application.
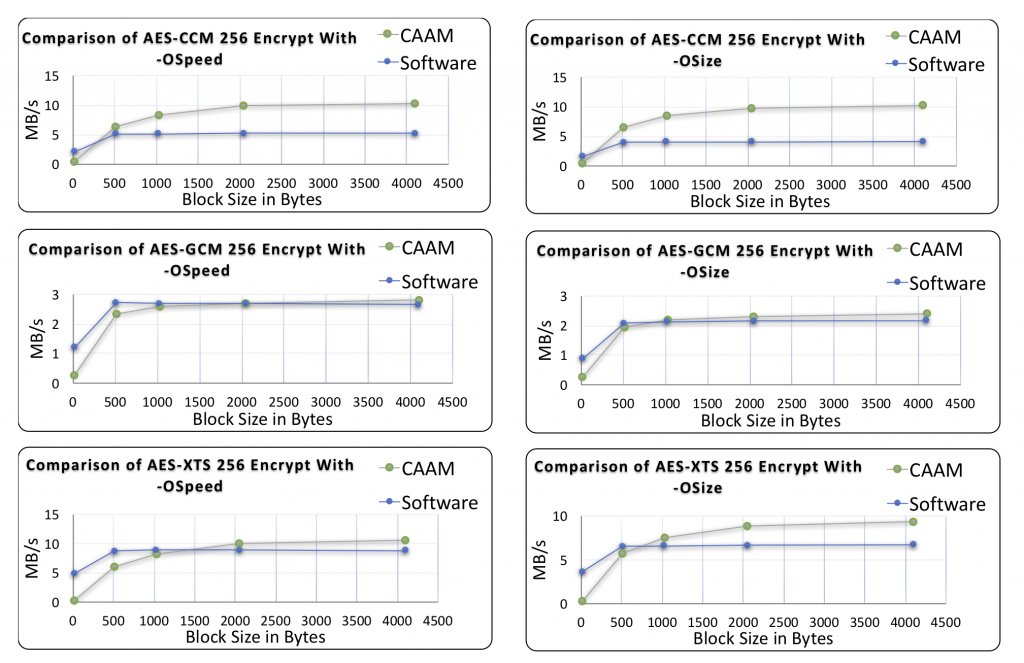
Return to top of page
Platform:
iPhone X:
Benchmark:
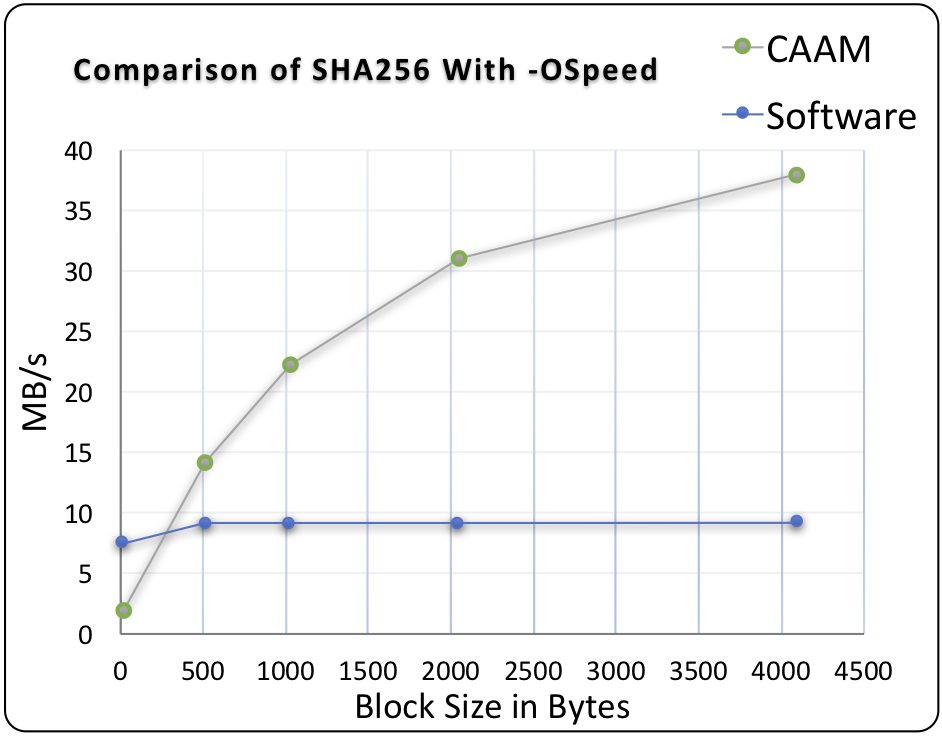
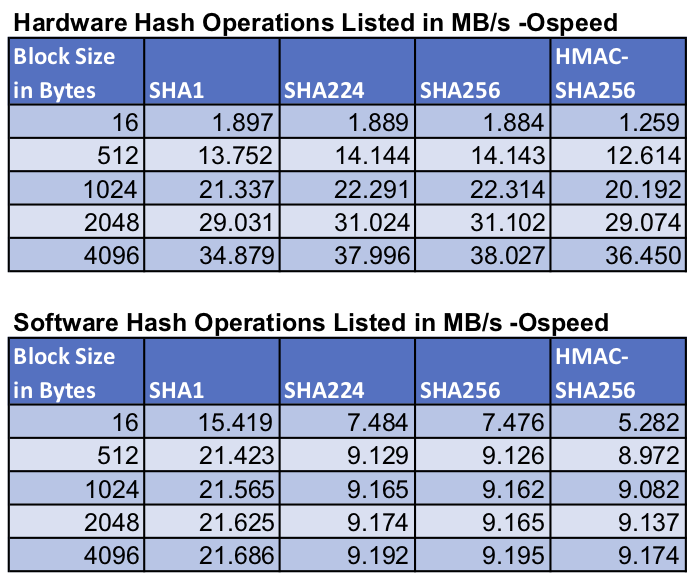
Benchmarks were collected using Apple’s iPhone X, which has their new A11 processor. These benchmarks use ARMv8 crypto extensions and single precision math to demonstrate performance.
For symmetric AES and SHA using our ARMv8 crypto assembly speedups we see
| Algorithm | Performance |
|---|---|
| AES-128 CBC Encrypt | 912.347 MB/s (36.58X) |
| AES-128 CBC Decrypt | 6,084.83 MB/s (256.15X) |
| AES-128 GCM Encrypt | 1,242.28 MB/s (193.65X) |
| AES-128 GCM Decrypt | 575.83 MB/s (90.26X) |
| SHA-256 | 1,717.28 MB/s (56.11X) |
This feature is enabled using `./configure –enable-armasm` or the `WOLFSSL_ARMASM` define.
For asymmetric RSA, DH and ECC using our single precision math speedups we see
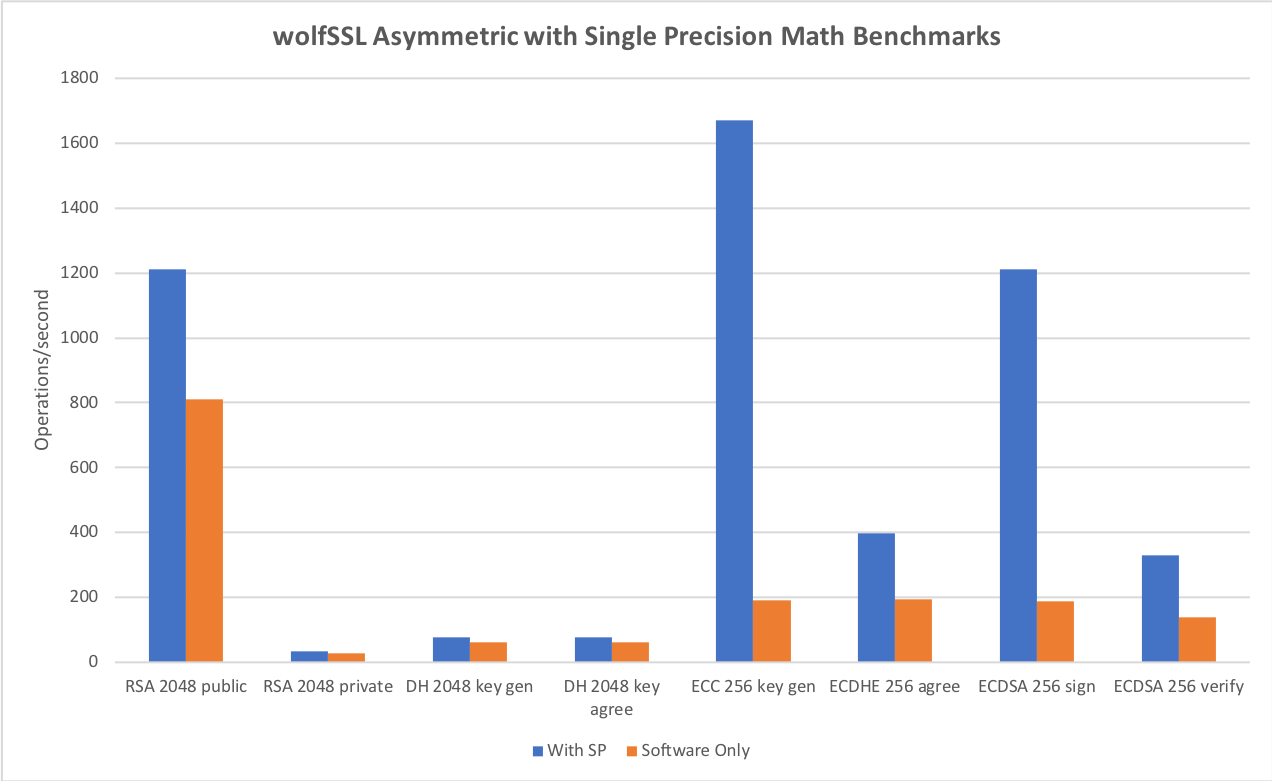
| Algorithm | Performance |
|---|---|
| RSA 2048 public | 1,211.27 ops/sec (1.50X) |
| RSA 2048 private | 32.59 ops/sec (1.18X) |
| DH 2048 key gen | 77.44 ops/sec (1.24X) |
| DH 2048 key agree | 77.45 ops/sec (1.29X) |
| ECC 256 key gen | 1670.65 ops/sec (8.67X) |
| ECDHE 256 agree | 396.88 ops/sec (2.05X) |
| ECDSA 256 sign | 1,212.33 ops/sec (6.42X) |
| ECDSA 256 verify | 331.02 ops/sec (2.38X) |
This feature is enabled using `./configure –enable-sp` or the `WOLFSSL_HAVE_SP_RSA`, `WOLFSSL_HAVE_SP_DH` and `WOLFSSL_HAVE_SP_ECC` defines.
For TLS v1.2 we see the following performance benchmarks by cipher suite
| Algorithm | Performance |
|---|---|
| DHE-RSA-AES128-SHA256 | CPS 22.5, Read 388 MB/s, Write 106 MB/s |
| ECDHE-RSA-AES128-GCM-SHA256 | CPS 26.2, Read 598 MB/s RX, Write 125 MB/s |
| ECDHE-ECDSA-AES128-GCM-SHA256 | CPS 83.4, Read 504.8 MB/s, Write 92.2 MB/s |
Benchmarks done on iPhone X using a single thread and our wolfCrypt and wolfSSL benchmark tools.
`X`= performance increase as compared to our default software based implementation.
`CPS` = Connections per second
Reference: wolfCrypt/wolfSSL Benchmarks with iPhone 8/8 Plus/X (A11) blog post
Return to top of page
Platform:
Microchip PIC32MZ:
PIC32MZ, at 200MHz
Benchmark:
Benchmarks were collected using PIC32MZ Ethernet Starter Kit, using the wolfCrypt benchmark application and compiled with MPLAB X.
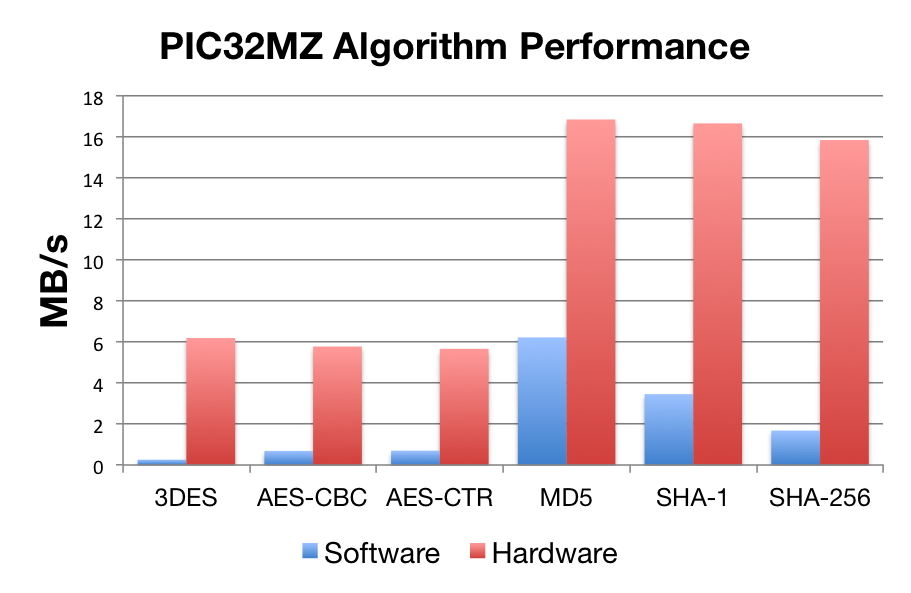
| Software Crypto | Hardware Crypto | |
| AES-CBC | 0.26 Mb/s | 5.78 Mb/s |
| AES-CTR | 0.69 Mb/s | 5.67 Mb/s |
| 3DES | 6.19 Mb/s | 6.19 Mb/s |
| MD5 | 6.22 Mb/s | 16.84 Mb/s |
| SHA-1 | 3.46 Mb/s | 16.65 Mb/s |
| SHA-256 | 1.678 Mb/s | 15.84 Mb/s |
Reference:
Return to top of page
Platform:
STM32:
STM32F439, at 180MHz
STM32F756, at 216MHz
Benchmark:
Benchmarks were collected using STMicroelectronics Evaluation Boards, using the wolfCrypt benchmark application and compiled with IAR EWARM (Optimization: High/Size).
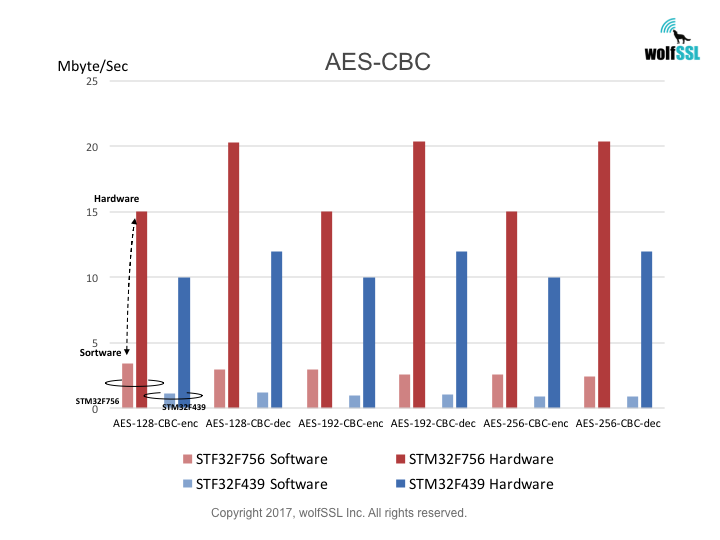
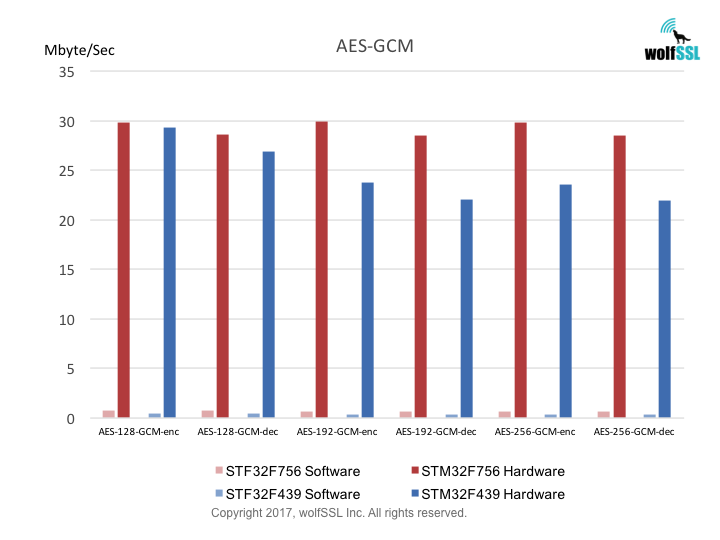
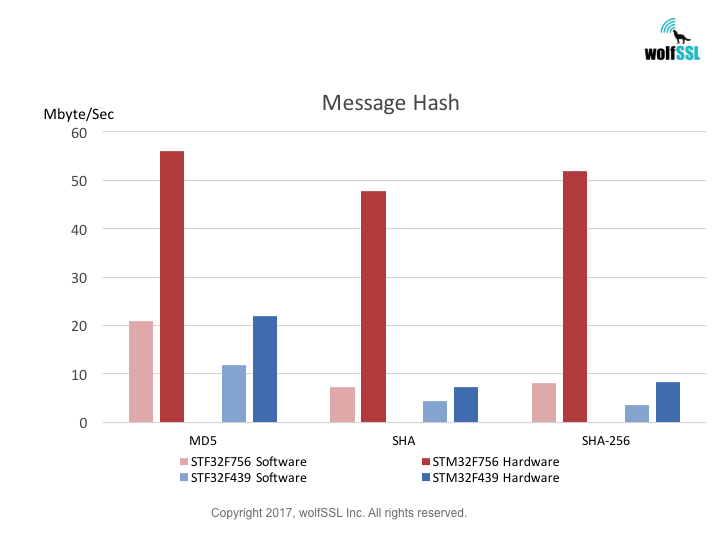
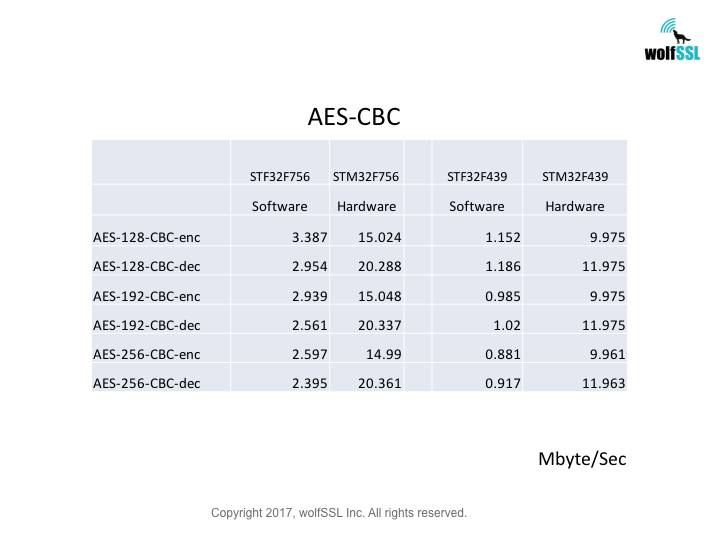
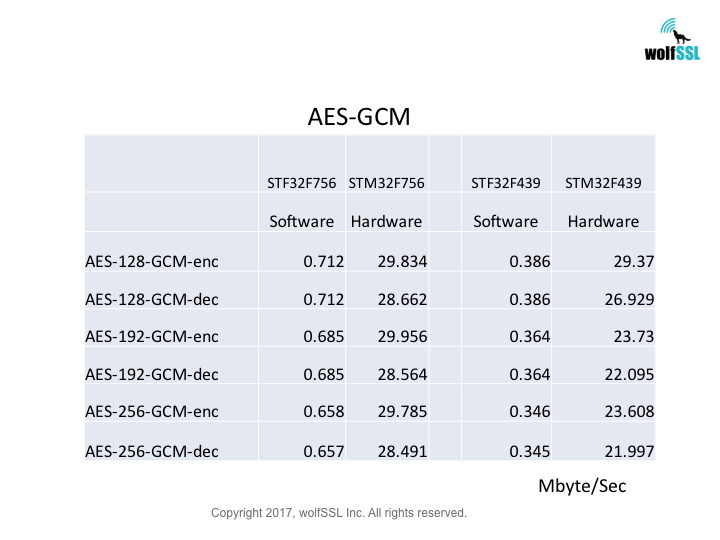
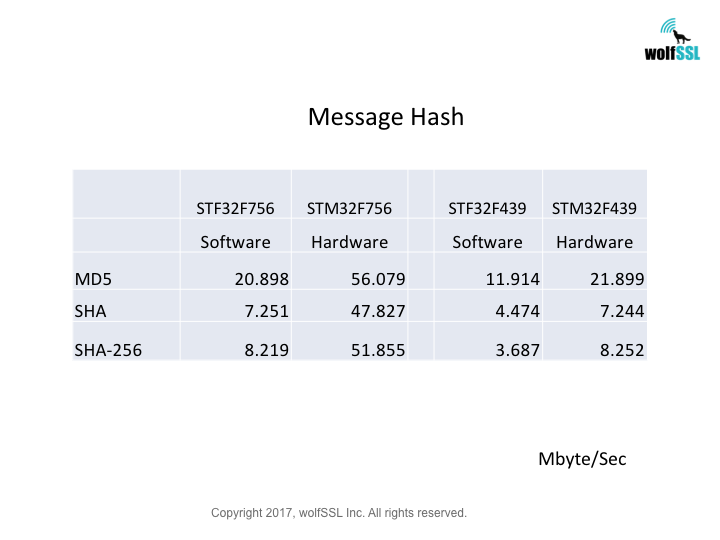
Reference:
Return to top of page
Platform:
STM32F777NI:
ARM Cortex M7
216 MHz
Using GCC ARM (arm-none-eabi-gcc) with OpenSTM32 (System Workbench)
Bare Metal
Benchmark:
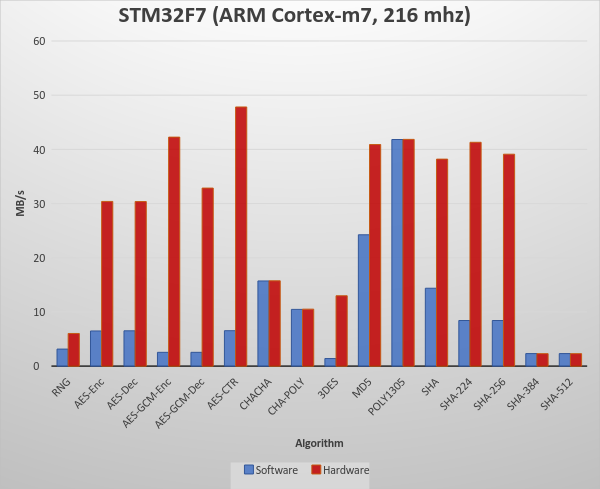
Crypto Benchmarks:
wolfSSL Software Crypto, Normal Big Integer Math Library
| RNG | 3 MB took 1.000 seconds | 3.149 MB/s |
| AES-Enc | 6 MB took 1.000 seconds | 6.494 MB/s |
| AES-Dec | 7 MB took 1.000 seconds | 6.519 MB/s |
| AES-GCM-Enc | 3 MB took 1.004 seconds | 553 MB/s |
| AES-GCM-Dec | 3 MB took 1.004 seconds | 2.553 MB/s |
| AES-CTR | 7 MB took 1.000 seconds | 6.543 MB/s |
| CHACHA | 16 MB took 1.000 seconds | 15.723 MB/s |
| CHA-POLY | 10 MB took 1.000 seconds | 10.474 MB/s |
| 3DES | 1 MB took 1.008 seconds | 1.405 MB/s |
| MD5 | 24 MB took 1.000 seconds | 24.243 MB/s |
| POLY1305 | 42 MB took 1.000 seconds | 41.821 MB/s |
| SHA | 14 MB took 1.000 seconds | 14.380 MB/s |
| SHA-224 | 8 MB took 1.000 seconds | 8.423 MB/s |
| SHA-256 | 8 MB took 1.000 seconds | 8.423 MB/s |
| SHA-384 | 2 MB took 1.000 seconds | 2.319 MB/s |
| SHA-512 | 2 MB took 1.000 seconds | 2.319 MB/s |
STM32F7 Hardware Crypto, Normal Big Integer Math Library
| RNG | 6 MB took 1.000 seconds | 6.030 MB/s |
| AES-Enc | 30 MB took 1.000 seconds | 30.396 MB/s |
| AES-Dec | 30 MB took 1.000 seconds | 30.371 MB/s |
| AES-GCM-Enc | 42 MB took 1.000 seconds | 42.261 MB/s |
| AES-GCM-Dec | 33 MB took 1.000 seconds | 32.861 MB/s |
| AES-CTR | 48 MB took 1.000 seconds | 47.827 MB/s |
| CHACHA | 16 MB took 1.000 seconds | 15.747 MB/s |
| CHA-POLY | 11 MB took 1.000 seconds | 10.522 MB/s |
| 3DES | 13 MB took 1.000 seconds | 12.988 MB/s |
| MD5 | 41 MB took 1.000 seconds | 40.894 MB/s |
| POLY1305 | 42 MB took 1.000 seconds | 41.846 MB/s |
| SHA | 38 MB took 1.004 seconds | 38.202 MB/s |
| SHA-224 | 41 MB took 1.000 seconds | 41.309 MB/s |
| SHA-256 | 39 MB took 1.000 seconds | 39.111 MB/s |
| SHA-384 | 2 MB took 1.004 seconds | 2.310 MB/s |
| SHA-512 | 2 MB took 1.004 seconds | 2.310 MB/s |
Reference:
wolfSSL and STM32F7
STM32F77NI
Return to top of page
Platform:
Apple A11 Bionic
2.39 GHz hexa-core 64-bit
Benchmark:
Benchmarks on Apple’s new A11 processor in their latest iPhone 8 / 8 Plus and iPhone X. This processor features six ARMv8 CPU cores (2 high-performance 2.53GHz and 4 high-efficiency 1.42GHz). The benchmarks use wolfSSL’s latest speedups for ARMv8 crypto extensions and single precision math to demonstrate our exceptional performance.For symmetric AES and SHA using our ARMv8 crypto assembly speedups we see:
AES-128 CBC Encrypt: 912.347 MB/s (36.58X) AES-128 CBC Decrypt: 6,084.83 MB/s (256.15X) AES-128 GCM Encrypt: 1,242.28 MB/s (193.65X) AES-128 GCM Decrypt: 575.83 MB/s (90.26X) SHA-256: 1,717.28 MB/s (56.11X)
This feature is enabled using `./configure –enable-armasm` or the `WOLFSSL_ARMASM` define.
For asymmetric RSA, DH and ECC using our single precision math speedups we see:
RSA 2048 public: 1,211.27 ops/sec (1.50X) RSA 2048 private: 32.59 ops/sec (1.18X) DH 2048 key gen: 77.44 ops/sec (1.24X) DH 2048 key agree: 77.45 ops/sec (1.29X) ECC 256 key gen: 1670.65 ops/sec (8.67X) ECDHE 256 agree: 396.88 ops/sec (2.05X) ECDSA 256 sign: 1,212.33 ops/sec (6.42X) ECDSA 256 verify: 331.02 ops/sec (2.38X)
This feature is enabled using `./configure –enable-sp` or the `WOLFSSL_HAVE_SP_RSA`, `WOLFSSL_HAVE_SP_DH` and `WOLFSSL_HAVE_SP_ECC` defines.
For TLS v1.2 we see the following performance benchmarks by cipher suite:
DHE-RSA-AES128-SHA256: CPS 22.5, Read 388 MB/s, Write 106 MB/s ECDHE-RSA-AES128-GCM-SHA256: CPS 26.2, Read 598 MB/s RX, Write 125 MB/s ECDHE-ECDSA-AES128-GCM-SHA256: CPS 83.4, Read 504.8 MB/s, Write 92.2 MB/s
Benchmarks done on iPhone X using a single thread and our wolfCrypt and wolfSSL benchmark tools.
`X`= performance increase as compared to our default software based implementation.
`CPS` = Connections per second
You can download the raw benchmark numbers here:
https://www.wolfssl.com/files/benchmarks/iOSiPhoneXA11Benchmarks.pdf
Reference
wolfSSL Blog Post
Return to top of page
Platform:
Benchmark:
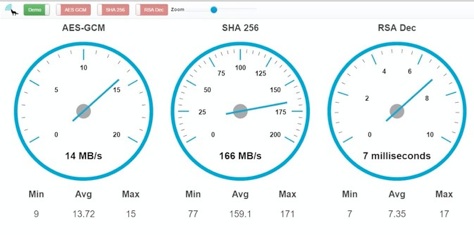
Benchmarks of wolfCrypt running in an Intel SGX enclave. These benchmarks show that running wolfCrypt cryptography inside SGX has minimal performance impact on cryptography operation.
Non-SGX Benchmarks
SHA-256 0.264s 189.078 MB/s
AES-GCM 3.142s 15.911 MB/s
RSA (2048) Encrypt 0.238 ms
RSA (2048) Decrypt 6.239 ms
SGX Benchmarks, Inside the Enclave
SHA-256 0.263s 190.436 MB/s -0.38% difference
AES-GCM 3.128s 15.985 MB/s -0.45% difference
RSA (2048) Encrypt 0.245 ms 2.94% difference
RSA (2048) Decrypt 6.242 ms 0.05% difference
Reference
Intel Software Guard Extensions (SGX) SDK
Return to top of page
Platform:
Benchmark:
Crypto Benchmarks:
Benchmarks using wolfSSL’s asynchronous benchmark application running multiple threads with CPU affinity in user space:
RSA 2048 public: 209,909 ops/sec
RSA 2048 private: 41,999 ops/sec
DH 2048 key gen: 112,491 ops/sec
DH 2048 key agree: 95,129 ops/sec
ECDHE 256 agree: 55,117 ops/sec
ECDSA 256 sign: 46,798 ops/sec
ECDSA 256 verify: 28,917 ops/sec
AES-CBC Enc: 2,932 MB/s
AES-CBC Dec: 2,882 MB/s
AES-GCM: 2,903 MB/s
3DES: 1,511 MB/s
MD5: 2,309 MB/s
SHA: 5,068 MB/s
SHA-224: 2,392 MB/s
SHA-256: 1,275 MB/s
SHA-384: 2,020 MB/s
SHA-512: 1,908 MB/s
Reference
wolfSSL Blog Post
Intel QuickAssist
Return to top of page
Platform:
HiKey LeMaker (ARMv8)
Kirin 620 SoC
ARM® CortexTM-A53 Octa-core 64-bit up to 1.2GHz (ARM v8 instruction set)
8GB eMMC storage
1GB RAM
Benchmark:
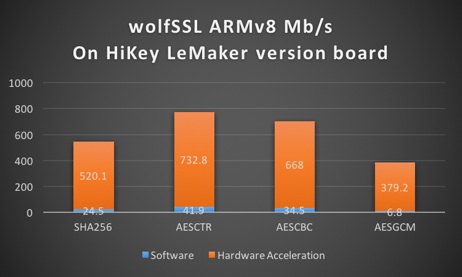
Below is the complete data from the benchmarks comparing hardware acceleration to normal software crypto:
| Algorithm | Software Cryptography | Hardware Cryptography |
|---|---|---|
| RNG | 16.761 MB/s | 82.599 MB/s |
| AES-128-CBC-enc | 26.491 MB/s | 649.179 MB/s |
| AES-128-CBC-dec | 26.915 MB/s | 607.407 MB/s |
| AES-192-CBC-enc | 22.796 MB/s | 566.717 MB/s |
| AES-192-CBC-dec | 23.130 MB/s | 553.092 MB/s |
| AES-256-CBC-enc | 20.004 MB/s | 504.143 MB/s |
| AES-256-CBC-dec | 20.207 MB/s | 491.374 MB/s |
| AES-128-GCM-enc | 6.224 MB/s | 393.407 MB/s |
| AES-128-GCM-dec | 6.226 MB/s | 182.279 MB/s |
| AES-192-GCM-enc | 5.895 MB/s | 361.801 MB/s |
| AES-192-GCM-dec | 5.895 MB/s | 175.676 MB/s |
| AES-256-GCM-enc | 5.609 MB/s | 333.911 MB/s |
| AES-256-GCM-dec | 5.610 MB/s | 169.085 MB/s |
| CHACHA | 60.510 MB/s | 60.017 MB/s |
| CHA-POLY | 41.805 MB/s | 41.410 MB/s |
| MD5 | 156.310 MB/s | 154.421 MB/s |
| POLY1305 | 144.464 MB/s | 143.058 MB/s |
| SHA | 89.874 MB/s | 89.154 MB/s |
| SHA-256 | 38.805 MB/s | 533.139 MB/s |
| HMAC-MD5 | 156.301 MB/s | 154.083 MB/s |
| HMAC-SHA | 89.859 MB/s | 89.045 MB/s |
| HMAC-SHA256 | 38.814 MB/s | 532.316 MB/s |
| RSA, 2048, public | 171.995 Ops/s | 171.355 Ops/s |
| RSA, 2048, private | 13.716 Ops/s | 13.686 Ops/s |
| DH, 2048, key generation | 50.831 Ops/s | 50.575 Ops/s |
| DH, 2048, agree | 41.826 Ops/s | 41.596 Ops/s |
Return to top of page
Platform:
AVX1: 1.8GHz, Intel Core i5
AVX2: Intel Broadwell
Benchmark:
Crypto Benchmarks:
- AVX2: SHA-256 50 megs took 0.320 seconds, 156.118 MB/s
Cycles per byte = 9.75 = 47% - AVX1: SHA-256 50 megs took 0.272 seconds, 184.068 MB/s
Cycles per byte = 11.89 = 39% - Normal: SHA-256 50 megs took 0.376 seconds, 132.985 MB/s
Cycles per byte = 16.46 - AVX2: SHA-384 50 megs took 0.226 seconds, 221.318 MB/s
Cycles per byte = 6.88 = 42% - AVX1: SHA-384 50 megs took 0.192 seconds, 260.975 MB/s
Cycles per byte = 8.39 = 9% - Normal: SHA-384 50 megs took 0.209 seconds, 239.743 MB/s
Cycles per byte = 9.13 - AVX2: SHA-512 50 megs took 0.224 seconds, 223.120 MB/s
Cycles per byte = 6.82 = 75% - AVX1: SHA-512 50 megs took 0.188 seconds, 266.126 MB/s
Cycles per byte = 8.22 = 50% - Normal: SHA-512 50 megs took 0.281 seconds, 177.997 MB/s
Cycles per byte = 12.29
Reference
Return to top of page
Platform:
Atmel SAMD21
ARM Cortex M0
48 MHz
Benchmark:
TLS Establishment Times:
Hardware accelerated ATECC508A: 2.342 seconds average
Software only: 13.422 seconds average
The TLS connection establishment time is 5.73 times faster with the ATECC508A.
Software only implementation (SAMD21 48Mhz Cortex-M0, Fast Math TFM-ASM):
ECC 256 key generation 3123.000 milliseconds, avg over 5 iterations
EC-DHE key agreement 3117.000 milliseconds, avg over 5 iterations
EC-DSA sign time 1997.000 milliseconds, avg over 5 iterations
EC-DSA verify time 5057.000 milliseconds, avg over 5 iterations
ATECC508A HW accelerated implementation:
ECC 256 key generation 144.400 milliseconds, avg over 5 iterations
EC-DHE key agreement 134.200 milliseconds, avg over 5 iterations
EC-DSA sign time 293.400 milliseconds, avg over 5 iterations
EC-DSA verify time 208.400 milliseconds, avg over 5 iterations
For reference the benchmarks for RNG, AES, MD5, SHA and SHA256 are:
RNG 25 kB took 0.784 seconds, 0.031 MB/s (coming from the ATECC508A)
AES 25 kB took 0.177 seconds, 0.138 MB/s
MD5 25 kB took 0.050 seconds, 0.488 MB/s
SHA 25 kB took 0.141 seconds, 0.173 MB/s
SHA-256 25 kB took 0.352 seconds, 0.069 MB/s
Reference
Microchip Hardware-TLS Platform
wolfSSL Microchip ATECC508A Overview and Examples
Return to top of page
Platform:
STM32F221G-EVAL
ARM Cortex M3
120MHz
1 MB FLASH
128 KB SRAM
Benchmark:
Crypto Benchmarks:
Software Crypto: wolfCrypt Benchmark, Normal Big Integer Math Library
AES 1024 kB took 0.822 seconds, 1.22 MB/s
ARC4 1024 KB took 0.219 seconds, 4.57 MB/s
DES 1024 KB took 1.513 seconds, 0.66 MB/s
3DES 1024 KB took 3.986 seconds, 0.25 MB/s
MD5 1024 KB took 0.119 seconds, 8.40 MB/s
SHA 1024 KB took 0.279 seconds, 3.58 MB/s
SHA-256 1024 KB took 0.690 seconds, 1.45 MB/s
RSA 2048 encryption took 111.17 milliseconds, avg over 100 iterations
RSA 2048 decryption took 1204.77 milliseconds, avg over 100 iterations
DH 2048 key generation 467.90 milliseconds, avg over 100 iterations
DH 2048 key agreement 538.94 milliseconds, avg over 100 iterations
STM32F2 Hardware Crypto: wolfCrypt Benchmark, Normal Big Integer Math Library
AES 1024 kB took 0.105 seconds, 9.52 MB/s
ARC4 1024 KB took 0.219 seconds, 4.57 MB/s
DES 1024 KB took 0.125 seconds, 8.00 MB/s
3DES 1024 KB took 0.141 seconds, 7.09 MB/s
MD5 1024 KB took 0.045 seconds, 22.22 MB/s
SHA 1024 KB took 0.047 seconds, 21.28 MB/s
SHA-256 1024 KB took 0.690 seconds, 1.45 MB/s
RSA 2048 encryption took 111.09 milliseconds, avg over 100 iterations
RSA 2048 decryption took 1204.88 milliseconds, avg over 100 iterations
DH 2048 key generation 467.56 milliseconds, avg over 100 iterations
DH 2048 key agreement 542.11 milliseconds, avg over 100 iterations
Reference
Return to top of page
Platform:
Texas Instruments
Tiva C Series TM4C1294XL Connected Launchpad
(www.ti.com)
ARM Cortex-M4
120 MHz
1 MB FLASH
256 KB SRAM
6 KB EEPROM
Benchmark:
Crypto Benchmarks:
AES 25 kB took 0.038 seconds, 0.642 MB/s
Camellia 25 kB took 0.032 seconds, 0.763 MB/s
ARC4 25 kB took 0.006 seconds, 4.069 MB/s
RABBIT 25 kB took 0.005 seconds, 4.883 MB/s
CHACHA 25 kB took 0.007 seconds, 3.488 MB/s
3DES 25 kB took 0.164 seconds, 0.149 MB/s
MD5 25 kB took 0.003 seconds, 8.138 MB/s
POLY1305 25 kB took 0.004 seconds, 6.104 MB/s
SHA 25 kB took 0.006 seconds, 4.069 MB/s
SHA-256 25 kB took 0.014 seconds, 1.744 MB/s
SHA-512 25 kB took 0.042 seconds, 0.581 MB/s
RSA 2048 encryption took 88.000 milliseconds, avg over 1 iterations
RSA 2048 decryption took 1456.000 milliseconds, avg over 1 iterations
DH 2048 key generation 661.000 milliseconds, avg over 1 iterations
DH 2048 key agreement 665.000 milliseconds, avg over 1 iterations
ECC 256 key generation 130.400 milliseconds, avg over 5 iterations
EC-DHE key agreement 118.000 milliseconds, avg over 5 iterations
EC-DSA sign time 136.800 milliseconds, avg over 5 iterations
EC-DSA verify time 253.800 milliseconds, avg over 5 iterations
Reference
Return to top of page
Platform:
Freescale TWR-K70F120M
(www.freescale.com)
Freescale Kinetis K70
120 MHz
2 GB FLASH
1 GB RAM
Benchmark:
Crypto Benchmarks:
AES 5120 kB took 9.059 seconds, 0.55 MB/s
ARC4 5120 kB took 2.190 seconds, 2.28 MB/s
DES 5120 kB took 18.453 seconds, 0.27 MB/s
MD5 5120 kB took 1.396 seconds, 3.58 MB/s
SHA 5120 kB took 3.635 seconds, 1.38 MB/s
SHA-256 5120 kB took 9.145 seconds, 0.55 MB/s
RSA 2048 encryption took 73.99 milliseconds, avg over 100 iterations
RSA 2048 decryption took 1359.09 milliseconds, avg over 100 iterations
DH 2048 key generation 536.75 milliseconds, avg over 100 iterations
DH 2048 key agreement 540.99 milliseconds, avg over 100 iterations
Build Details
- MQX RTOS, using the fastmath library with TFM_TIMING_RESISTANT
- FREESCALE_MQX define set in <cyassl_root>/cyassl/ctaocrypt/settings.h
- CodeWarrior 10.2 IDE and compiler, optimizing for speed
Reference
Freescale TWR-K70F120M: http://www.freescale.com/webapp/sps/site/prod_summary.jsp?code=TWR-K70F120M
Return to top of page
Platform:
Apple TV 2
(www.apple.com)
Apple A4 (ARM Cortex-A8)
1 GHz
8 GB FLASH
256 MB RAM
Benchmark:
Crypto Benchmarks:
AES 5 megs took 0.500 seconds, 9.99 MB/s
ARC4 5 megs took 0.174 seconds, 28.66 MB/s
RABBIT 5 megs took 0.126 seconds, 39.56 MB/s
3DES 5 megs took 2.196 seconds, 2.28 MB/s
MD5 5 megs took 0.163 seconds, 30.73 MB/s
SHA 5 megs took 0.137 seconds, 36.61 MB/s
SHA-256 5 megs took 0.309 seconds, 16.20 MB/s
RSA 1024 encryption took 1.12 milliseconds, avg over 100 iterations
RSA 1024 decryption took 17.81 milliseconds, avg over 100 iterations
DH 1024 key generation 11.90 milliseconds, avg over 100 iterations
DH 1024 key agreement 11.22 milliseconds, avg over 100 iterations
Build Details
Complete build, compiled with fastmath (–enable-fastmath)
Reference
Blog Post: Running CyaSSL on the Apple TV 2
Return to top of page
Benchmark:
Memory Usage:
RAM Usage: 2.0 kB
Flash Usage*: 64 kB
* This included our test driver code, about 3kB.
Crypto Benchmarks:
public RSA: 10 milliseconds
private RSA: 165 milliseconds
Build Details
– Complete build, everything but SHA-512, DH, DSA, and HC-128
– Compiled using mbed cloud compiler
Reference
http://mbed.org/users/toddouska/libraries/CyaSSL/lm43pv
http://mbed.org/users/toddouska/programs/cyassl-client/lm394s
Return to top of page
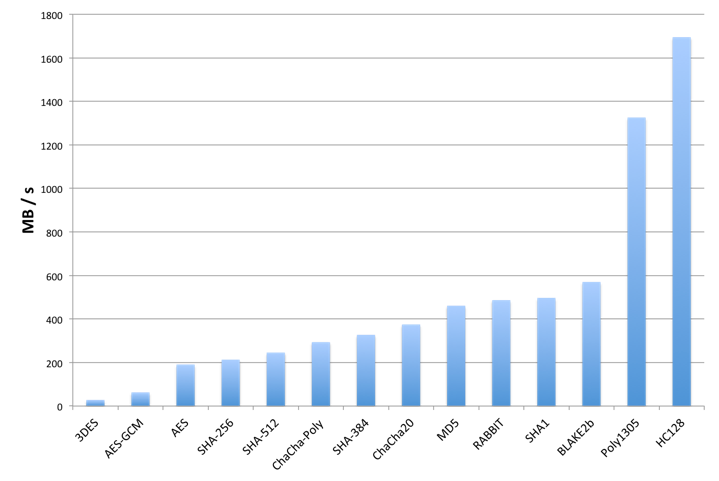
Relative Cipher Performance
Although the performance of individual ciphers and algorithms will depend on the host platform, the following graph shows relative performance between some of wolfCrypt’s algorithms. These tests were conducted on a Macbook Pro (OS X 10.6.8) running a 2.2 GHz Intel Core i7.
 Return to top of page
Return to top of page
If you want to use only a subset of ciphers, you can customize which specific cipher suites and/or ciphers wolfSSL uses when making an SSL/TLS connection. For example, to force 128-bit AES, add the following line after the call to wolfSSL_CTX_new (SSL_CTX_new):
wolfSSL_CTX_set_cipher_list(ctx, “AES128-SHA”);
Post-Quantum Kyber Benchmarks (Linux)
Platform:
11th Gen Intel® Core™ i7-1185G7 @ 3.00GHz × 8
Benchmark:
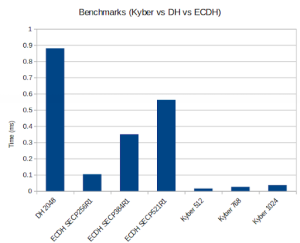
Notes:
- – Only 1 core is used
- – Conventional algorithms are present for comparison purposes
- – The wolfSSL configuration used was:
./configure --disable-psk --disable-shared --enable-intelasm --enable-aesni --enable-sp --enable-sp-math --enable-sp-asm --enable-kyber=wolfssl,all 'CFLAGS=-Os -DECC_USER_CURVES -DHAVE_ECC256 -DHAVE_ECC384'
wolfSSL Server Benchmark on TLS13-AES256-GCM-SHA384 with group ECC_SECP384R1:
Total : 5505024 bytes
Num Conns : 22
Rx Total : 953.534 ms
Tx Total : 6.757 ms
Rx : 2.753 MB/s
Tx : 388.471 MB/s
Connect : 55.076 ms
Connect Avg : 2.503 ms
wolfSSL Client Benchmark on TLS13-AES256-GCM-SHA384 with group ECC_SECP384R1:
Total : 5505024 bytes
Num Conns : 22
Rx Total : 956.304 ms
Tx Total : 5.627 ms
Rx : 2.745 MB/s
Tx : 466.488 MB/s
Connect : 54.827 ms
Connect Avg : 2.492 ms
wolfSSL Server Benchmark on TLS13-AES256-GCM-SHA384 with group ECC_SECP521R1:
Total : 5505024 bytes
Num Conns : 22
Rx Total : 948.864 ms
Tx Total : 6.542 ms
Rx : 2.766 MB/s
Tx : 401.226 MB/s
Connect : 59.490 ms
Connect Avg : 2.704 ms
wolfSSL Client Benchmark on TLS13-AES256-GCM-SHA384 with group ECC_SECP521R1:
Total : 5505024 bytes
Num Conns : 22
Rx Total : 951.101 ms
Tx Total : 5.791 ms
Rx : 2.760 MB/s
Tx : 453.275 MB/s
Connect : 59.598 ms
Connect Avg : 2.709 ms
wolfSSL Server Benchmark on TLS13-AES256-GCM-SHA384 with group KYBER_LEVEL1:
Total : 5505024 bytes
Num Conns : 22
Rx Total : 954.452 ms
Tx Total : 7.089 ms
Rx : 2.750 MB/s
Tx : 370.297 MB/s
Connect : 47.349 ms
Connect Avg : 2.152 ms
wolfSSL Client Benchmark on TLS13-AES256-GCM-SHA384 with group KYBER_LEVEL1:
Total : 5505024 bytes
Num Conns : 22
Rx Total : 956.931 ms
Tx Total : 6.189 ms
Rx : 2.743 MB/s
Tx : 424.149 MB/s
Connect : 46.129 ms
Connect Avg : 2.097 ms
wolfSSL Server Benchmark on TLS13-AES256-GCM-SHA384 with group KYBER_LEVEL3:
Total : 5767168 bytes
Num Conns : 23
Rx Total : 958.702 ms
Tx Total : 7.431 ms
Rx : 2.868 MB/s
Tx : 370.070 MB/s
Connect : 48.699 ms
Connect Avg : 2.117 ms
wolfSSL Client Benchmark on TLS13-AES256-GCM-SHA384 with group KYBER_LEVEL3:
Total : 5767168 bytes
Num Conns : 23
Rx Total : 961.281 ms
Tx Total : 6.032 ms
Rx : 2.861 MB/s
Tx : 455.903 MB/s
Connect : 47.497 ms
Connect Avg : 2.065 ms
wolfSSL Server Benchmark on TLS13-AES256-GCM-SHA384 with group KYBER_LEVEL5:
Total : 5767168 bytes
Num Conns : 23
Rx Total : 967.680 ms
Tx Total : 6.709 ms
Rx : 2.842 MB/s
Tx : 409.906 MB/s
Connect : 51.945 ms
Connect Avg : 2.258 ms
wolfSSL Client Benchmark on TLS13-AES256-GCM-SHA384 with group KYBER_LEVEL5:
Total : 5767168 bytes
Num Conns : 23
Rx Total : 969.719 ms
Tx Total : 6.183 ms
Rx : 2.836 MB/s
Tx : 444.774 MB/s
Connect : 49.456 ms
Connect Avg : 2.150 ms
wolfSSL Server Benchmark on TLS13-AES256-GCM-SHA384 with group P256_KYBER_LEVEL1:
Total : 2883584 bytes
Num Conns : 12
Rx Total : 494.597 ms
Tx Total : 2.225 ms
Rx : 2.780 MB/s
Tx : 618.065 MB/s
Connect : 540.056 ms
Connect Avg : 45.005 ms
wolfSSL Client Benchmark on TLS13-AES256-GCM-SHA384 with group P256_KYBER_LEVEL1:
Total : 2883584 bytes
Num Conns : 12
Rx Total : 495.337 ms
Tx Total : 2.282 ms
Rx : 2.776 MB/s
Tx : 602.567 MB/s
Connect : 538.472 ms
Connect Avg : 44.873 ms
wolfSSL Server Benchmark on TLS13-AES256-GCM-SHA384 with group P384_KYBER_LEVEL3:
Total : 2883584 bytes
Num Conns : 12
Rx Total : 503.707 ms
Tx Total : 3.427 ms
Rx : 2.730 MB/s
Tx : 401.222 MB/s
Connect : 526.276 ms
Connect Avg : 43.856 ms
wolfSSL Client Benchmark on TLS13-AES256-GCM-SHA384 with group P384_KYBER_LEVEL3:
Total : 2883584 bytes
Num Conns : 12
Rx Total : 505.002 ms
Tx Total : 3.302 ms
Rx : 2.723 MB/s
Tx : 416.462 MB/s
Connect : 523.324 ms
Connect Avg : 43.610 ms
wolfSSL Server Benchmark on TLS13-AES256-GCM-SHA384 with group P521_KYBER_LEVEL5:
Total : 2883584 bytes
Num Conns : 12
Rx Total : 503.258 ms
Tx Total : 3.171 ms
Rx : 2.732 MB/s
Tx : 433.556 MB/s
Connect : 537.391 ms
Connect Avg : 44.783 ms
wolfSSL Client Benchmark on TLS13-AES256-GCM-SHA384 with group P521_KYBER_LEVEL5:
Total : 2883584 bytes
Num Conns : 12
Rx Total : 504.367 ms
Tx Total : 3.316 ms
Rx : 2.726 MB/s
Tx : 414.636 MB/s
Connect : 532.820 ms
Connect Avg : 44.402 ms
Post-Quantum Kyber Benchmarks (ARM Cortex-M4)
Platform:
STM NUCLEO-F446ZE
Benchmark:
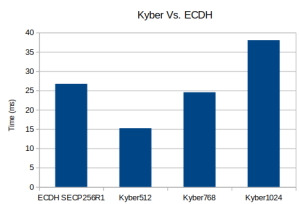
Notes:
- – The HCLK in the project was set to 168MHz
- – Only 1 core used
– wolfSSL Math Configuration set to “Single Precision ASM Cortex-M3+ Math”
– Optimization flag: -Ofast
– Conventional algorithms are present for comparison purposes
RSA 2048 public 82 ops took 1.020 sec, avg 12.439 ms, 80.392 ops/sec RSA 2048 private 4 ops took 1.827 sec, avg 456.750 ms, 2.189 ops/sec DH 2048 key gen 5 ops took 1.181 sec, avg 236.200 ms, 4.234 ops/sec DH 2048 agree 6 ops took 1.419 sec, avg 236.500 ms, 4.228 ops/sec ECC SECP256R1 key gen 118 ops took 1.012 sec, avg 8.576 ms, 116.601 ops/sec ECDHE SECP256R1 agree 56 ops took 1.016 sec, avg 18.143 ms, 55.118 ops/sec KYBER512 128 key gen 232 ops took 1.004 sec, avg 4.328 ms, 231.076 ops/sec KYBER512 128 encap 192 ops took 1.008 sec, avg 5.250 ms, 190.476 ops/sec KYBER512 128 decap 178 ops took 1.004 sec, avg 5.640 ms, 177.291 ops/sec KYBER768 192 key gen 146 ops took 1.008 sec, avg 6.904 ms, 144.841 ops/sec KYBER768 192 encap 118 ops took 1.008 sec, avg 8.542 ms, 117.063 ops/sec KYBER768 192 decap 110 ops took 1.000 sec, avg 9.091 ms, 110.000 ops/sec KYBER1024 256 key gen 92 ops took 1.011 sec, avg 10.989 ms, 90.999 ops/sec KYBER1024 256 encap 76 ops took 1.000 sec, avg 13.158 ms, 76.000 ops/sec KYBER1024 256 decap 72 ops took 1.000 sec, avg 13.889 ms, 72.000 ops/sec
Post-Quantum Kyber Benchmarks (MacOS)
Platform:
Apple MacBook Pro 18,3 with an Apple M1 Pro, 3.09 GHz processor
Benchmark:
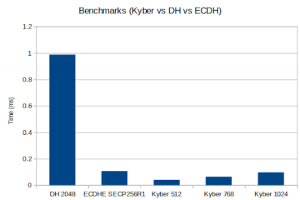
Notes:
- – Only 1 core is used
Math: Multi-Precision: Wolf(SP) no-dyn-stack word-size=64 bits=4096 sp_int.c Single Precision: ecc 256 384 521 rsa/dh 2048 3072 4096 asm sp_arm64.c wolfCrypt Benchmark (block bytes 1048576, min 1.0 sec each) DH 2048 key gen 3997 ops took 1.000 sec, avg 0.250 ms, 3996.812 ops/sec DH 2048 agree 4100 ops took 1.001 sec, avg 0.244 ms, 4097.522 ops/sec KYBER512 128 key gen 96100 ops took 1.001 sec, avg 0.010 ms, 96037.765 ops/sec KYBER512 128 encap 78000 ops took 1.000 sec, avg 0.013 ms, 77970.220 ops/sec KYBER512 128 decap 58900 ops took 1.001 sec, avg 0.017 ms, 58867.158 ops/sec KYBER768 192 key gen 58200 ops took 1.000 sec, avg 0.017 ms, 58192.314 ops/sec KYBER768 192 encap 48700 ops took 1.001 sec, avg 0.021 ms, 48664.334 ops/sec KYBER768 192 decap 38100 ops took 1.001 sec, avg 0.026 ms, 38059.656 ops/sec KYBER1024 256 key gen 37800 ops took 1.003 sec, avg 0.027 ms, 37704.299 ops/sec KYBER1024 256 encap 32600 ops took 1.001 sec, avg 0.031 ms, 32566.427 ops/sec KYBER1024 256 decap 26000 ops took 1.001 sec, avg 0.039 ms, 25967.020 ops/sec ECC [ SECP256R1] 256 key gen 84100 ops took 1.001 sec, avg 0.012 ms, 84013.469 ops/sec ECDHE [ SECP256R1] 256 agree 24400 ops took 1.004 sec, avg 0.041 ms, 24300.995 ops/sec
Platform:
Raspberry Pi Pico-W
ARM Cortext M0+, 125MHz
Benchmark:
wolfSSL/wolfCrypt v5.6.3
Configuration Options
– SP Math:
Enable: WOLFSSL_HAVE_SP_RSA, WOLFSSL_HAVE_SP_DH, WOLFSSL_HAVE_SP_ECC, WOLFSSL_SP_ARM_THUMB_ASM Disable: WOLFSSL_SP_SMALL, WOLFSSL_SP_ASM
– AES-GCM:
Enable: GCM_TABLE_4BIT Disable: GCM_SMALL
``` wolfCrypt Benchmark (block bytes 1024, min 1.0 sec each) RNG 475 KiB took 1.048 seconds, 453.220 KiB/s AES-128-CBC-enc 850 KiB took 1.027 seconds, 827.711 KiB/s AES-128-CBC-dec 825 KiB took 1.014 seconds, 813.327 KiB/s AES-192-CBC-enc 725 KiB took 1.002 seconds, 723.594 KiB/s AES-192-CBC-dec 700 KiB took 1.017 seconds, 688.524 KiB/s AES-256-CBC-enc 650 KiB took 1.005 seconds, 647.072 KiB/s AES-256-CBC-dec 625 KiB took 1.023 seconds, 610.908 KiB/s AES-128-GCM-enc 375 KiB took 1.008 seconds, 372.077 KiB/s AES-128-GCM-dec 375 KiB took 1.048 seconds, 357.974 KiB/s AES-192-GCM-enc 350 KiB took 1.031 seconds, 339.515 KiB/s AES-192-GCM-dec 325 KiB took 1.015 seconds, 320.354 KiB/s AES-256-GCM-enc 325 KiB took 1.035 seconds, 313.895 KiB/s AES-256-GCM-dec 325 KiB took 1.083 seconds, 300.044 KiB/s AES-128-GCM-enc-no_AAD 400 KiB took 1.020 seconds, 392.229 KiB/s AES-128-GCM-dec-no_AAD 400 KiB took 1.063 seconds, 376.324 KiB/s AES-192-GCM-enc-no_AAD 375 KiB took 1.053 seconds, 356.052 KiB/s AES-192-GCM-dec-no_AAD 350 KiB took 1.044 seconds, 335.173 KiB/s AES-256-GCM-enc-no_AAD 350 KiB took 1.067 seconds, 327.915 KiB/s AES-256-GCM-dec-no_AAD 325 KiB took 1.038 seconds, 312.985 KiB/s GMAC Table 4-bit 1 MiB took 1.001 seconds, 1.173 MiB/s CHACHA 3 MiB took 1.008 seconds, 2.615 MiB/s CHA-POLY 975 KiB took 1.001 seconds, 974.262 KiB/s POLY1305 2 MiB took 1.006 seconds, 1.625 MiB/s SHA 2 MiB took 1.004 seconds, 2.456 MiB/s SHA-256 1 MiB took 1.000 seconds, 1.025 MiB/s SHA-384 550 KiB took 1.032 seconds, 532.885 KiB/s SHA-512 525 KiB took 1.029 seconds, 510.002 KiB/s SHA-512/224 525 KiB took 1.009 seconds, 520.350 KiB/s SHA-512/256 525 KiB took 1.010 seconds, 519.658 KiB/s SHA3-224 575 KiB took 1.002 seconds, 573.882 KiB/s SHA3-256 550 KiB took 1.016 seconds, 541.124 KiB/s SHA3-384 425 KiB took 1.021 seconds, 416.388 KiB/s SHA3-512 300 KiB took 1.032 seconds, 290.658 KiB/s SHAKE128 675 KiB took 1.015 seconds, 665.093 KiB/s SHAKE256 550 KiB took 1.016 seconds, 541.122 KiB/s HMAC-SHA 2 MiB took 1.005 seconds, 2.429 MiB/s HMAC-SHA256 1 MiB took 1.008 seconds, 1.017 MiB/s HMAC-SHA384 525 KiB took 1.003 seconds, 523.222 KiB/s HMAC-SHA512 500 KiB took 1.008 seconds, 495.957 KiB/s RSA 2048 public 30 ops took 1.000 sec, avg 33.335 ms, 29.998 ops/sec RSA 2048 private 2 ops took 2.555 sec, avg 1277.379 ms, 0.783 ops/sec DH 2048 key gen 2 ops took 1.117 sec, avg 558.654 ms, 1.790 ops/sec DH 2048 agree 2 ops took 1.116 sec, avg 557.958 ms, 1.792 ops/sec ECC [ SECP256R1] 256 key gen 18 ops took 1.012 sec, avg 56.241 ms, 17.781 ops/sec ECDHE [ SECP256R1] 256 agree 10 ops took 1.058 sec, avg 105.786 ms, 9.453 ops/sec ECDSA [ SECP256R1] 256 sign 16 ops took 1.132 sec, avg 70.740 ms, 14.136 ops/sec ECDSA [ SECP256R1] 256 verify 10 ops took 1.171 sec, avg 117.119 ms, 8.538 ops/sec CURVE 25519 key gen 12 ops took 1.020 sec, avg 85.014 ms, 11.763 ops/sec CURVE 25519 agree 12 ops took 1.014 sec, avg 84.486 ms, 11.836 ops/sec ED 25519 key gen 26 ops took 1.011 sec, avg 38.891 ms, 25.713 ops/sec ED 25519 sign 24 ops took 1.041 sec, avg 43.392 ms, 23.046 ops/sec ED 25519 verify 10 ops took 1.062 sec, avg 106.162 ms, 9.420 ops/sec CURVE 448 key gen 4 ops took 1.226 sec, avg 306.396 ms, 3.264 ops/sec CURVE 448 agree 4 ops took 1.219 sec, avg 304.700 ms, 3.282 ops/sec ED 448 key gen 7 ops took 1.105 sec, avg 157.866 ms, 6.334 ops/sec ED 448 sign 8 ops took 1.305 sec, avg 163.081 ms, 6.132 ops/sec ED 448 verify 4 ops took 1.525 sec, avg 381.261 ms, 2.623 ops/sec ```
Benchmarking Notes
-
The processors native register size (32 vs 64-bit) can make a big difference when doing 1000+ bit public key operations.
-
fastmath (–enable-fastmath) reduces dynamic memory usage and speeds up public key operations. If you are having trouble building on a 32-bit platform with fastmath, disable shared libraries so that PIC isn’t hogging a register (also see notes in the README):
./configure –enable-fastmath –disable-shared
make clean
make*NOTE: doing a “make clean” is good practice with wolfSSL when switching configure options
-
By default, fastmath tries to use assembly optimizations if possible. If assembly optimizations don’t work, you can still use fastmath without them by adding TFM_NO_ASM to CFLAGS when building wolfSSL:
./configure –enable-fastmath CFLAGS=-DTFM_NO_ASM
-
Using fasthugemath can try to push fastmath even more for users who are not running on embedded platforms:
./configure –enable-fasthugemath
-
With the default wolfSSL build, we have tried to find a good balance between memory usage and performance. If you are more concerned about one of the two, please see Chapter 2 of the wolfSSL manual for additional wolfSSL configuration options.
-
Bulk Transfers: wolfSSL by default uses 128 byte I/O buffers since about 80% of SSL traffic falls within this size and to limit dynamic memory use. It can be configured to use 16K buffers (the maximum SSL size) if bulk transfers are required.
Publications and Flyers
Publications in relation to benchmarking our SSL/TLS and crypto libraries:
wolfSSL+NTRU: High-Performance SSL
This flyer details the performance gains that can be seen when using the wolfSSL embedded SSL library with Security Innovation’s NTRU cipher. NTRU is similar to the RSA public key algorithm but can offer anywhere from a 20-200X speed improvement.
wolfSSL Secure memcached Benchmarks
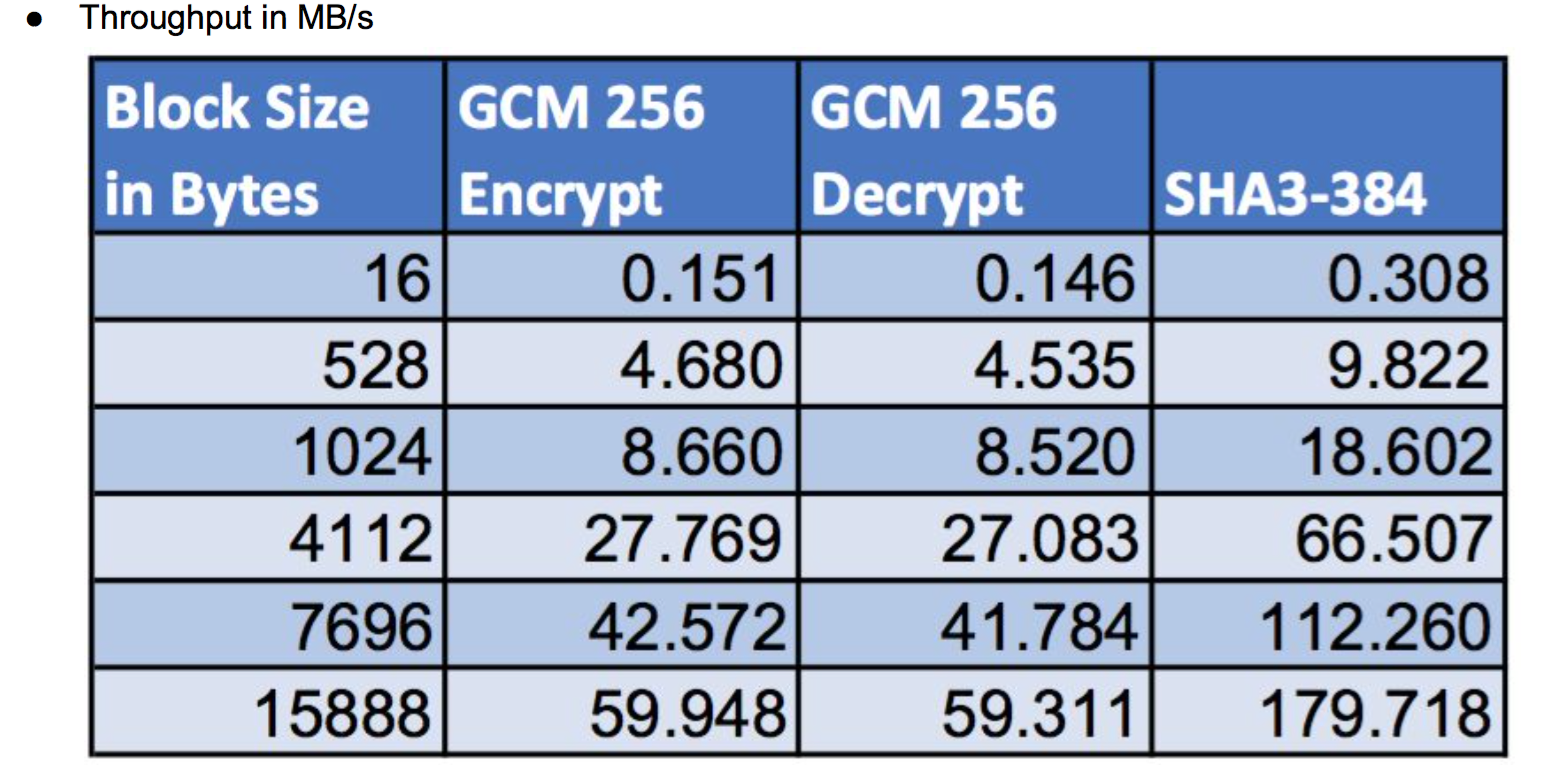
Because wolfSSL can offer fast encryption and low memory usage it can easily be leveraged onto high-volume servers supporting many thousands of connections. This flyer demonstrates memcached benchmarks using wolfSSL.


 Return to
Return to 
